可恶,太菜了
Web
nisc_easyweb
题解
dirsearch扫描得到robots.txt
- 访问
/api/record/,得到api_test.php
- 访问查看源代码,找到
hint
get参数得到flag
吃豆人吃豆魂
题解
- 查看源代码,在
index.js发现base64的flag
Misc
chechin_gift
题解
010查看附件,结尾存在base64
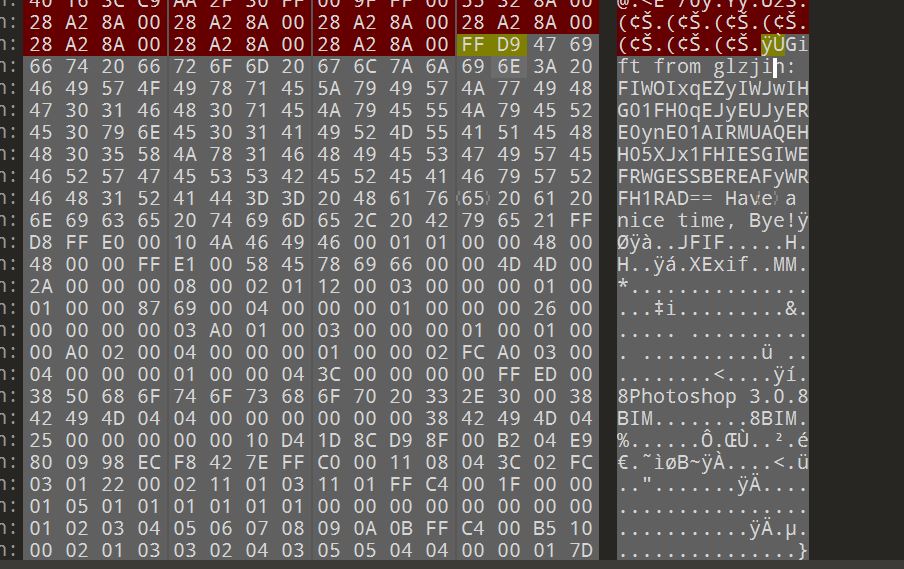
- 替换码表
- N-ZA-Mn-za-m0-9+/=
- base32
- DASCTF{722433fc22f2e79959da2208d84cbb40}
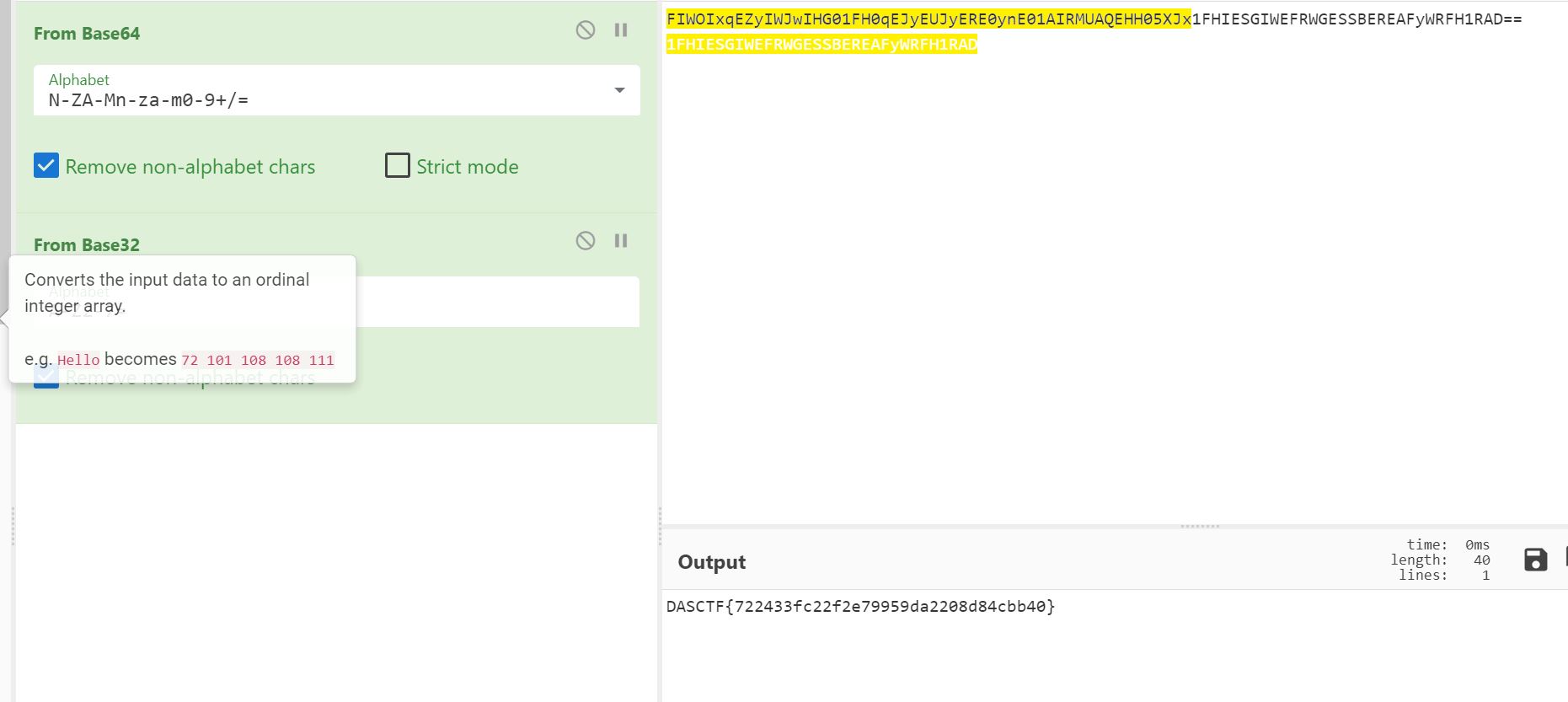
m4a
题解
- 打开音频文件,很明显是一串摩尔斯密码,转换为 MP3,拖入 Audacity 查看波形图
- 1000 01 00001 00011 1000 1010 0 0010 1010 00111 11111 00001
- BA43BCEFC204
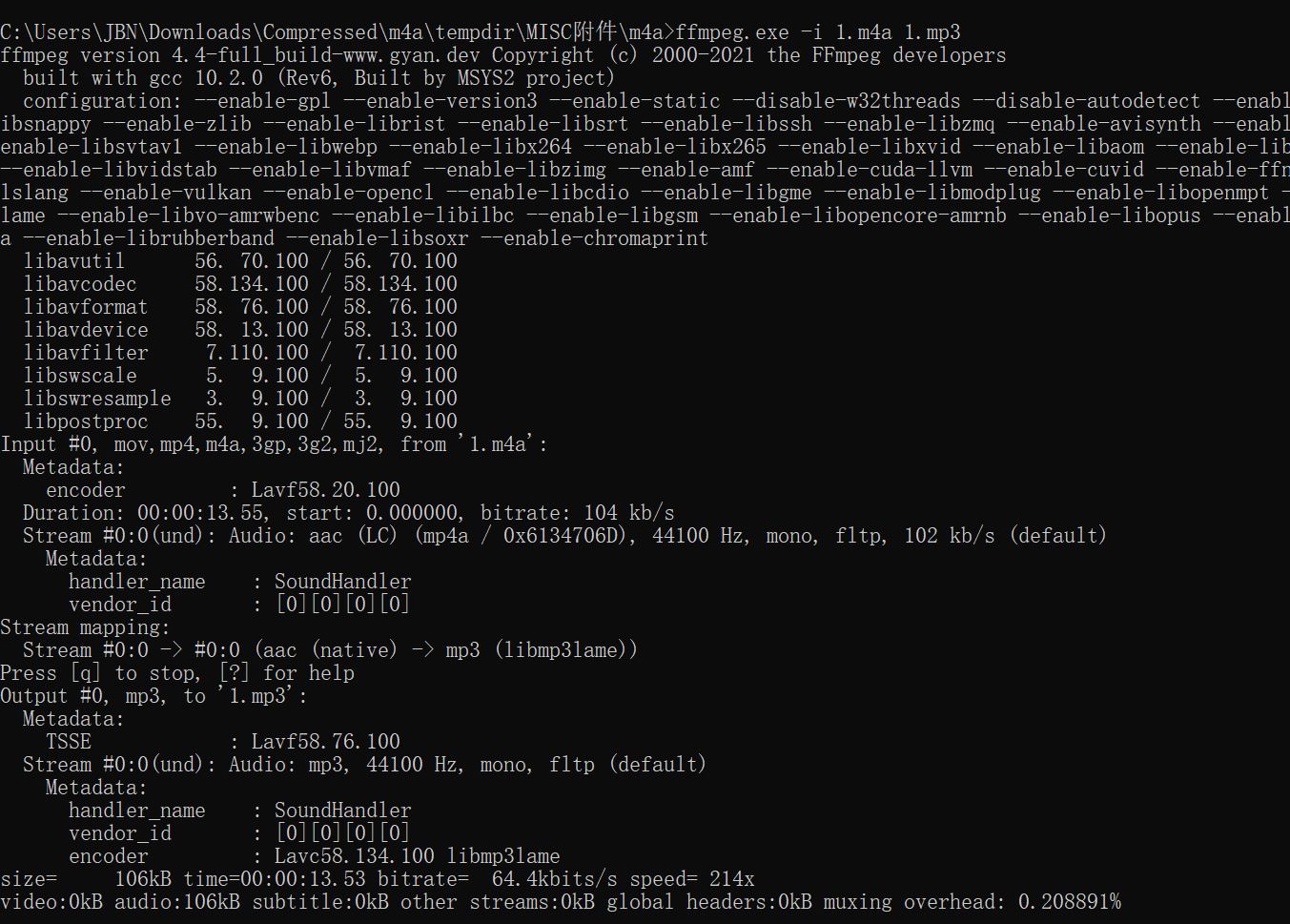
010查看m4a

- 文件结尾有倒置的 PK 文件,写脚本
with open('1.m4a', 'rb') as rb:
content = rb.read().hex()
a = content[::-2]
b = ' ' + content[::-1]
b = b[::2].replace(' ', '')
c = ''
for i in range(len(a)):
c += b[i]
c += a[i]
with open('1.txt', 'w') as w:
w.write(c)
- 导入
010,运行zip模板删除多余内容,用key解压 - 看 wp 知道这是
rot47+atbash- DASCTF{5e0f98a95f79829b7a484a54066cb08f}
Unkn0wnData
题解
010打开,结尾存在base64,magic爆破加密
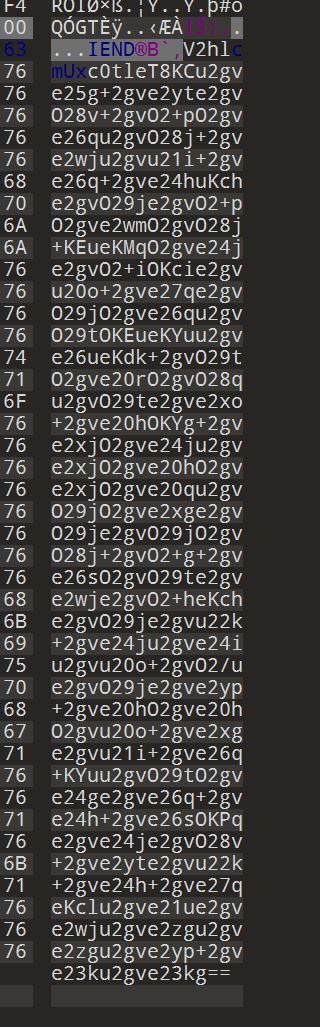
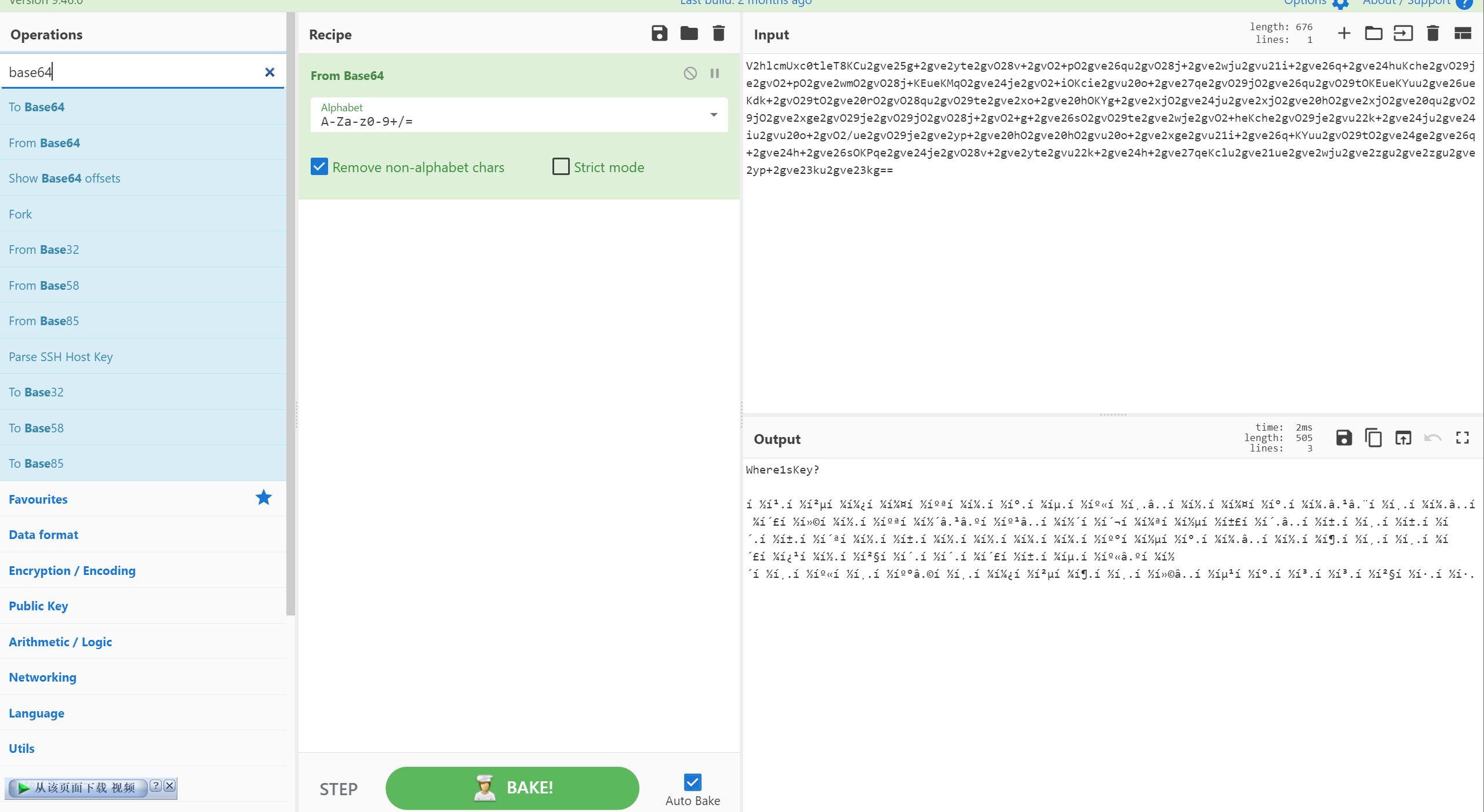
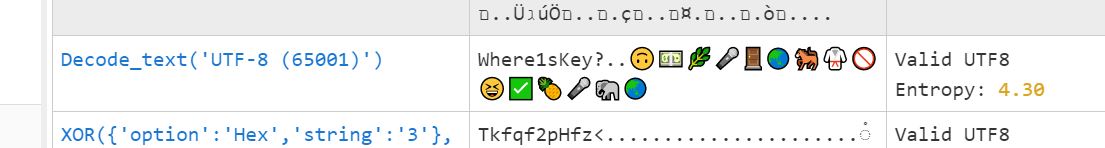
- 图片存在
LSB隐写,保存 bin
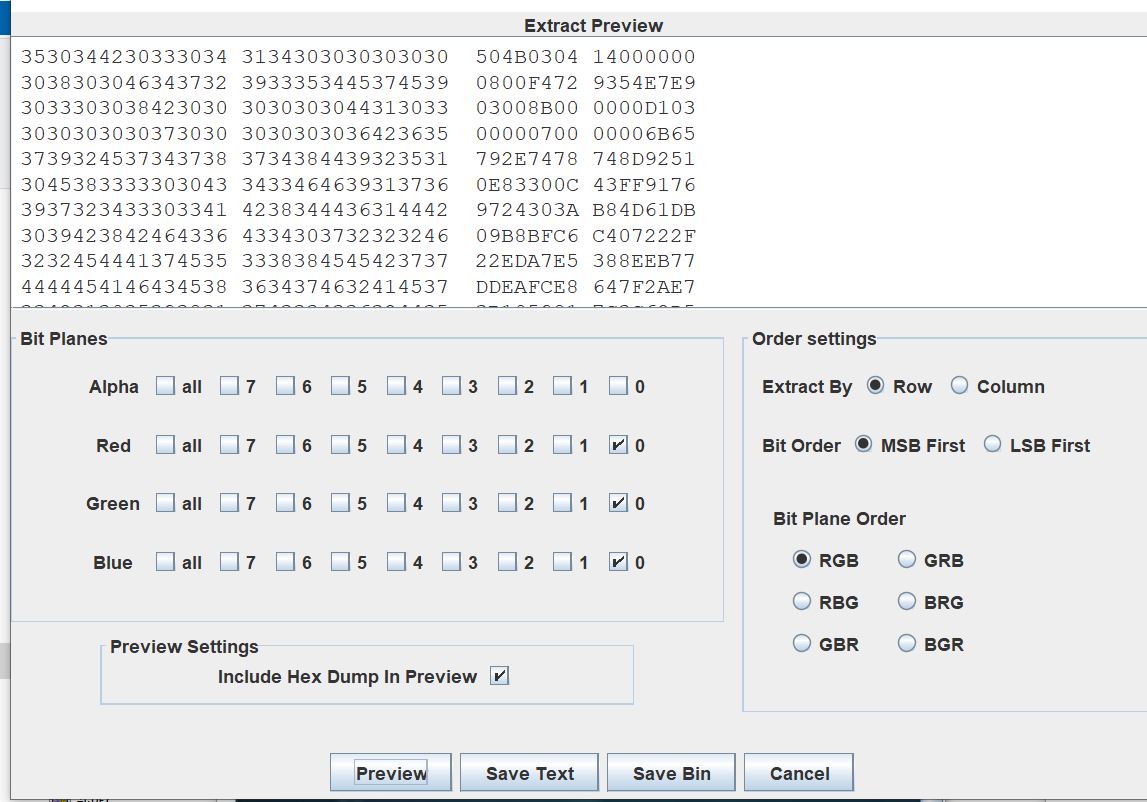
- 解压
zip得到
data:
0000100000000000
00000c0000000000
00000e0000000000
00002a0000000000
0000100000000000
0000040000000000
0000080000000000
00002a0000000000
0000160000000000
00000b0000000000
00000c0000000000
00001c0000000000
00002a0000000000
00002c0000000000
0200340000000000
00002a0000000000
0200090000000000
00000c0000000000
0000110000000000
0000070000000000
0200170000000000
00002a0000000000
0200170000000000
00000b0000000000
0000080000000000
0000120000000000
00002a0000000000
0200150000000000
0000080000000000
0000040000000000
00000f0000000000
00000a0000000000
00002a0000000000
02000e0000000000
0000080000000000
00001c0000000000
00000a0000000000
00002a0000000000
0000040000000000
0000110000000000
0000070000000000
00000f0000000000
00002a0000000000
0200100000000000
0000040000000000
00000e0000000000
0000080000000000
0000080000000000
00002a0000000000
02000c0000000000
0000170000000000
02001e0000000000
0000070000000000
00002a0000000000
- 键盘流量
- mik
maeshiy:FindTTheoRealgKeygandlMakeeIt!d mimashi FindTheRealKeyandMakeIt!
- mik
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
keys = open('key.txt')
output = ""
for line in keys:
k = line[1]
n = line[4:6]
if k == '0':
print(normalKeys[n], end='')
elif k == '2':
print(shiftKeys[n], end='')normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
keys = open('key.txt')
output = ""
for line in keys:
k = line[1]
n = line[4:6]
if n == '2a':
print(output[-1], end='')
if k == '0':
output += normalKeys[n]
elif k == '2':
output += shiftKeys[n]- key: Toggled
emoji-aes解码- https://aghorler.github.io/emoji-aes/#
- 手动解码
- U2FsdGVkX1+psEGiQ9Bl3PbdKi4mYKSHJfRIoCoRo/bepbG8tJvD+pzC53ApwRR3ekX4K0X6tZ9F2z6PxNVOOw==
import base64
from Crypto.Cipher import AES
import string
emojisInit=" 









