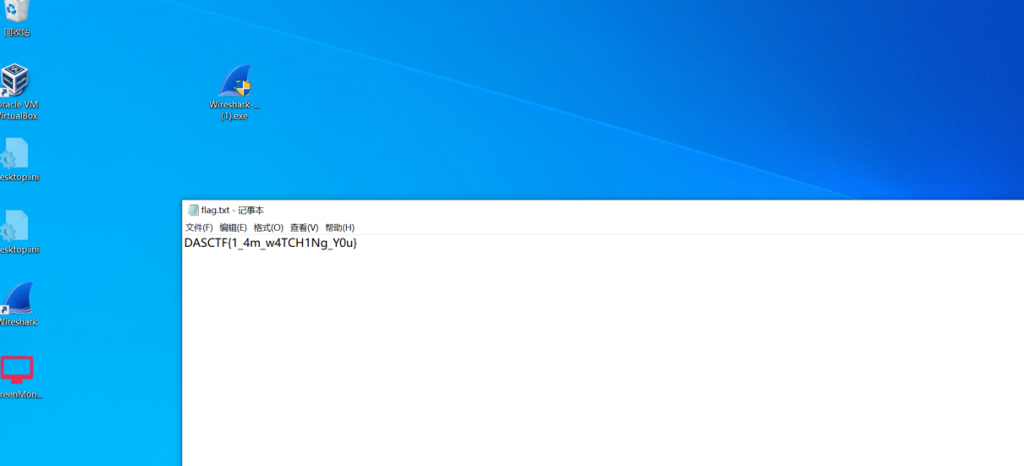
本文最后更新于 363 天前,其中的信息可能已经有所发展或是发生改变。
Misc
ez_minecraft
- 进入世界后,头顶有很多方块,大致能猜到一种方块儿对应一个数值
- 同时发现一个
file_encoder插件,从中可以发现decodeblocks指令
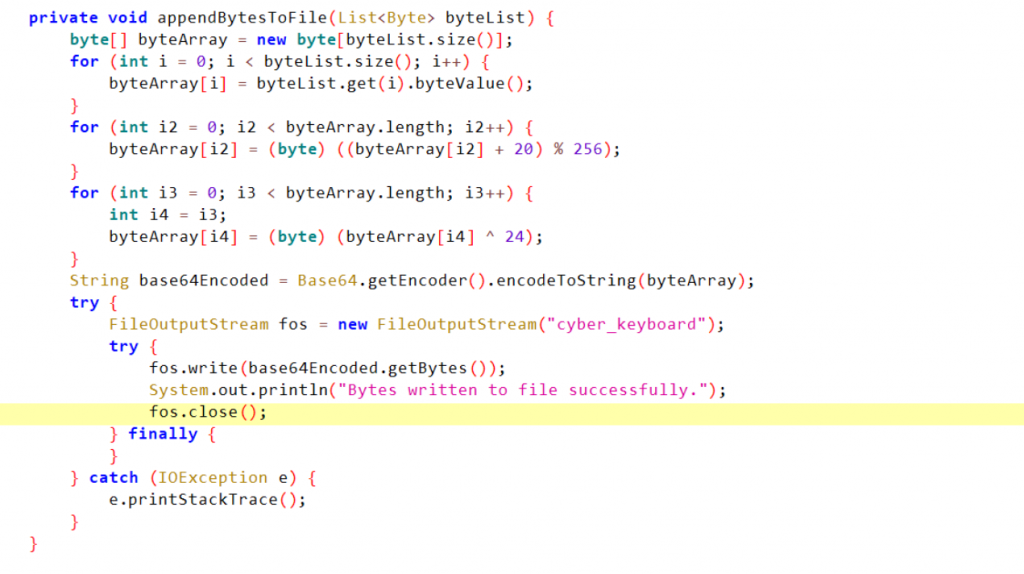
- 得到的
cyber_keyboard并不可逆,尝试修改插件,直接保存原始数据
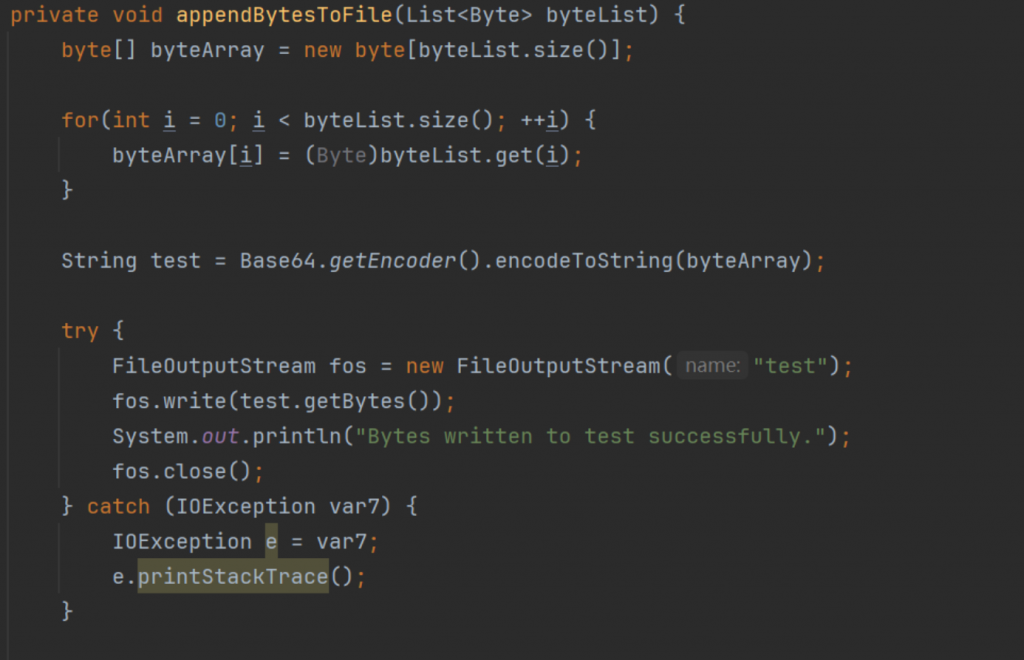
- 可以得到一个伪加密压缩包,得到一段USB流量,解密
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>","54":"/","55":"*","56":"-","57":"+","58":"<RET2>","59":"1","5a":"2","5b":"3","5c":"4","5d":"5","5e":"6","5f":"7","60":"8","61":"9","62":"0","bc":"A","bd":"B","be":"C","bf":"D","c0":"E","c1":"F"}
nums = []
keys = open('usbdata.txt')
for line in keys:
if len(line) != 19:
continue
nums.append(line[0:2]+line[6:8])
keys.close()
output = ""
flag = -1
for n in nums:
if n[2:4] in normalKeys:
output += normalKeys[n[2:4]]
print('output :' + output)55252542175525254217552525421750161550315087746536478215342755252542174782153427508774653655252542175525254217475315478147016549904603153445501615503147821534274782153427475315478147821534274782153427501615503147531547815293250167475315478155252542174753154781475315478147821534274753154781478215342747821534275293250167542255165447016549904782153427470165499047821534274753154781475315478147821534274782153427470165499052932501675422551654470165499047821534275525254217478215342748820539414782153427470165499047821534275293250167+6587+660E+53CB+5584+6CD5+6CBB+516C+6B63+6C11+4E3B+548C+8C10+6587+660E+516C+6B63+548C+8C10+548C+8C10+6CD5+6CBB+6587+660E+53CB+5584+6CD5+6CBB+516C+6B63+516C+6B63+548C+8C10+5BCC+5F3A+516C+6B63+516C+6B63+548C+8C10+6CD5+6CBB+548C+8C10+516C+6B63+548C+8C10+548C+8C10+548C+8C10+81EA+7531+516C+6B63+6C11+4E3B+516C+6B63+6587+660E+548C+8C10+5E73+7B49+548C+8C10+6587+660E+548C+8C10+7231+56FD+6CD5+6CBB+53CB+5584+6CD5+6CBB- 前半段
GBK,后半段Unicode
import libnum
import unicodedata
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>","54":"/","55":"*","56":"-","57":"+","58":"<RET2>","59":"1","5a":"2","5b":"3","5c":"4","5d":"5","5e":"6","5f":"7","60":"8","61":"9","62":"0","bc":"A","bd":"B","be":"C","bf":"D","c0":"E","c1":"F"}
nums = []
keys = open('usbdata.txt')
for line in keys:
if len(line) != 19:
continue
nums.append(line[0:2]+line[6:8]+line[2:4])
keys.close()
output = ""
tmp = ""
for n in nums:
if n[2:4] in normalKeys:
tmp += normalKeys [n[2:4]]
elif(n[4:6] == "00"):
if(tmp[0] != "+"):
output += libnum.n2s(int(tmp)).decode("gbk")
else:
output += unicodedata.lookup(unicodedata.name(chr(int(tmp[1:],16))))
tmp = ""
print(output)whyApple
- 附件为
Charles抓包的产物,打开后,根据题目描述尝试搜索与device/register相关的内容,找到过滤出一条流量
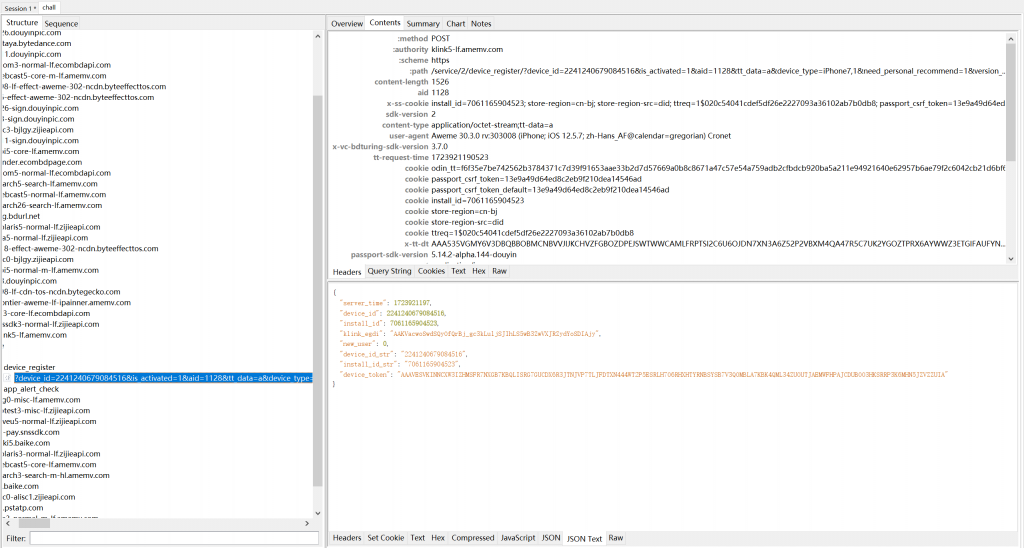
- 在Notes中,很容易看到题目中提及的
Post Headers相关内容
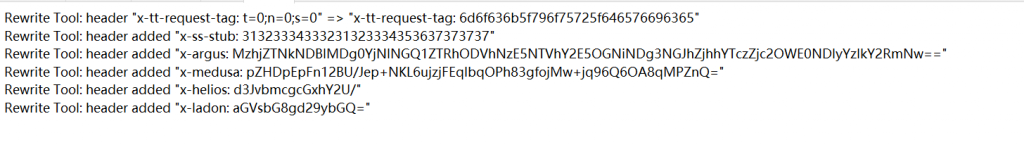
aGVsbG8gd29ybGQ= --> hello world
d3JvbmcgcGxhY2U/ --> wrong place?
MzhjZTNkNDBlMDg0YjNlNGQ1ZTRhODVhNzE5NTVhY2E5OGNiNDg3NGJhZjhhYTczZjc2OWE0NDIyYzlkY2RmNw== --> 38ce3d40e084b3e4d5e4a85a71955aca98cb4874baf8aa73f769a4422c9dcdf7- 还有个
x-medusa字段不能解码,猜测为flag,尝试常见的加密方式,爆破一下AES
from base64 import b64decode
from Crypto.Cipher import AES
a = [
b64decode(b"MzhjZTNkNDBlMDg0YjNlNGQ1ZTRhODVhNzE5NTVhY2E5OGNiNDg3NGJhZjhhYTczZjc2OWE0NDIyYzlkY2RmNw=="),
b64decode(b"pZHDpEpFn12BU/Jep+NKL6ujzjFEqlbqOPh83gfojMw+jq96Q6OA8qMPZnQ="),
b64decode(b"aGVsbG8gd29ybGQ="),
b64decode(b"d3JvbmcgcGxhY2U/"),
bytes.fromhex("31323334333231323334353637373737"),
bytes.fromhex("6d6f636b5f796f75725f646576696365"),
bytes.fromhex(b64decode(b"MzhjZTNkNDBlMDg0YjNlNGQ1ZTRhODVhNzE5NTVhY2E5OGNiNDg3NGJhZjhhYTczZjc2OWE0NDIyYzlkY2RmNw==").decode())
]
for x in a:
for y in a:
for z in a:
try:
aes = AES.new(key=x, mode=AES.MODE_CBC, iv=y)
result = aes.decrypt(z)
print(x, y, z, result)
except Exception as e:
passb'mock_your_device' b'1234321234567777' b'8\xce=@\xe0\x84\xb3\xe4\xd5\xe4\xa8Zq\x95Z\xca\x98\xcbHt\xba\xf8\xaas\xf7i\xa4B,\x9d\xcd\xf7' b'key_to_flag_838B6072\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c'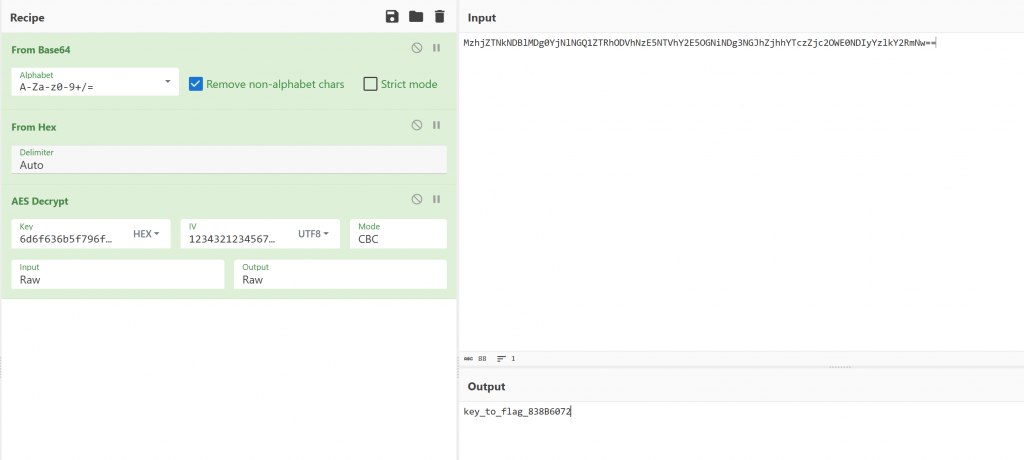
- RC4解出flag
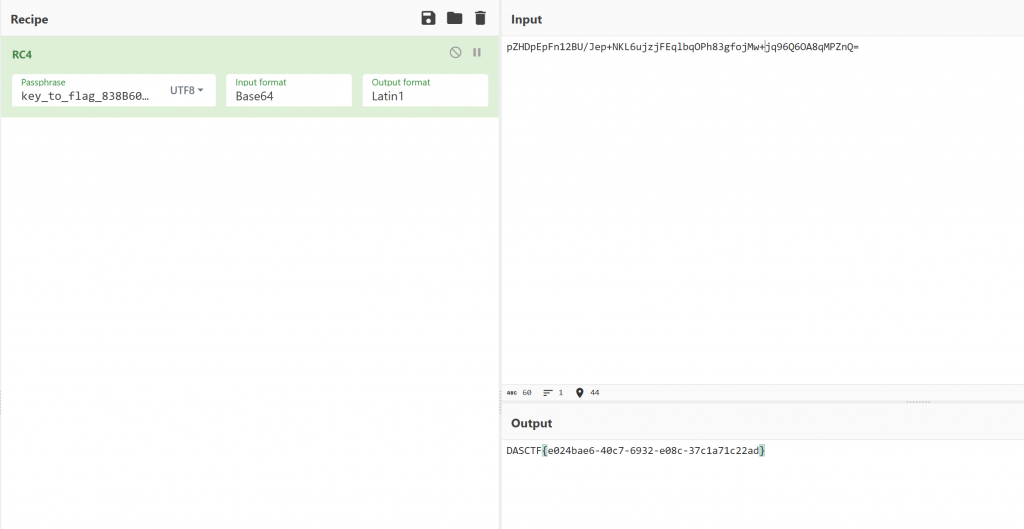
monitor
- 下载后得到一个exe和一个流量,首先过滤出所有相关流量
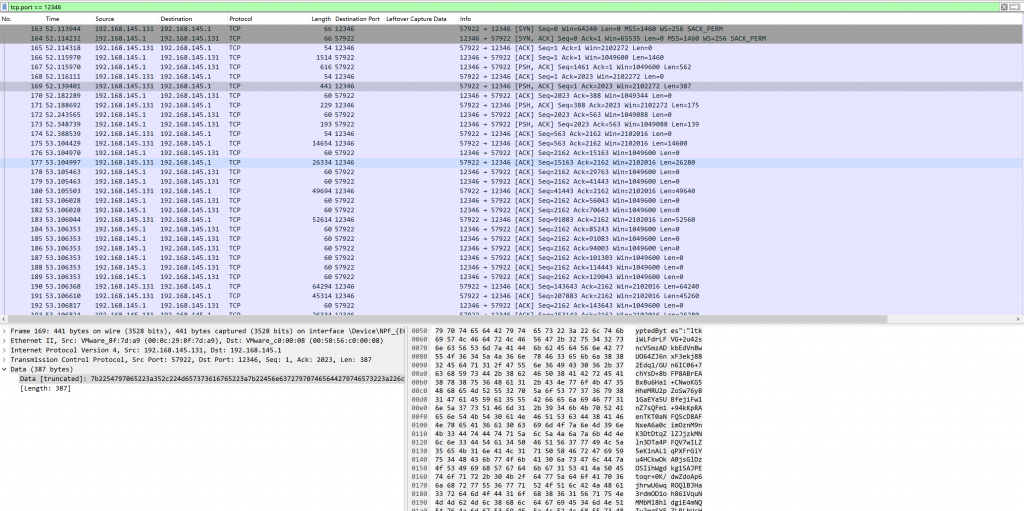
- 观察前几个包,在经历tcp握手后,由server端向client发送RSA公私钥的值(比赛时眼瞎只看到了公钥,没看见私钥)
{
"Message": {
"RsaPrivateKeyBytes": "MIIEpAIBAAKCAQEAxdeHjC8YvbE3rEoeluSJ5NP5obNGE1l86jWALgnLT9K8zi2YGvehzhrjloCnAOO9vGFmvK19ThiKS2lpwHFHmBhWgVputEPM7y8zr5zV+Ia9v2frsa2tFl1ODjW3KgljNXRw4UKDdHq/2t5QpKU7+sTiveXMZiOMFZc/7tq60DM+g2WEdXKBM7+lEkPh/wPZIcBL7T77iWyxVLdsrlvMoch8wiQ4ueenK4uF1f8TfFusSrYLI9BHGJpOQ+BjsBwPebM2vaVM8q+Zw+57M+eHKSy9NqLAwGtSGlydRI6dp2/UxilhXZoPfAFRiowLEJw5q8VvekiQEgJinEn3fmzxHQIDAQABAoIBACKzbhP5gsZq2g//JCRlS4Z2Y7eoASeNr6pI3gW1NBL5LKKhPqekPZ4v+zE/uYsfZv0uvF1ltK/JACDACYt2kw8rXajsmrRFnCFrzw4DXUhtIcT7zkxo4Q4mKXW2mDzoTp1mohHwn6wDh7k0+0IVtVKDzB1wvAxCOeTjlZQoi1HPC5Nt2yaoqRAIggM5LKBa2bDSAt5OPnMjP+GJS1EUlV/4PZRREUiIfMRZd+srC3DHtmlUnPF2Z8WvYbSFmY5dUpMSFqLfq/YZ07FCGayUflL4lzUw2r/JQWgR4gFrCkmS4/fdjNl5qw7OuWCAR/C6NpBDWJwTt017XqJuEsZ3UyUCgYEA/+WsJz1e7SomQaSQ/jPMpK/8tahTg1/TpnXRsFZidOPXOtg8IEdOuVscw2FTI15QC295qOZcN/X/7aGyvslvbp7lwBpAQA9opUm54UpDtXipqW77FPwEFSFKTEwWktrX6OCkUycgX+9fMa+V+fQ8kR220AdxYUV2m3DEb9lJD78CgYEAxeviVDuIWVbSHEezeOIkyT3E11B/fCPyovBU0xLTfrP+/HYyWrvT+9koT9ZZ4TMy9DEcTtzszglM3gTUfk6XZ+ZvcZVsmo5MJgy6YcaVFAA4YLrCSR3dLcFBTjPL8SE9ZuFG3Db/kH5c2+FtYfPnl2Ve7uw65uILXQhztXdCtiMCgYEAoPnPKUQfEhygwkyO9YqKYtNeqrwABTXkA+Q8C6zb9OJbQ+ZBNKEG8e1SE8qGrUooGnl+0/RN8NosrEU7F2/KTJFiwE0DPAk1cD0H1KSOIXuNZ0usYVAEFXLCtWpsDOfkSNgAJ1sGr7L6dFwbgYjWDQffN9Bmz6UN7syqlh3fKysCgYBHMwxAcQoj2W/MbJ7Lpc7F9kqRiovSBLyMkRhythsPQYFBIOQMb/VabExsLBg5Q0nZPrGITUGC/SWB2Qr4RR2Caws8ORzQnNAYAAwskFugzlN5uLWbx/qBMzxi/Y8oN2T3VaNAJSjauhp9nyLSUgPGGtmD6cdmt3qPBTNa3IRLMQKBgQCMvXMuGZjedrf7tat9gMDJgYnZey8e7xSuC9H6K4Ls5ammtmyBdrmWhyZiB9d/+88C/Wr3LjqfGyeiBbJoVMqO0tl4INH1FXdL1bItL2Qw5A9r6fqx1E3Cya84hNRNECa/+TVHYjRqc6zt308Q9/cq4ccuQlzOXLjn5jD+DvRQWg==",
"RsaPublicKeyBytes": "MIIBCgKCAQEAxdeHjC8YvbE3rEoeluSJ5NP5obNGE1l86jWALgnLT9K8zi2YGvehzhrjloCnAOO9vGFmvK19ThiKS2lpwHFHmBhWgVputEPM7y8zr5zV+Ia9v2frsa2tFl1ODjW3KgljNXRw4UKDdHq/2t5QpKU7+sTiveXMZiOMFZc/7tq60DM+g2WEdXKBM7+lEkPh/wPZIcBL7T77iWyxVLdsrlvMoch8wiQ4ueenK4uF1f8TfFusSrYLI9BHGJpOQ+BjsBwPebM2vaVM8q+Zw+57M+eHKSy9NqLAwGtSGlydRI6dp2/UxilhXZoPfAFRiowLEJw5q8VvekiQEgJinEn3fmzxHQIDAQAB"
},
"Type": 6
}- 紧接着由client向server发送加密后的AES密钥值
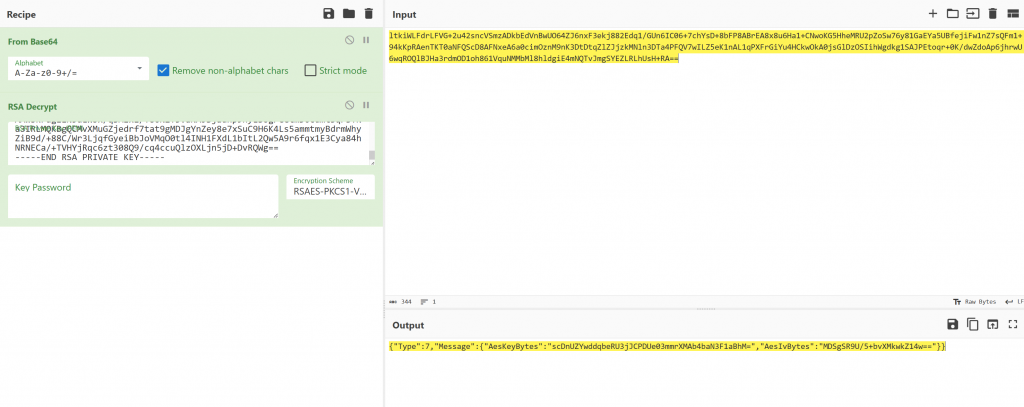
{
"Message": {
"AesIvBytes": "MDSgSR9U/5+bvXMkwkZ14w==",
"AesKeyBytes": "scDnUZYwddqbeRU3jJCPDUe03mmrXMAb4baN3F1aBhM="
},
"Type": 7
}- 使用AES解密后续所有client发往server的流量,其中部分内容为图片,保存后,在某张图中可以得到flag
from pyshark import FileCapture
from Crypto.Cipher import AES
from base64 import b64decode
from gzip import decompress, BadGzipFile
from json import loads
file = FileCapture(
'monitor.pcapng',
display_filter="tcp.dstport == 12346")
tmp = ""
a = 0
for i in file:
try:
getattr(i.tcp, "payload")
except AttributeError as e:
continue
try:
tmp += str(i.tcp.payload).replace(":", "")
if tmp.startswith(b'{"'.hex()) and tmp.endswith(b'}\n'.hex()):
key = b64decode(b"scDnUZYwddqbeRU3jJCPDUe03mmrXMAb4baN3F1aBhM=")
iv = b64decode(b"MDSgSR9U/5+bvXMkwkZ14w==")
data: bytes = b64decode(loads(bytes.fromhex(tmp).decode())["Message"]["EncryptedBytes"].encode())
tmp = ""
aes = AES.new(key, AES.MODE_CFB, iv)
data: dict = loads(decompress(aes.decrypt(data)).decode())
if data.get("Message") and data.get("Message").get("ImageData"):
with open(f"test/{a}.png", "wb") as f:
f.write(b64decode(data.get("Message").get("ImageData")))
print(a)
a += 1
except TypeError as e:
tmp = ""
except BadGzipFile as e:
tmp = ""